The new META malware, a new stealer malware appears to be rising in popularity among cybercriminals. Darknet users advertise new malware as an “improved RedLine” version. RedLine has been known for stealing user information, such as browser-saved credentials, browser history, credit cards, cryptocurrency wallet access, cookies, desktop files, gaming credentials and desktop screenshots among other information.
The tool is sold at $125 for monthly subscribers or $1,000 for unlimited lifetime use and is promoted as an improved version of RedLine.
The Bleeping Computer has first reported of the Meta malware launch last month. Ever since we were able to gather more information on malware, including the attack vector and the scheme of spreading it.
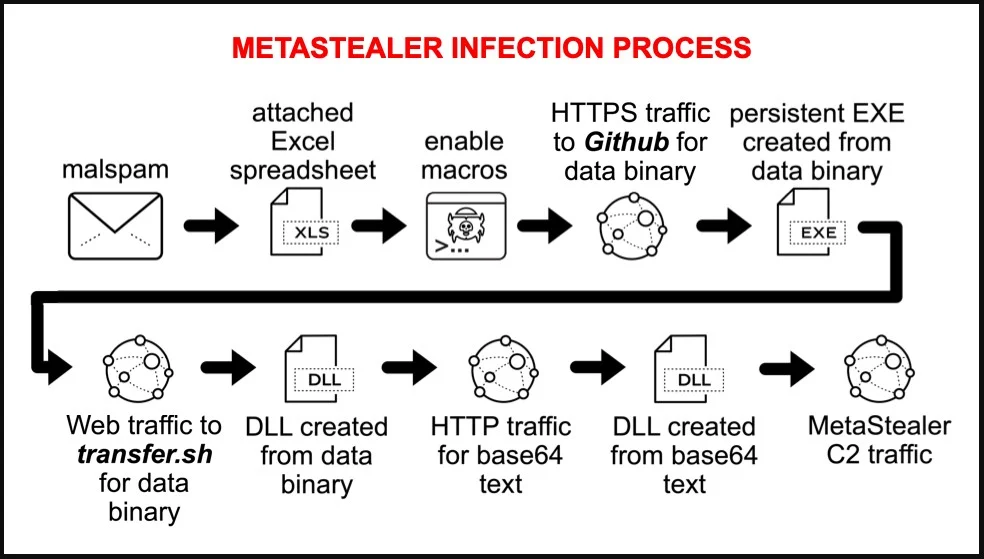
The infection chain in the particular campaign follows the “standard” approach of a macro-laced Excel spreadsheet arriving in prospective victims’ inboxes as email attachments.
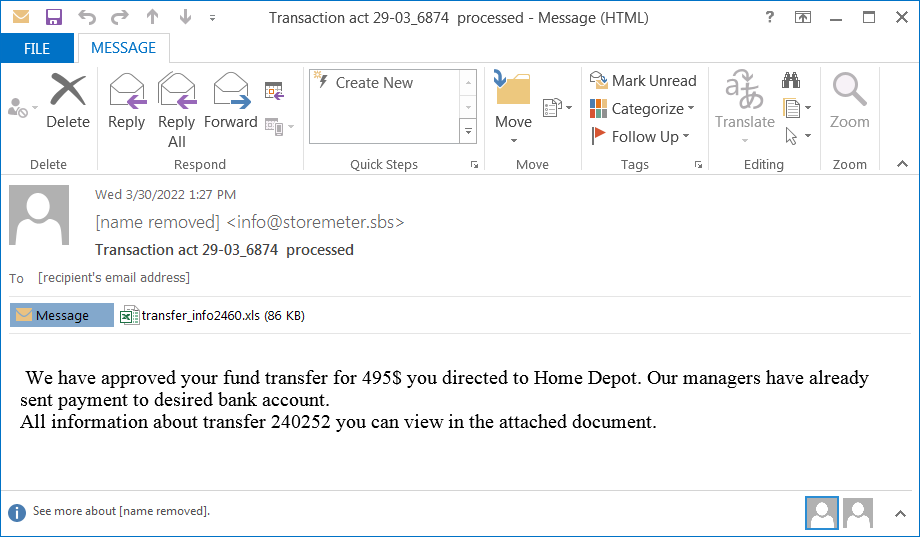
The messages make bogus claims of fund transfers that are not particularly convincing or well-crafted but can still be effective against a significant percentage of recipients.
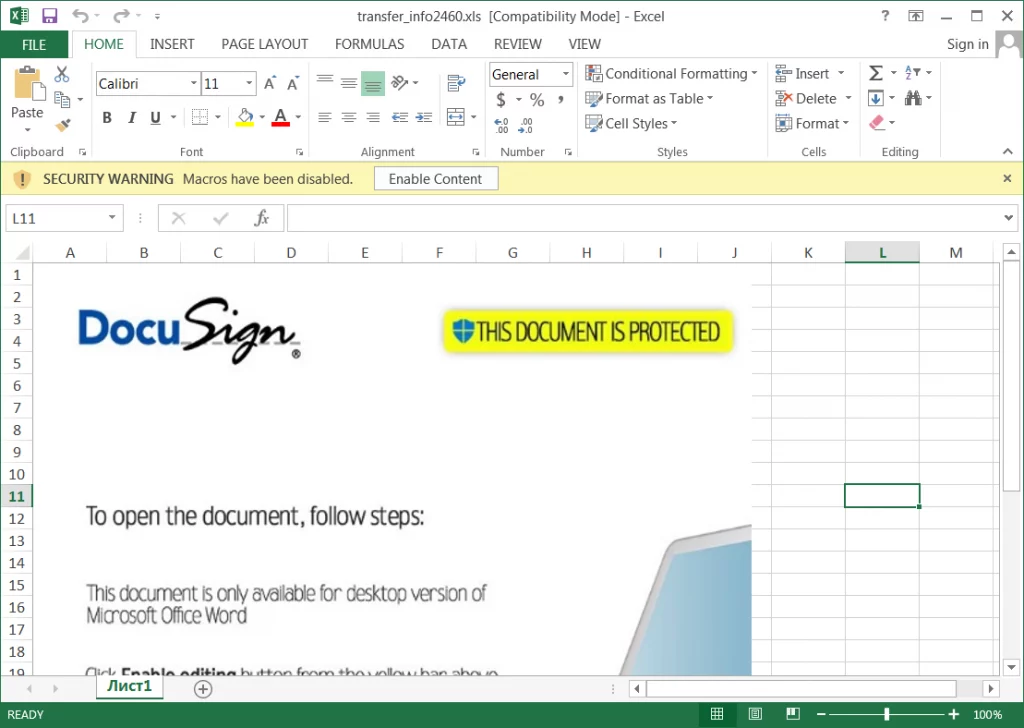
The spreadsheet files feature a DocuSign lure that urges the target to “enable content” required to run the malicious VBS macro in the background.
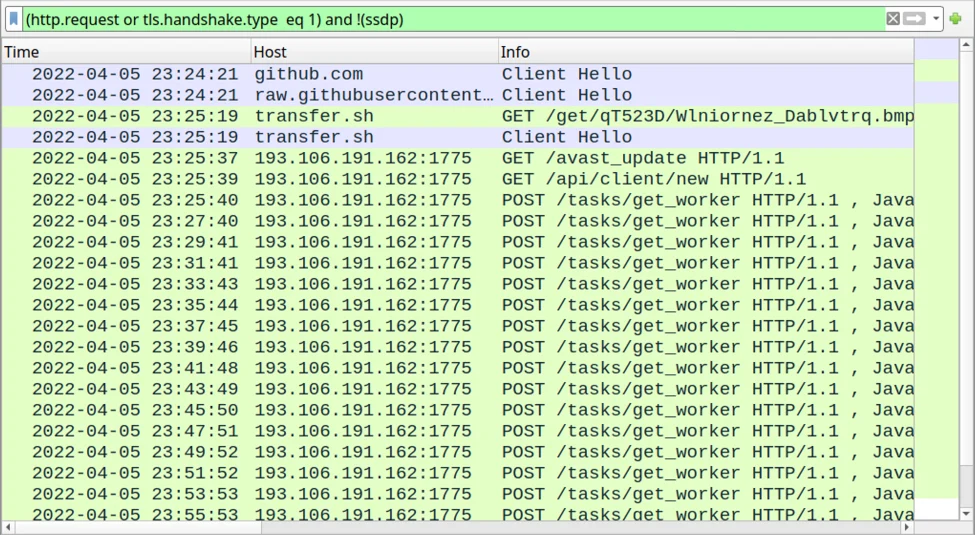
When the malicious script runs, it will download various payloads, including DLLs and executables, from multiple sites, such as GitHub.
Some of the downloaded files are base64 encoded or have their bytes reversed to bypass detection by security software. Eventually, the final payload is assembled on the machine under the name “qwveqwveqw.exe,” which is likely random, and a new registry key is added for persistence.
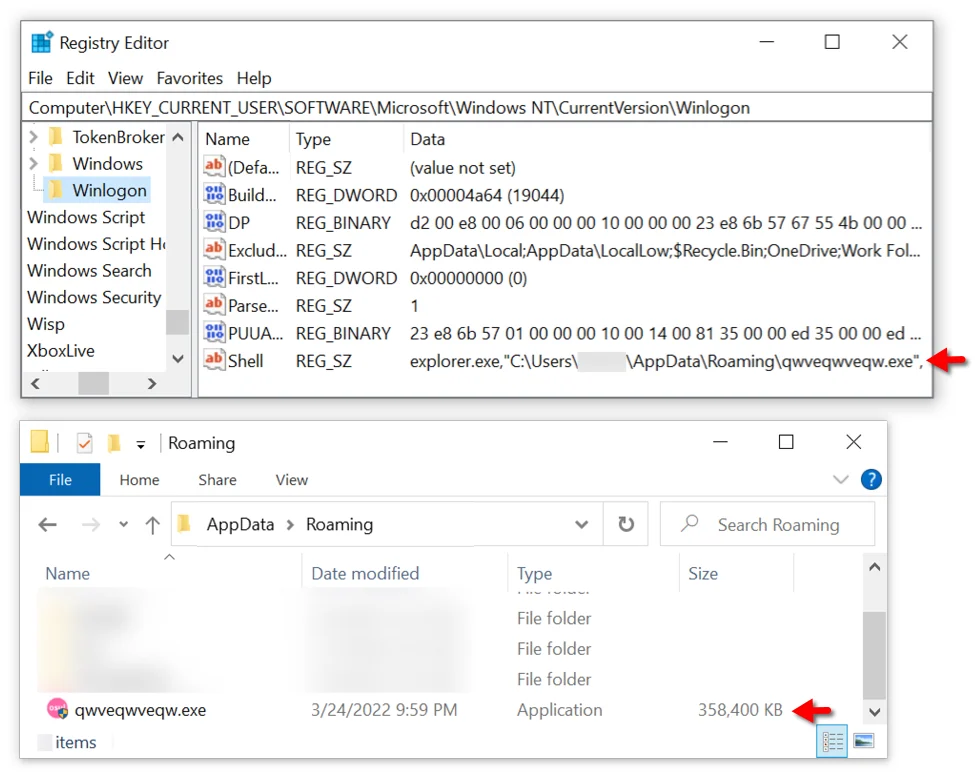
A clear and persistent sign of the infection is the EXE file generating traffic to a command and control server at 193.106.191[.]162, even after the system reboots, restarting the infection process on the compromised machine.
Malware like this is not an exception, there are hundreds of derivatives of stealer malware, starting with Azorult, RedLine, Predator and so on. Cyber criminals develop more and more sophisticated examples that are not detected by antivirus programs. We recommend users to pay attention to email that come to your inbox, beware of Macros attacks and stay cyber secured!
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.
