➤Summary
The WormGPT AI leak has rapidly become one of the most discussed alleged incidents across underground communities and cybersecurity circles. First posted by the author Sythe on breachforums.bf on 10 February 2026, the claim suggests that a database connected to WormGPT.AI may have been exposed, revealing sensitive user and financial information. According to the forum post, compromised data allegedly includes email addresses, payment details, subscription records, UIDs, and additional metadata that could be exploited by threat actors. This WormGPT AI leak is particularly alarming because WormGPT has been widely associated with misuse scenarios involving automated cybercrime tooling.

While the authenticity of the dataset remains unverified at the time of writing, the implications alone are enough to raise serious concerns among users, researchers, and organizations monitoring the evolving threat landscape. Understanding what was allegedly leaked, how it surfaced, and what actions to take next is critical in minimizing potential damage ⚠️.
Background: Understanding WormGPT and Its Ecosystem
WormGPT emerged as an AI-powered tool frequently discussed in dark web communities for its alleged role in generating malicious content, phishing templates, and exploit assistance. Unlike mainstream AI platforms, WormGPT has been marketed in underground forums as a solution tailored for cybercriminal operations. The WormGPT AI leak draws attention not only because of the data involved but also because it sheds light on the user base interacting with such platforms. Reports from researchers and references shared on cyber threat intelligence platforms indicate that WormGPT-related discussions have spiked over the past year, making any breach involving its infrastructure especially sensitive 🔍. The alleged exposure of subscription and payment data could allow attackers to map identities, track behavior patterns, and correlate users across other breached services.
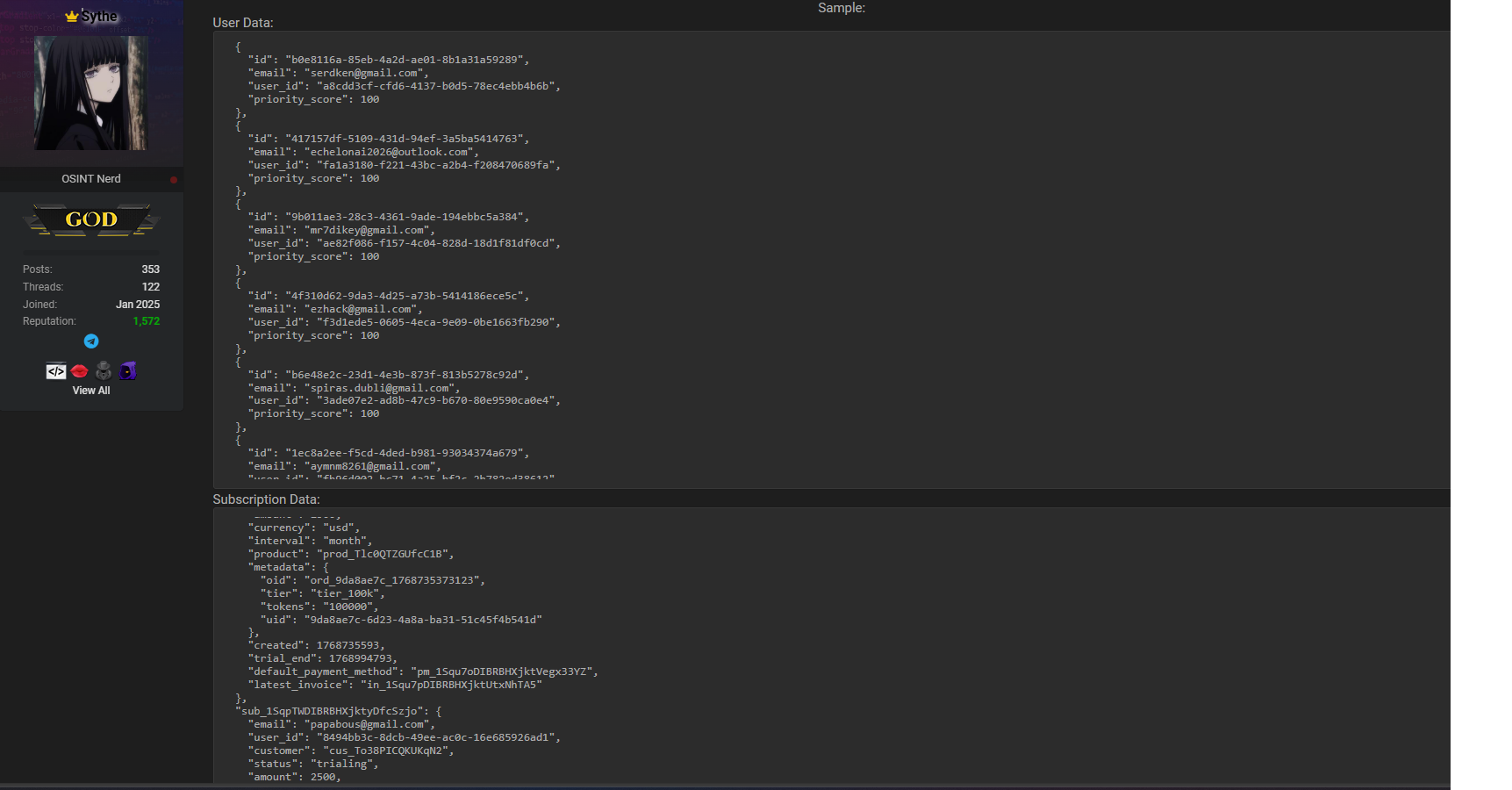
Alleged Details of the WormGPT AI Leak
According to the breachforums.bf post, the leaked dataset is described as a structured database dump. The WormGPT AI leak allegedly contains several categories of sensitive information:
- Registered email addresses tied to WormGPT.AI accounts
- Payment-related data, potentially including transaction identifiers
- Subscription status and history
- Unique user identifiers (UIDs)
- Additional internal fields suggesting account activity
If confirmed, this type of exposure goes beyond simple credential leaks. It could enable targeted scams, account takeovers on reused credentials, and profiling of individuals involved in high-risk online activities 😟. Cyber Threat Analysts monitoring forums have noted that such datasets are often resold, repackaged, or combined with other breaches to increase their value.
Data Sensitivity and Potential Risks
Why does the WormGPT AI leak matter so much? The answer lies in the nature of the data and the context of the platform itself. Email addresses linked to controversial AI tools can be used for doxing, extortion, or social engineering. Payment data, even if partially redacted, can support fraud attempts or identity verification scams. Subscription records may reveal duration of use and engagement levels, which attackers can exploit for personalized phishing. One key question arises: Does an alleged leak automatically mean users are compromised? The clear answer is no, but it significantly raises the risk profile for affected individuals. Even unverified leaks can trigger waves of scam campaigns and opportunistic attacks 🚨.
Verification Status and Community Reactions
As of now, the WormGPT AI leak remains labeled as “alleged.” No official confirmation has been issued by WormGPT.AI operators, and independent verification is ongoing. Security researchers often caution that breachforum posts can range from accurate disclosures to exaggerated or fabricated claims. However, historical patterns show that many high-impact breaches were first revealed in similar forums. Discussions indexed via cyber threat intelligence platforms suggest mixed reactions, with some users claiming sample data appears legitimate while others urge caution. External cybersecurity experts, including those cited by reputable outlets like Krebs on Security, emphasize the importance of treating such leaks seriously until disproven.
Broader Impact on the AI and Cybercrime Landscape
The WormGPT AI leak highlights a broader trend: AI-driven platforms operating in gray or illegal markets face the same, if not greater, security risks as legitimate services. Weak infrastructure, lack of compliance, and adversarial user bases make breaches more likely. From a strategic perspective, leaked data from such platforms can fuel law enforcement investigations and academic research into cybercrime ecosystems 📉. At the same time, it underscores the growing need for proactive malware detection within AI services to prevent abuse and internal compromise. This incident may also accelerate calls for stronger oversight and defensive intelligence capabilities across the industry.
Practical Checklist: What Users and Organizations Should Do
If you suspect your information could be linked to the WormGPT AI leak, consider the following practical steps:
- Change passwords associated with the exposed email immediately
- Avoid clicking unsolicited emails referencing AI tools or subscriptions
- Monitor financial statements for unusual activity
- Use a trusted dark web search to check for data exposure
- Implement a dark web monitoring platform to receive early alerts
- Stay informed through darknetsearch.com – a quality and cheap dark web intelligence platform.
This checklist helps reduce risk even when the breach details are still emerging. Proactive monitoring and awareness remain the most effective defenses in uncertain situations.
Expert Insight and Industry Perspective
A cybersecurity analyst quoted by Wired recently noted, “Underground AI platforms are prime targets for breaches because trust is low and security practices are inconsistent.” This observation aligns closely with the WormGPT AI leak narrative. When platforms prioritize secrecy over security, user data often becomes collateral damage. Industry experts recommend that both individuals and organizations expand their intelligence-gathering capabilities and integrate breach awareness into routine security operations 🔐.
Conclusion: Staying Ahead of Emerging Threats
The alleged WormGPT AI leak serves as a stark reminder of how quickly sensitive information can surface in underground spaces. Whether fully verified or not, the exposure claims underline the importance of vigilance, education, and continuous monitoring. Users linked to controversial platforms face elevated risks, while defenders gain valuable insight into evolving cybercrime infrastructures. Staying informed through trusted resources, adopting proactive security measures, and understanding the implications of such leaks are essential steps forward. Discover much more in our complete guide and Request a demo NOW 🚀
*Disclaimer: DarknetSearch reports on publicly available threat-intelligence sources. Inclusion of an organization in an article does not imply confirmed compromise. All claims are attributed to external sources unless explicitly verified.
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.

