➤Summary
The Colvanes SAS data leak is an alarming incident now circulating on dark-web forums after a 31 October 2025 post by a user called “OnionGarbage.” The actor claims to be selling more than 400 GB uncompressed (around 140 GB compressed) plus a full database with an intranet injection endpoint, REST API source code, and billing photos — totaling 500 GB+ of allegedly fresh 2025 data. This revelation, found during routine dark-web monitoring, raises immediate risks for customers, partners, and the logistics sector at large. Read on for a detailed, actionable breakdown — with proof placeholders, mitigation checklist, and expert resources. 😱🔐📦
📸 [Forum post proof]

Quick summary: what the post claims
The threat actor’s message says: over 400 GB uncompressed, ~140 GB compressed (zst and other formats), database access (with an endpoint enabling code injection on the intranet), a “guide query API” exposing billing photos and customer information, and the REST API source code. They advertise “All fresh data 2025 include guides — total size = 500 GB+.” If authentic, this is both a massive data breach logistics firm event and an API/source-code theft nightmare. 🔥
Screenshot of Data
[Sample]
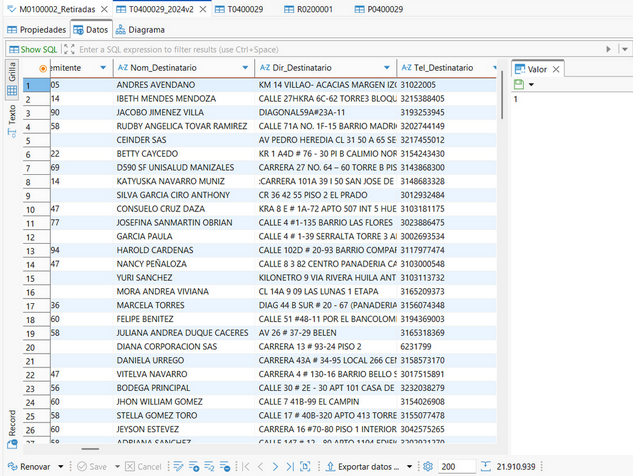
[Sample]
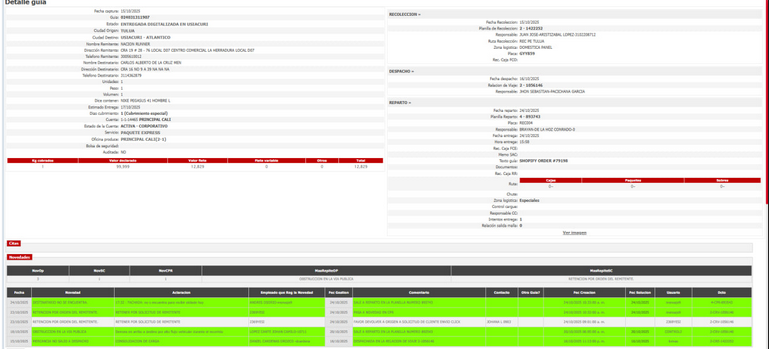
[Sample]
How the leak was discovered
The Kaduu monitoring team (and other dark-web surveillance services) detected the listing during routine scans of underground forums and marketplaces. Cyber threat intelligence platforms such as DarknetSearch often uncover such postings hours to days before mainstream outlets — which is why continuous exposure scanning matters. For more on dark-web scanning approaches, see their latest dark-web exposure reports. 🔎
7 urgent facts about the Colvanes SAS data leak (concise list)
1️⃣ Scale: The actor claims 500 GB+ of data, including compressed/uncompressed dumps and images — this quantity is consistent with a mid-to-large logistics company’s transactional and multimedia data stores.
2️⃣ Type of data: Claimed contents include customer names, addresses, billing photos, shipment records, and API/source code — meaning both PII and system-level assets are at risk.
3️⃣ Attack surface: The post mentions an endpoint for code injection, indicating potential API or intranet misconfiguration.
4️⃣ Freshness: The seller claims these are “fresh data 2025” — modern/active records, not just old backups.
5️⃣ Sale format: Files offered in zst and other compressed formats, plus an interactive query API to browse data (very dangerous).
6️⃣ Trust & verification: At present the leak is reported by dark-web monitoring and early reporting sites — independent verification (file hashes, samples vetted by multiple firms) is limited. Treat as credible but unverified.
7️⃣ Industry impact: Logistics firms are prime targets due to the value of shipping records and business-continuity impact — expect regulatory interest and supplier alerts. 📛
Why this matters (risks explained)
The Colvanes SAS data leak and the linked Envía data leak go beyond simple file theft: they claim system access and exploitable endpoints. That elevates the threat from identity theft and phishing to active system tampering, fraudulent shipments, and potential supply-chain compromises. Exposed source code and APIs enable attackers to search for vulnerabilities, replicate internal logic, or craft sophisticated impersonation attacks. LSI phrases: database injection endpoint, billing photos leak, REST API source code exposed, data breach logistics firm, dark web data sale. 🔓🚨
Credibility check — evidence & red flags
Evidence supporting credibility: detailed file-size claims, mention of specific artifacts (billing photos, REST API), and detection by professional monitoring services. Red flags: no official Colvanes/Envía admission yet, and threat-actor or hackers screenshots can be faked. Until forensic verification (hashes, sample review by third-party responders) is public, treat the listing as likely but not fully proven. Proactive defensive steps are still recommended. ✅
Practical checklist — what to do now (for users & organizations)
For individual customers:
🛡️ Change passwords and enable MFA on associated accounts.
🛡️ Watch for phishing/impersonation messages claiming to be shipping notices or billing disputes.
🛡️ Monitor financial statements and credit reports for anomalies.
For corporate partners & vendors:
📋 Audit any integrations with Envía/Colvanes (APIs, SFTP, shared credentials).
📋 Block or rotate shared API keys and enforce least privilege.
📋 Scan logs for unusual API queries or large data exports starting weeks before 31 Oct 2025.
📋 Notify legal & compliance teams and prepare regulator notifications if affected.
For Envía / Colvanes themselves:
🔧 Engage independent forensic investigators and preserve logs.
🔧 Publish a factual, timely disclosure to affected parties.
🔧 Patch injection points, rotate credentials, and sandbox exposed APIs.
🔧 Increase dark-web monitoring and negotiate takedowns where possible.
Practical tip — quick verification steps for security teams
✅ Request file samples or hashes from monitoring providers and compare to backups.
✅ Check network egress logs for unusual large transfers.
✅ Isolate any public API endpoints and perform controlled scans.
✅ Consider legal takedown requests and notify data-protection authorities. 📌
Expert note & context
“Logistics and courier firms sit on rich PII and multimedia (billing photos) that attackers monetize quickly,” says a threat-intelligence summary on dark-web monitoring best practices by Recorded Future. ⚙️
FAQ (featured snippet style)
Q: Has Envía/Colvanes confirmed the breach?
A: As of this article, Envía/Colvanes has not publicly confirmed a full compromise; the posting was detected on 31 Oct 2025 on Darkforums.st and reported by dark-web monitoring teams. Treat the listing as credible but pending independent verification.
Checklist (table snippet for featured-snippet friendliness)
| Item | Action (48-hour priority) |
| API keys | Rotate all keys & revoke unused clients |
| Logs | Preserve and analyze egress + auth logs |
| Communication | Draft customer/partner notice templates |
| Monitoring | Increase dark-web & brand monitoring |
| MFA | Enforce for all employee & admin accounts |
Related reading & embedded links
- For further dark-web monitoring tools and coverage, visit DarknetSearch for continuous monitoring solutions and examples.
• For context on the monitoring capability used to spot this posting, review Kaduu’s dark-web monitoring overview.
• For an authoritative primer on dark-web detection and response, see the Recorded Future guide to dark-web monitoring.
Final analysis
The Colvanes SAS data leak (operating as Envía) may represent a major exposure of customer and operational data — including Envía customer billing photos leaked and API/source-code artifacts — that threatens privacy and system integrity. Even if some details remain unverified, the combination of claimed database access and source-code exposure warrants immediate action from customers, partners, and the company itself. Act now: rotate credentials, enable MFA, audit integrations and engage forensic help. 🔐🚀
🔍 Discover much more in our complete guide
📩 Request a demo NOW
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.

