➤Summary
Dark Web Monitoring has become a critical cybersecurity priority as reports of alleged data leaks continue to surface across underground forums. In January 2026, a post published on Darkforums.st by a user known as TANAKA claimed the release of sensitive Bumble.com-related data, drawing renewed attention to how exposed information circulates beyond the surface web. While such disclosures must always be treated with caution and verified through professional analysis, the situation highlights why organizations and users alike need visibility into dark web activity to understand potential exposure and respond effectively 🚨
Overview of the Alleged Bumble.com Data Leak
According to the forum post on Darkforums.st, the leak was reportedly released on January 28, 2026, and attributed to author TANAKA. The content allegedly referenced a wide range of compromised data types, including genders, hobbies, addresses, feedbacks, ebooks, contracts, stories, videos, agreements, management reports, invoices, transactions, and internal documents. Claims of this scale, whether fully accurate or partially exaggerated, demonstrate how threat actors bundle diverse datasets to increase perceived value and attention on underground markets 🧠
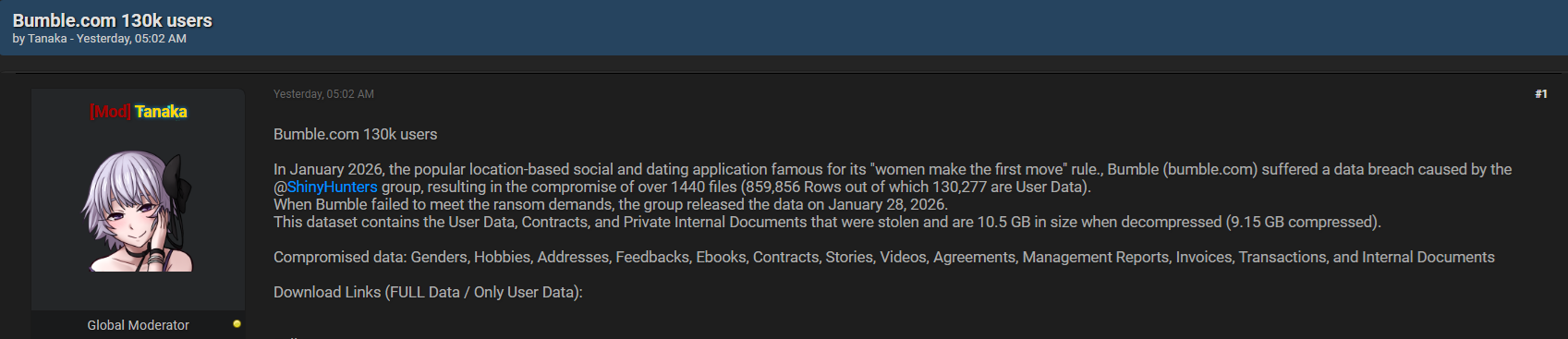
It is important to emphasize that dark web claims should always be considered alleged until validated by trusted cybersecurity investigations or official disclosures.
Why Dark Web Monitoring Matters for Dating Platforms
Dark Web Monitoring plays a vital role for platforms handling large volumes of personal and behavioral data. Dating services like Bumble.com store profile attributes, user-generated content, and transactional information, making them attractive targets for cybercriminals seeking to monetize trust and intimacy-based data 💔
By continuously scanning hidden forums, marketplaces, and paste sites, monitoring teams can detect early indicators of compromise, leaked credentials, or internal documents before damage escalates. This proactive approach reduces dwell time and supports faster incident response.
Types of Data Allegedly Compromised and Their Risks
The dataset described on Darkforums.st included both personal and corporate-level information. The table below summarizes potential risks associated with each category, helping security teams prioritize response actions.
| Data Type | Potential Risk |
| Genders and Hobbies | Profiling, targeted phishing, social engineering |
| Addresses | Identity theft, stalking, physical security risks |
| Feedbacks and Stories | Reputation damage, blackmail attempts |
| Contracts and Agreements | Legal exposure, competitive intelligence loss |
| Management Reports | Strategic insight for competitors or attackers |
| Invoices and Transactions | Financial fraud, account takeover |
| Videos and Internal Documents | Extortion, compliance violations |
Such breadth underscores why dark web monitoring reports are essential for understanding not just whether data is exposed, but how it could be misused downstream 📊
How Dark Web Monitoring Reports Support Incident Response
Dark Web Monitoring reports consolidate findings from multiple hidden sources into actionable intelligence. These reports typically include indicators such as sample data, timestamps, forum credibility, and spread velocity. For security teams, this context answers a crucial question: Is the threat real and actionable?
Yes, when properly validated, these insights allow organizations to initiate credential resets, notify affected users, and engage legal or regulatory stakeholders early, reducing long-term fallout.
The Role of a Dark Web Solution in Risk Mitigation
A comprehensive dark web solution goes beyond keyword searches. It combines automated crawling, human analyst validation, and correlation with existing security logs. This layered approach helps distinguish recycled data dumps from newly exposed material and reduces false positives that often overwhelm teams ⚙️
For consumer-facing platforms, integrating monitoring outputs into SIEM or SOAR workflows ensures alerts translate into measurable action rather than static reports.
Dark Web Monitoring for MSSP and Enterprise Teams
Dark Web Monitoring for MSSP providers has become a differentiator in managed security offerings. By delivering continuous visibility into underground ecosystems, MSSPs help clients stay ahead of reputational and regulatory risk without building in-house expertise.
This model is particularly relevant for organizations like dating platforms, where trust erosion can have immediate business impact. MSSPs can contextualize findings, provide takedown guidance, and support executive-level reporting 🛡️
Practical Checklist: What Organizations Should Do Next
Below is a practical checklist security leaders can follow when a potential leak is identified, ensuring a structured and defensible response.
- Verify claims through independent intelligence sources
- Preserve evidence and document timelines
- Assess exposed data categories and user impact
- Engage legal and compliance teams early
- Communicate transparently with stakeholders
- Enhance continuous monitoring and alerting
This checklist supports featured snippet visibility while offering immediate value to readers seeking guidance.
Expert Insight on Underground Data Exposure
“Dark web disclosures are often incomplete or exaggerated, but ignoring them is a mistake,” notes a senior analyst cited in multiple cybersecurity briefings. “The goal isn’t panic, it’s preparedness—knowing what’s being said and acting proportionally.” This perspective reinforces why monitoring, not assumption, is the cornerstone of modern cyber defense 🧩
Trusted Resources and Further Reading
For ongoing intelligence and context around underground activity, readers can explore research and updates available at dark web monitoring platforms which provides insights into forums, marketplaces, and threat trends. Additional perspectives on breach response and consumer protection are available from the U.S. Federal Trade Commission at https://www.ftc.gov, a high-authority resource on data security and privacy. These references help ground analysis in reputable guidance 🔍
Final Thoughts and Call to Action
Dark Web Monitoring is no longer optional for organizations operating at scale in data-driven industries. The alleged Bumble.com leak discussed on Darkforums.st illustrates how quickly claims can spread and why visibility into hidden channels is essential for timely, measured response. Whether the data proves fully accurate or not, the lesson remains clear: proactive monitoring, clear reporting, and integrated response capabilities define resilience in today’s threat landscape 🚀
Discover much more in our complete guide
Request a demo NOW
*Disclaimer: DarknetSearch reports on publicly available threat-intelligence sources. Inclusion of an organization in an article does not imply confirmed compromise. All claims are attributed to external sources unless explicitly verified.
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.

