➤Summary
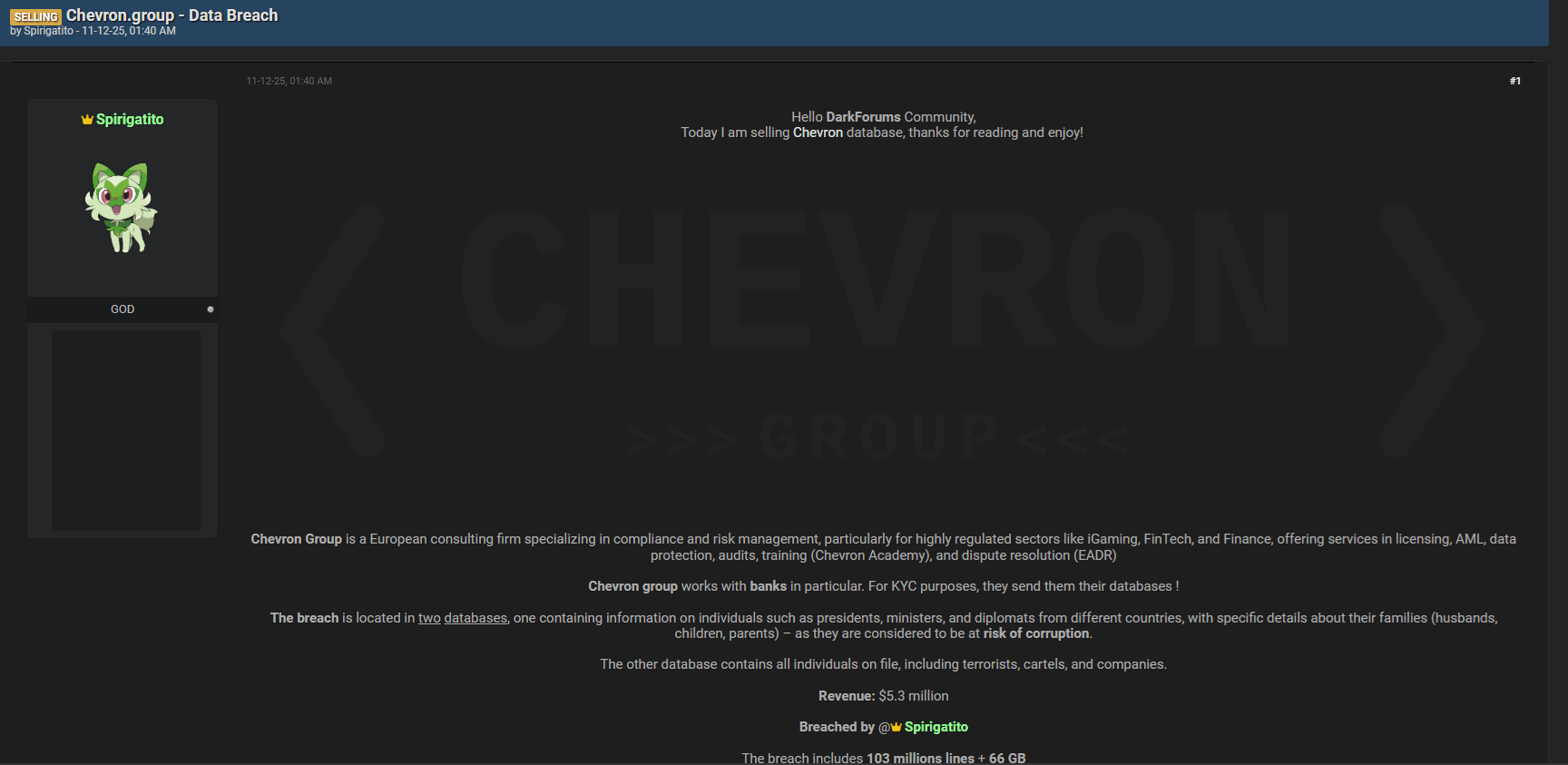
The Chevron.group data breach allegation has emerged as a serious cybersecurity concern after a post appeared on Darkforums.hn claiming the sale of highly sensitive databases. Reported by a forum user known as Spirigatito and dated 11 December 2025, the incident has attracted attention from Security Practitioners, and risk intelligence teams worldwide. According to the post, the data allegedly originates from chevron.group systems and includes records tied to high-profile political figures and high-risk individuals. While the claims remain unverified, the scale and sensitivity described make this case noteworthy for organizations tracking underground data exposure trends. 🔍
Clarifying the Alleged Target
It is important to clearly differentiate the entity referenced in this alleged Chevron.group data breach. The victim described in the forum post does not appear to be Chevron Corporation, the United States based energy multinational. Instead, the contextual details provided by the seller, including references to European compliance operations and iGaming sector exposure, strongly suggest a distinct business to business organization. This entity is believed to operate as a specialized provider of Anti Money Laundering and Know Your Customer screening services, supporting risk assessment and compliance workflows for regulated industries. 🧩
This distinction is critical for accurate attribution, responsible reporting, and for Security Practitioners conducting cyber threat intelligence analysis, as misidentifying the affected organization could lead to incorrect risk assumptions and misinformation.
The Chevron.group data breach discussion highlights why monitoring illicit forums remains critical for understanding emerging threats and potential downstream risks.
What is being claimed in the Chevron.group data breach
The alleged Chevron.group data breach centers on two separate databases reportedly extracted from internal systems. The first database is described as containing information on presidents, ministers, diplomats, and other politically exposed persons across multiple countries. According to the seller, these profiles also include detailed data about family members such as spouses, children, and parents, based on the premise that close relatives may face corruption or coercion risks. 🚨
The second database is said to be broader in scope, covering all individuals on file, including terrorists, cartel members, and corporate entities. If authentic, this would suggest exposure of intelligence-adjacent or compliance-related datasets rather than conventional customer information.
Alleged data fields and sensitivity assessment
Based on the forum description, the datasets linked to the Chevron.group data breach allegedly contain a wide range of structured personal information. Claimed fields include full name, case identifier, date of birth, passport number, residential address, country, and warning notices tied to risk or compliance status. Some entries are said to include contextual notes that could reveal investigative interest or threat classification. 🧠
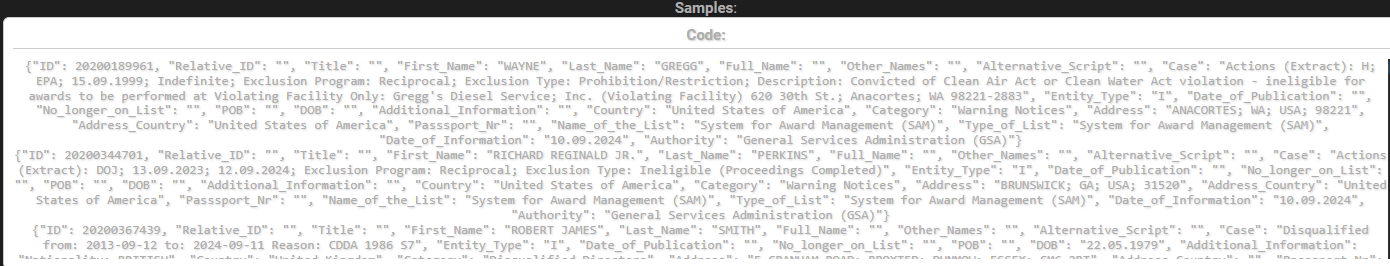
From a Security Practitioners perspective, the combination of identity data and risk annotations dramatically increases potential harm, enabling identity abuse, targeted surveillance, or coercion if misused.
Why this alleged breach stands out in Technology risk analysis
Unlike typical breaches involving login credentials or marketing databases, the Chevron.group data breach claims focus on individuals already considered high-risk. Technology teams managing sensitive datasets are expected to enforce strict access controls, logging, and segmentation. A failure in any of these areas could lead to cascading exposure. ⚙️
This case underlines how breaches involving intelligence, compliance, or due diligence platforms carry disproportionate consequences compared to standard consumer data leaks.
Status of verification and threat actor credibility
At the time of writing, the Chevron.group data breach remains unconfirmed. No official statement from Chevron Group has been published, and no cryptographic proof or downloadable samples have been released publicly. Darkforums.hn is known to host a mix of genuine leaks, recycled data, and exaggerated claims, making independent validation essential. 🧩
Security Practitioners typically treat such posts as early indicators rather than confirmed incidents, monitoring for corroborating evidence such as secondary resellers, data samples, or victim acknowledgments.
Relevance for Security Practitioners and intelligence teams
For Security Practitioners, the Chevron.group data breach allegation serves as a reminder of the importance of continuous cyber threat intelligence collection. Monitoring underground forums allows teams to detect potential data exposure early, even before official disclosures occur. This approach supports faster incident response planning and stakeholder communication. 🛡️
Role of Dark web monitoring in early detection
Effective Dark web monitoring plays a crucial role in identifying alleged breaches like this one before they escalate. By tracking specific brand mentions, dataset descriptions, and seller reputations, analysts can assess credibility and prioritize response actions. This approach is particularly valuable when dealing with non-traditional datasets that may not trigger automated breach notifications. 👀
Case study dark web monitoring insights from similar incidents
As a case study dark web monitoring example, previous incidents involving compliance databases show that early forum detection often precedes mainstream reporting by weeks or months. In several documented cases, organizations were able to confirm exposure, notify regulators, and mitigate harm faster because underground chatter was identified early. 📊
Applying these lessons to the Chevron.group data breach allegation emphasizes the value of proactive intelligence rather than reactive crisis management.
Potential impact if the claims are accurate
If the Chevron.group data breach is confirmed, the implications could extend far beyond reputational damage. Affected individuals could face personal safety risks, diplomatic complications, or financial harm. Governments and corporations may need to reassess protective measures for those named in the datasets. 🔐
From a Technology governance standpoint, regulators could scrutinize data handling practices, retention policies, and third-party integrations associated with the affected systems.
Internal and external reference points for analysis
Analysts tracking the Chevron.group data breach often compare it with similar exposures documented on research platforms such as https://darknetsearch.com/, where multiple alleged incidents are cataloged and analyzed. Additional background on breach response best practices can be found through authoritative guidance from organizations like the Cybersecurity and Infrastructure Security Agency at https://www.cisa.gov/, which maintains a strong domain authority and practical incident response frameworks. 📚
These reference points help contextualize the severity and likelihood of underground claims.
Practical checklist for organizations
Here is a concise checklist Security Practitioners can apply when assessing allegations like the Chevron.group data breach:
- Monitor underground forums and marketplaces for brand mentions
- Validate claims through cross-forum correlation
- Review access logs and anomaly alerts for sensitive systems
- Prepare communication templates for stakeholders
- Coordinate with legal and compliance teams early
Following this checklist improves readiness even when allegations remain unverified. ✅
Key question answered clearly
Is the Chevron.group data breach confirmed?
No. As of now, it remains an allegation posted on an underground forum with no official confirmation or publicly verifiable evidence. This distinction is critical for responsible reporting and response planning.
Technology trends and expert perspective
An independent cyber threat intelligence analyst quoted in prior industry research noted that breaches involving politically exposed persons data often originate from misconfigured access or over-privileged accounts rather than external exploits. This aligns with broader Technology trends showing insider risk and credential misuse as leading causes of sensitive data exposure. 🧠
While this quote does not confirm the Chevron.group data breach, it provides a plausible risk model for analysis.
Conclusion and next steps
The Chevron.group data breach allegation underscores the evolving nature of cyber risk, where the most damaging incidents may involve intelligence-grade data rather than consumer records. For Security Practitioners and Technology leaders, staying informed through structured monitoring and credible analysis is essential. Continued observation of Darkforums.hn and related channels will determine whether this case develops into a verified incident or fades as an unsubstantiated claim. 📌
Discover much more in our complete guide
Request a demo NOW
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.

