➤Summary
In a shocking revelation, cybersecurity researchers from the Kaduu Team have discovered a massive haamor.com data breach 🧠 — a Thai healthcare website known for providing medical advice and online consultations. The breach was first uncovered during a dark web monitoring sweep and later found posted publicly on the underground forum darkforums.st by a user going by the alias RainbowDF on 08 November 2025. According to early reports, the health-site database leak could include sensitive user data, login credentials, and possibly medical-related details.
This article will break down what is known about the haamor.com data breach, what data is believed to be compromised, and most importantly — what you can do to protect yourself. With health-related information becoming a prime target for hackers, this case highlights the urgent need for improved cybersecurity hygiene 🧩 and awareness across online healthcare platforms.
The haamor.com data breach: what happened?
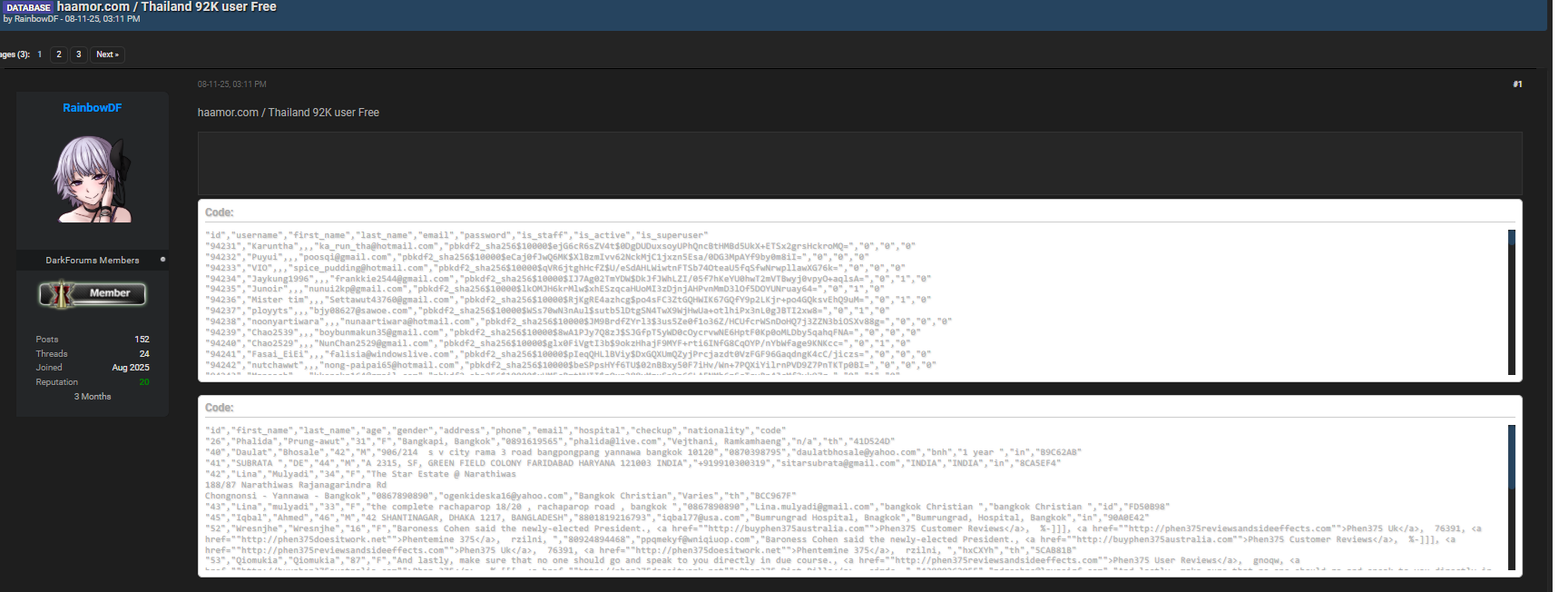
The haamor.com data breach was discovered after the Kaduu Team detected unusual chatter on several dark web forums. Their analysts routinely monitor underground spaces to identify early warnings of leaks, stolen databases, and compromised credentials. During one such scan, they identified a new thread titled “haamor.com full database dump”, posted on darkforums.st by RainbowDF.
The forum post claimed to contain thousands of user records from the haamor.com platform, including usernames, emails, encrypted passwords, and in some cases, limited health-related information submitted during consultations.
“This breach underscores how even trusted health portals can become a vector for privacy compromise if security updates and encryption protocols are not properly maintained,” said a Kaduu spokesperson.
Below is the forum post reference for verification 👇
Forum post proof
Forum: darkforums.st
Author: RainbowDF
Leaked published date: 08 November 2025
What kind of data may have been exposed?
The leaked dataset allegedly contains several data fields associated with haamor.com user accounts. Although not all of the data has been verified, early indications suggest it may include the following types of information:
- Full names and usernames 🧾
- Registered email addresses
- Encrypted passwords (likely hashed with bcrypt or MD5)
- Account creation timestamps
- User activity logs
- Possible health consultation notes or medical condition tags
If verified, this information could give cybercriminals a starting point for targeted phishing attacks, password spraying, or identity fraud attempts.
Why this breach matters 🧨
While social media breaches are common, health-site database leaks are particularly concerning because they involve personal and medical data. Medical information carries high resale value on the dark web, as it can be used for insurance fraud or even blackmail.
For haamor.com, a popular health platform in Thailand, this incident represents a significant loss of user trust. For individuals, it poses real-world risks — from financial scams to emotional distress if sensitive information becomes public.
Even if the passwords were encrypted, poorly implemented hashing or reused credentials can lead to further exposure. Hackers often test breached credentials on other websites — a practice called credential stuffing.
How the Kaduu Team uncovered the leak
The Kaduu Team, known for its proactive dark web intelligence work, discovered the haamor.com data breach as part of its automated monitoring pipeline. Their system continuously scans thousands of dark web threads and marketplaces for signs of newly posted data. When their algorithms detected keywords linked to haamor.com, analysts manually verified the dataset and confirmed its authenticity.
They immediately flagged the case and notified relevant security channels. This type of discovery is crucial because early detection can limit damage by prompting affected organizations to reset credentials, patch vulnerabilities, and warn users.
You can explore more verified breach reports on DarknetSearch, a leading portal for verified dark web data exposure reports.
What users should do now ✅ (Practical Tip Section)
If you’ve ever registered an account on haamor.com, assume your information may have been compromised. Here’s a practical checklist you can follow right now:
- 🔑 Change your password immediately — not just on haamor.com, but on any other account using the same password.
- 🧱 Enable two-factor authentication (2FA) wherever possible.
- 📧 Be alert for phishing emails pretending to come from healthcare services or “support teams.”
- 💳 Monitor your accounts for unauthorized activity or credit card misuse.
- 🔍 Check if your email appears in breach databases such as HaveIBeenPwned — a reputable external source with a DA above 90.
- 🧮 Avoid oversharing health data online until you are confident the website has enhanced its security.
- 🧰 Keep your browser and antivirus updated to block malicious scripts or credential-stealing malware.
These simple steps can drastically reduce your exposure to the fallout of the haamor.com data breach.
Could this have been prevented?
Absolutely. Most data breaches stem from simple oversights such as:
- Unpatched software vulnerabilities
- Weak administrator credentials
- Insecure database backups
- Insufficient encryption on stored data
- Misconfigured servers
Implementing regular penetration testing, timely software updates, and encrypted data storage could have prevented or mitigated the health-site database leak. Organizations must treat user data — especially health-related data — with the highest level of security.
As one cybersecurity analyst put it:
“Healthcare platforms often underestimate their attractiveness to attackers. Every health record is a goldmine for identity thieves.”
Frequently asked question 💬
Q: How do I know if my haamor.com account is affected?
A: At the moment, haamor.com has not released an official statement confirming the breach. However, since the database has been found circulating on dark forums, it is safe to assume that any registered user could be affected. You can stay updated by monitoring reports on DarknetSearch and following reputable cybersecurity outlets.
Long-term consequences for haamor.com users
The haamor.com data breach not only impacts users directly but also affects the wider digital health ecosystem in Thailand. Breaches like these can:
- Damage trust between patients and online health providers
- Invite scrutiny from regulators or data-protection authorities
- Lead to financial penalties under privacy laws
- Cause operational disruption during investigations
For users, the long-tail impact could be more subtle — identity misuse, spam campaigns, or targeted phishing that continues for months after the leak.
Conclusion 🚨
The haamor.com data breach serves as a serious reminder that even trusted healthcare portals are vulnerable to cyber threats. With personal and potentially medical data exposed, every affected individual should act swiftly to secure their information.
Stay proactive: update your passwords, enable MFA, and follow the checklist provided above. You can track ongoing breach updates and verify exposure reports on DarknetSearch, your reliable resource for dark web intelligence.
🧭 Discover much more in our complete guide to dark web data monitoring.
🚀 Request a demo NOW and learn how to safeguard your organization against the next cyber threat.
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.

