➤Summary
Leaked Database of Medan State University has surfaced on a well-known cybercrime forum, raising serious concerns about student data security in Indonesia’s higher education sector. The incident involves a massive SQL database allegedly belonging to Medan State University, shared by a threat actor on BreachForums. 😟 According to underground posts and third-party monitoring reports, the leak contains detailed student identification records, putting thousands at potential risk of misuse. This Leaked Database of Medan State University case highlights how academic institutions remain attractive targets for cybercriminals seeking large volumes of structured personal data.
What Happened in the Medan State University Data Breach
The Leaked Database of Medan State University was reportedly published on BreachForums.bf by a user known as “anim3” on 03 February 2026. The dataset, shared in .sql format, is approximately 948.9 MB in size, indicating a full or near-full database extraction. 🧩 Earlier references to the same incident appeared on HackNotice on 23 January 2026, suggesting the breach may have occurred weeks before public disclosure. This Medan State University data breach reflects a growing pattern where educational databases are traded in underground communities before institutions can respond.
Forum Details and Threat Actor Activity
The database was advertised on BreachForums, a notorious hub for leaked databases and stolen credentials.

In the context of the Leaked Database of Medan State University, forum users reportedly discussed the completeness of the dataset and its potential resale value. Darknetsearch.com platforms such as frequently track such activity to identify early warning signs of data exposure and secondary distribution.
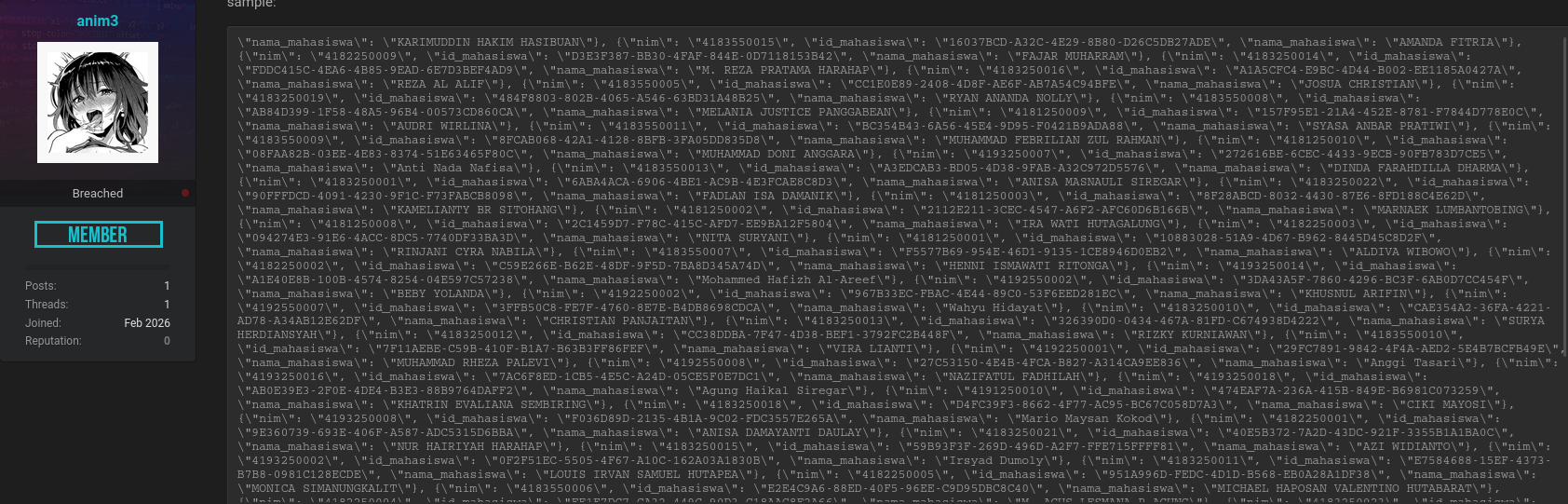
What Data Was Compromised
According to the forum post and supporting reports, the compromised database contains sensitive student information. The exposed fields reportedly include:
- nim – Student identification number
- id_mahasiswa – Unique internal student ID (UUID)
- nama_mahasiswa – Full name of the student
This type of structured personal data is particularly valuable for identity correlation and social engineering attacks. 📂 The Leaked Database of Medan State University does not appear to include financial records, but even basic identifiers can be abused when combined with other breached datasets.
Scope and Potential Impact on Students
While the exact number of affected students has not been officially confirmed, the size of the SQL file suggests a large population. The Leaked Database of Medan State University could impact current students, alumni, and possibly applicants. 🎓 Risks include identity misuse, targeted phishing, and impersonation attempts. A common question is: Does this leak directly enable financial fraud? The clear answer is that while no banking data is mentioned, personal identifiers can still facilitate fraud when cross-referenced with other leaks.
Timeline of Disclosure and Public Reporting
Understanding the timeline is critical in breach analysis. The Medan State University database was first referenced publicly by HackNotice on 23 January 2026, based on underground monitoring. 🗓️ The BreachForums post followed on 03 February 2026, making the Leaked Database of Medan State University widely visible to threat actors. This gap highlights how data can circulate quietly before gaining broader attention, limiting response time for affected institutions.
Why Universities Are Prime Targets
Educational institutions often manage vast amounts of personal data while operating with limited cybersecurity budgets. The Leaked Database of Medan State University underscores systemic challenges such as legacy systems, inconsistent patching, and decentralized IT environments. 🧠 Universities also value openness and collaboration, which can unintentionally expand attack surfaces. Similar cases tracked on https://darknetsearch.com/ show that higher education breaches are frequently exploited for long-term data harvesting rather than immediate monetization.
Practical Checklist for Affected Individuals
If you believe your data may be part of the Leaked Database of Medan State University, consider the following steps ✅:
- Be cautious of unsolicited emails or messages referencing your student status
- Avoid sharing identification numbers or personal details online
- Monitor accounts for unusual activity, even if no financial data was leaked
- Stay informed through trusted breach notification platforms
These actions reduce the likelihood of follow-up attacks stemming from exposed academic records.
Institutional Lessons and Security Gaps
From a defensive standpoint, the Leaked Database of Medan State University highlights the importance of database access controls, regular audits, and incident response planning. 🔐 Educational organizations should prioritize encryption of stored data and strict segmentation of student information systems. Proactive monitoring of underground forums can help detect early signs of compromise before large-scale exposure occurs.
Expert Insight on Academic Data Leaks
Security analysts often warn that student databases are “low-hanging fruit” for attackers. One researcher quoted in breach analysis reports noted that academic records are “timeless identifiers that retain value for years.” 📊 This observation directly applies to the Leaked Database of Medan State University, where even basic fields can remain exploitable long after graduation. Such incidents reinforce the need for sustained investment in academic cybersecurity.
External Confirmation and Reporting
Additional details about this breach were documented by HackNotice, a platform known for tracking leaked databases and exposed credentials. Their report provides context on the dataset and its underground circulation, adding credibility to the claims. 🌐 You can review their coverage via the external reference at HackNotice, which aligns with broader observations from dark web intelligence communities.
Conclusion: Why This Leak Matters Beyond One University
The Leaked Database of Medan State University is not an isolated event—it reflects a broader trend of academic data exposure worldwide. As student records continue to surface in underground forums, the long-term implications for privacy and trust in educational institutions grow more severe. 🚨 Staying informed, adopting proactive monitoring, and strengthening institutional defenses are essential steps forward. Discover much more in our complete guide. Request a demo NOW.
*Disclaimer: DarknetSearch reports on publicly available threat-intelligence sources. Inclusion of an organization in an article does not imply confirmed compromise. All claims are attributed to external sources unless explicitly verified.
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.

