➤Summary
Introduction
The PKB Indonesia leaked database has sparked urgent discussions in cybersecurity and politics across Southeast Asia. On September 12, 2025, a hacker known as TERRORISM666 claimed responsibility for releasing what he described as the internal database of the Partai Kebangkitan Bangsa (PKB) on the Darkforums.st darknet forum. This incident, still under investigation, raises alarms about cybercrime, political vulnerability, and the protection of sensitive data in Indonesia. ⚠️
At the center of the controversy is the alleged leak of thousands of personal records, party communications, and identification details. While independent experts have yet to verify the authenticity of the data, the potential impact is massive: from exposing private identities to shaking public trust in one of Indonesia’s key political parties.
The Leak and Its Source
According to underground posts, the PKB Indonesia leaked database was uploaded on Darkforums.st, a well-known darknet forum for trading stolen data and hacking tools. The threat actor TERRORISM666 presented himself as the source, boasting about breaching PKB’s systems. Claims suggest the database includes:
- Full names and contact details of party members
- National Identification Numbers (NIK)
- Internal communications and strategy documents
- Potentially financial and electoral records
🔗 External report: H4ckmanac post on X confirms that the claim has been circulating in cybersecurity monitoring communities.
Proof of Leak 📸
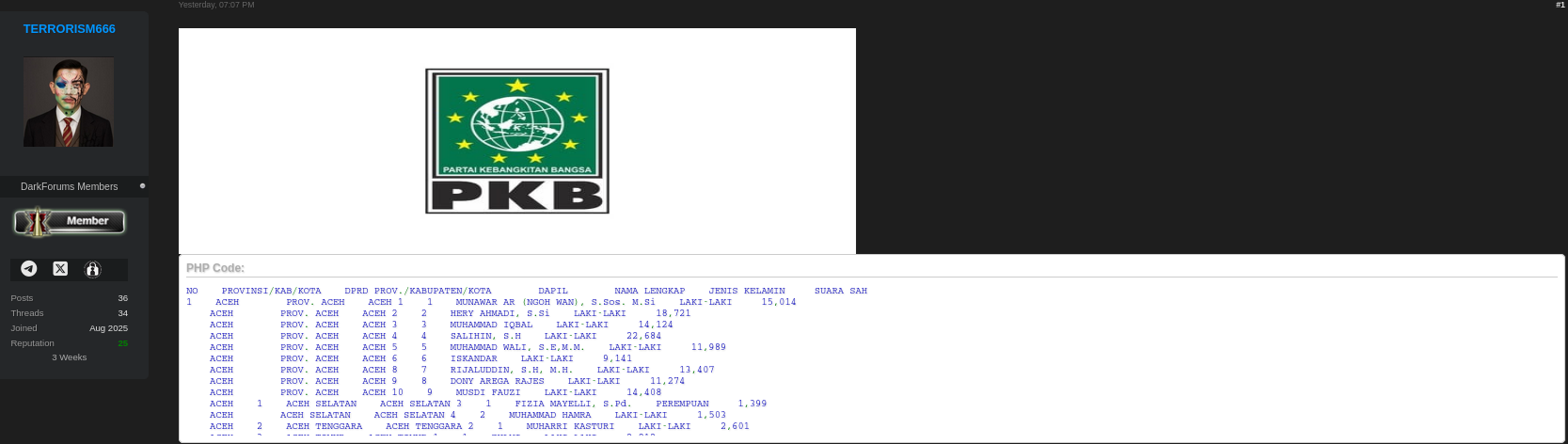
This screenshot is crucial evidence, as visual proof often distinguishes between credible leaks and exaggerated hacker claims. Without it, the authenticity remains speculative.
Why PKB Matters in Indonesian Politics
The Partai Kebangkitan Bangsa (PKB) is a major player in Indonesian politics, with deep roots in the Nahdlatul Ulama community. A breach targeting PKB is not just a technical failure but also a political vulnerability. Exposure of sensitive data could:
- Damage voter trust ahead of elections
- Undermine PKB’s internal cohesion
- Be exploited by political rivals or malicious actors
- Trigger investigations into compliance with Indonesia’s Personal Data Protection Law (UU PDP)
Hacker Profile: Who is “TERRORISM666”?
The alias TERRORISM666 has appeared sporadically on darknet platforms over the past year, often linked with political leaks and ideological cyber attacks. While motives are unclear, the pattern suggests a combination of:
- Reputation building among peers in the hacking community
- Political disruption by undermining institutions
- Financial gain, if the dataset is offered for sale privately
💡 Practical tip: Always treat aliases in the darknet ecosystem as fluid. Hackers change handles often, either to evade detection or to rebrand themselves for credibility.
Risks and Consequences of the Leak
If authentic, the PKB Indonesia leaked database carries significant risks:
- Identity Theft: Members’ personal data can be exploited for fraud.
- Phishing Attacks: Hackers may use verified contact details to launch targeted campaigns.
- Political Sabotage: Internal communications could be weaponized to discredit PKB.
- National Security Concerns: Leaks of political databases may be exploited by foreign intelligence.
🚨 Checklist for political organizations to minimize risks:
- ✅ Encrypt sensitive files at rest and in transit
- ✅ Enforce strict access controls
- ✅ Regularly audit servers for vulnerabilities
- ✅ Train staff on phishing awareness
- ✅ Employ darknet monitoring solutions
How Darknet Forums Amplify Threats
The Darknet forum ecosystem, including Darkforums.st, acts as a marketplace and stage for cybercriminals. By posting the PKB dataset there, the hacker ensured maximum visibility in the underground scene. Key features of such forums include:
- Encrypted communications for anonymity
- A reputation system where hackers earn credibility by sharing or selling leaks
- Forums that act as archives, making leaked data retrievable long after publication
This makes the PKB case particularly alarming because once data circulates on the darknet, complete removal becomes almost impossible. 🕵️
Expert Insights
“The PKB leak, whether exaggerated or real, highlights the urgent need for proactive darknet intelligence. Waiting until data surfaces in public media is too late. Organizations must detect exposure at its earliest stage.”
— Cyber Analyst, darknetsearch.com
Our team at darknetsearch.com specializes in detecting such leaks at the earliest signals. By monitoring hidden communities like Darkforums.st, we provide clients with early-warning alerts, reducing potential damage.
Practical Tip for Individuals
If you suspect your data might be in the PKB Indonesia leaked database, take immediate action:
- Change all associated passwords 🔑
- Activate two-factor authentication
- Monitor financial accounts for unusual activity
- Be alert for phishing emails or messages pretending to be from PKB
For clarity, here’s what we know in structured format:
| Aspect | Details |
| Hacker Alias | TERRORISM666 |
| Platform | Darkforums.st (Darknet forum) |
| Date | 12 September 2025 |
| Target | Partai Kebangkitan Bangsa (PKB), Indonesia |
| Alleged Data | Member lists, NIKs, emails, internal docs |
| Verification | Pending; no forensic confirmation yet |
The Bigger Picture: Cyber Attacks on Politics
The PKB data breach on Darkforums.st is not an isolated case. Around the world, political parties have been prime targets for hackers. Common motivations include:
- Influencing electoral processes
- Damaging reputations of rival groups
- Selling high-value political intelligence
- Demonstrating hacking skills for notoriety
Indonesia, with its growing digital infrastructure and complex political landscape, has become a frequent target of cyber attacks in recent years.
Conclusion
The PKB Indonesia leaked database incident is a wake-up call 🚨 for political parties, government agencies, and organizations handling sensitive data. While the leak’s authenticity is not yet fully confirmed, the very claim highlights how exposed political institutions are to darknet threats.
Proactive monitoring through platforms like darknetsearch.com offers a crucial defense. The ability to identify leaks before they spread widely can mean the difference between minor damage and a full-scale crisis.
👉 Discover much more in our complete guide
👉 Request a demo NOW
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.

