➤Summary
The StMicroelectronics data breach has quickly become one of the most discussed cybersecurity incidents of 2025. First revealed on September 17 by a hacker named Shiney, the compromised database was leaked on the underground forum leakbase.la. The leak was later confirmed by the Kaduu monitoring team, which tracks darknet forums for corporate and government data exposures.
The breach is especially concerning because it doesn’t just expose customer transactions and shipping details—it also reveals internal corporate files linked to semiconductor design, supply chain projects, and even sensitive military-related fields. With the scale and type of data exposed, analysts fear that this incident could trigger ripple effects across industries and government contracts. ⚠️
In this article, we’ll cover the full scope of the leak, its potential impact, and why tools like darknetsearch.com have become a must-have in cybersecurity monitoring.
Proof of the Darknet Leak
The leaked database was posted directly on leakbase.la, one of the more active underground data-trading communities.
📷 [Forum post proof]
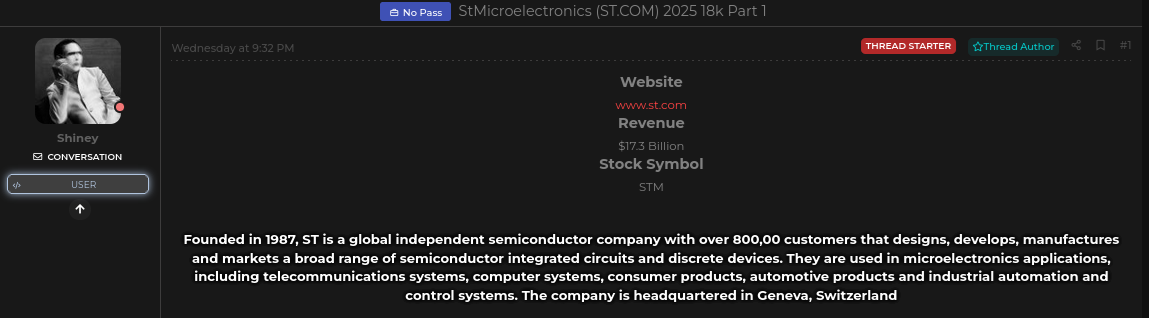
Cybersecurity investigators quickly validated the post, confirming that the database contained both customer-facing data and internal project information. This makes the breach highly valuable to cybercriminals, competitors, and even state-sponsored actors.
What Data Was Exposed?
The scale of the compromised dataset is massive. According to Kaduu’s findings, the following types of records were exposed:
- Order & Transaction Details: Magento Order ID, Mouser Order ID, Order Status, Total Order Value, Promocode Information, Guest Order Flag, Order Creation Date, Item Count
- Customer Identifiers: Full Name, Email Address, Telephone Number, Company Affiliation
- Shipping Data: Recipient Name, Street Address, City, State, Postal Code, Country, Shipping Method, Shipping Cost, and Descriptions
- Product & Project Details: SKUs, Item Names, Pricing, Quantities, Project Titles, Project Descriptions, Applications, End Applications, Design Stage, Estimated Annual Production, Target Production Date
- Military-Specific Field: A dedicated flag indicating whether products are for military use 🚨
- Internal Corporate Files: Engineering documents, R&D communications, and sensitive internal testing status
📂 [Example of exposed internal corporate files]
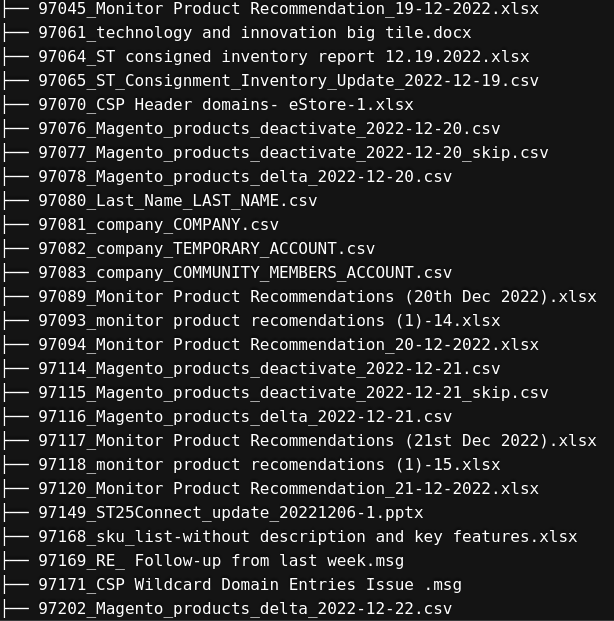
This combination of customer-facing and corporate-sensitive data makes the incident especially dangerous.
Why the StMicroelectronics Data Breach Matters
Semiconductors are not just commercial products—they are the backbone of national defense, telecommunications, and critical infrastructure. The exposure of sensitive project details could:
- Enable corporate espionage, giving competitors insights into proprietary chip designs.
- Create opportunities for supply chain attacks, as threat actors exploit Mouser and Magento transaction data.
- Lead to identity theft and fraud, as cybercriminals weaponize shipping and personal details.
- Endanger defense projects, since some records flag direct military applications.
Industry experts warn that this is not a simple case of credit card theft. Instead, it is a strategic breach with long-term implications.
Expert Insight
A cybersecurity analyst commenting on DailyDarkWeb said:
“This isn’t just about one company. The StMicroelectronics breach demonstrates how intellectual property, supply chain records, and sensitive customer data can converge in a single dataset. That convergence creates a goldmine for attackers.”
This statement reinforces the need for proactive monitoring tools and better supply chain resilience.
The Role of Darknet Monitoring Tools
In today’s digital landscape, darknet monitoring tools are no longer optional—they are essential. The Kaduu team only discovered this breach because they routinely scan underground forums for corporate exposures.
One of the most effective tools in this space is darknetsearch. By indexing hidden forums, marketplaces, and data dumps, it allows security teams to:
- Detect breaches before they become public headlines
- Verify if customer or corporate data is circulating in hacker communities
- Get early-warning intelligence to respond faster
- Protect supply chains by identifying compromised vendor records
💡 Practical Tip: Companies should integrate darknet monitoring into their SOC (Security Operations Center) workflow. Using tools like darknetsearch.com ensures that breaches are detected early, limiting financial and reputational damage.
A Checklist for Companies Affected by Data Breaches
If your company suspects it may be affected by the StMicroelectronics data breach or any similar incident, here’s a quick response checklist:
- 🔐 Isolate systems potentially connected to the breach
- 📢 Notify stakeholders—customers, vendors, and regulators
- 🕵️ Engage forensic experts to assess the scope of exposure
- 💾 Back up and secure uncompromised data
- 🔍 Use darknet monitoring tools like darknetsearch.com to confirm leaked records
- 📑 Document actions for compliance and potential legal defense
This proactive approach not only reduces the damage but also ensures regulatory compliance in regions with strict data protection laws.
FAQ: What Makes This Breach Different?
Q: How is the StMicroelectronics data breach different from other corporate leaks?
A: Most corporate leaks involve either customer data or internal files. This breach is unique because it combines both elements. Customers are exposed through shipping and transactional data, while internal corporate files and even military-related project details are also compromised. This dual exposure significantly increases the risks for both individuals and governments.
Broader Industry Implications
The StMicroelectronics breach isn’t happening in isolation. In recent years, several high-profile semiconductor and electronics firms have also suffered darknet leaks. Each incident highlights the same issue: supply chains remain a critical vulnerability.
For governments, this leak is especially concerning. With semiconductor technology tied to military contracts and critical infrastructure, the potential misuse of this data could have far-reaching consequences. 🌍
How Companies Can Protect Themselves
To reduce exposure, organizations should prioritize:
- Zero Trust Architecture: Reducing reliance on internal perimeter defenses
- Supply Chain Audits: Ensuring vendor and partner security standards are up to date
- Darknet Intelligence: Using darknetsearch.com or similar tools to detect leaks in real-time
- Encryption & Tokenization: Protecting sensitive data fields even if a database is exposed
- Regular Security Drills: Preparing teams to respond quickly and effectively
These steps can significantly reduce the fallout from future breaches.
Conclusion
The StMicroelectronics data breach of September 2025 is a wake-up call. With internal files, customer orders, and even defense-related project data leaked onto darknet forums, the risks extend far beyond typical consumer data exposure.
Organizations must accept that cybersecurity is no longer just about firewalls and antivirus software. Instead, it requires constant monitoring, supply chain visibility, and darknet intelligence tools to stay ahead of attackers.
As threats evolve, the importance of platforms like darknetsearch.com cannot be overstated. Companies that fail to monitor the dark web are essentially flying blind in an environment where leaks can appear overnight.
👉 Discover much more in our complete guide
👉 Request a demo NOW
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.

