➤Summary
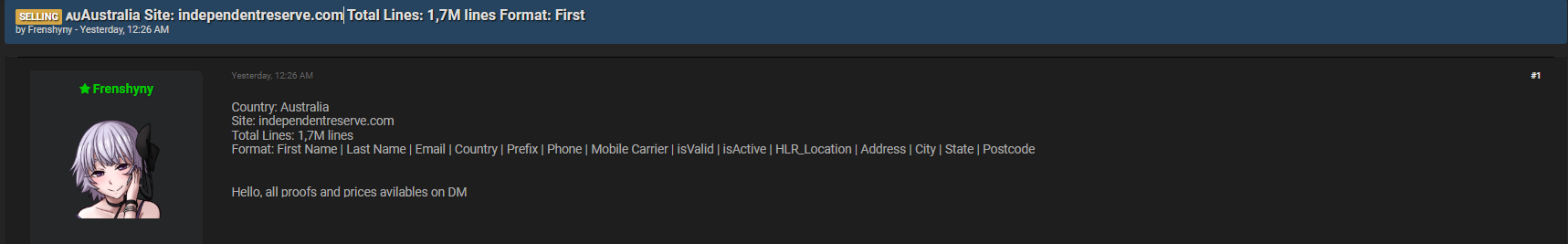
The Independent Reserve data breach allegedly posted on Darkforums.st has drawn global attention, particularly among security practitioners and professionals in the Finance industry. On December 10, 2025, a forum member known as Frenshyny claimed to be selling a dataset containing 1.7 million customer records—making the incident a highly relevant case study dark web monitoring analysis for cybersecurity researchers and risk teams. ⚠️
Although the authenticity of the stolen database has not been officially confirmed, the presence of such a listing underscores ongoing risks to financial platforms, cryptocurrency exchanges, and digital-asset service providers.
Understanding the Alleged Dark Web Listing
According to the forum post, the dataset—presented as originating from the Independent Reserve data breach—was allegedly offered for sale with 1.7M lines of customer information. The seller described the format as:
First Name | Last Name | Email | Country | Prefix | Phone | Mobile Carrier | isValid | isActive | HLR_Location | Address | City | State | Postcode
Such structured, enriched personal data can be extremely valuable to threat actors. It enables large-scale phishing campaigns, social engineering, SIM-swap attempts, identity theft, and account takeover attacks.
A listing of this size also raises urgent questions for security practitioners:
How was such a large volume of data accessed?
In most cyber incidents involving cryptocurrency exchanges or financial entities, attackers typically target misconfigured databases, leaked API keys, outdated authentication systems, or vulnerable third-party integrations. This suspected breach highlights why the Finance industry continues to be one of the most attractive and profitable targets for cybercriminals. 💼
Why This Incident Is Important for the Finance Industry
The Finance industry operates within one of the most heavily regulated sectors in the world. When a potential leak emerges—even before confirmation—it can trigger legal obligations, reputational consequences, and immediate customer trust issues.
Three factors amplify the importance of this alleged Independent Reserve data breach:
- Cryptocurrency exchanges process sensitive data similar to banks, making them prime targets.
- User trust is central to adoption—one data exposure can severely impact a platform’s credibility.
- Regulations mandate rapid response, including notifications, internal investigations, and risk assessments.
Even an unconfirmed listing could force organizations to deploy internal audits, engage digital forensics, and update public communications. For the broader Finance sector, this serves as a timely reminder of the rising sophistication of threat actors and the value of proactive dark-web surveillance. 🔍
Key Findings From the Alleged Independent Reserve Data Breach
Below is a quick, user-friendly breakdown suitable for featured snippets:
Table: Key Details of the Alleged Listing
| Item | Details |
| Forum | Darkforums.st |
| Seller | “Frenshyny” |
| Listing Date | 10 December 2025 |
| Total Records | 1.7 million |
| Data Types | Personal info, phone details, HLR lookup data, address fields |
| Industry Impacted | Finance industry |
| Risk Level | High if authentic |
How Security Practitioners Should React to Dark Web Claims
For security practitioners, the alleged Independent Reserve data breach is a valuable case study dark web monitoring scenario. To manage similar incidents effectively, organizations should follow a structured response.
Quick Checklist for Teams
- Monitor dark-web sources continuously (using automated crawlers + human validation).
- Cross-reference leaked emails with known compromised databases.
- Validate data samples without interacting with illicit marketplaces.
- Assess the breach scope internally by checking access logs and unusual system activity.
- Prepare user notifications if regulatory thresholds are met.
- Engage legal counsel familiar with finance-sector compliance.
This approach reduces the window of opportunity for attackers and strengthens long-term resilience.
Could the Data Be Authentic? A Critical Examination
Many readers ask:
“How do experts determine if a leaked dataset is real?”
Here is the answer:
Cybersecurity analysts use a combination of techniques such as metadata examination, cross-leak comparison, OSINT sources, and synthetic user testing to estimate authenticity. Even without purchasing illegal data, partial samples often reveal enough clues—like formatting consistency or domain-specific patterns—to identify whether the leak aligns with genuine customer data.
Yet, until the company provides disclosure, incidents like this remain unverified. Nevertheless, this process is standard—and vital—in the Finance industry, where false claims can still generate panic.
Risk Implications for Users and Organizations
If the alleged Independent Reserve data breach were confirmed, the exposure of detailed personal and phone-related information would increase risk levels dramatically.
Potential consequences include:
- More sophisticated phishing attacks targeting verified emails and phone numbers
- Increased SIM-swapping risk because of mobile carrier and prefix data
- Financial fraud attempts, especially involving crypto wallets
- Identity-based attacks against high-value users
- Long-term profile building by threat actors
At an industry level, such an incident reinforces why cryptocurrency platforms must invest in continuous monitoring, strong encryption, improved authentication, and detailed employee training.
Practical Tips to Reduce Exposure After a Suspected Data Leak
To protect users and organizations from fallout associated with any cyber incident—confirmed or not—follow these practical recommendations:
- Enable multi-factor authentication (MFA) on all accounts
- Reset passwords immediately if you suspect reuse across platforms
- Use strong, unique passphrases rather than short passwords
- Beware of unsolicited emails or SMS messages, especially those referencing account recovery
- Audit permissions on crypto platforms, exchanges, and connected apps
Small steps significantly reduce risk and help individuals respond effectively to potential data exposure. 🔐
A Closer Look at the Finance Industry’s Growing Threat Landscape
Across the global Finance industry, threat actors continue evolving. Cryptocurrency exchanges—like the one allegedly affected—face even greater risks compared to traditional banks due to the irreversible nature of blockchain transactions.
This alleged Independent Reserve data breach illustrates broader patterns such as:
- Increased targeting of digital-asset companies
- Use of dark-web marketplaces to monetize data
- Rise of data-enrichment techniques (e.g., HLR lookups)
- Greater sophistication in social-engineering campaigns
As cyberattacks escalate, financial platforms must adopt modern, intelligence-driven defense models that prioritize user privacy and infrastructure resilience. 🔒
Conclusion: Why This 2025 Breach Warning Should Not Be Ignored
The alleged Independent Reserve data breach presented on Darkforums.st may still be undergoing verification, but its impact on the cybersecurity narrative is undeniable. For security practitioners, regulators, and professionals in the Finance industry, this event serves as a powerful reminder: dark-web intelligence, proactive monitoring, and rapid response are no longer optional—they are mission-critical.
To stay protected, organizations must deploy modern monitoring solutions, enhance incident handling procedures, and ensure transparent communication when potential risks emerge.
If you want to continue strengthening your cybersecurity posture:
👉 Discover much more in our complete guide
👉 Request a demo NOW
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.

