Category: ➽Generic Information
-

Verizon outage: urgent impact guide with 7 facts on nationwide disruption
The Verizon outage that rippled across the United States raised immediate concerns about the resilience of critical communications infrastructure. Millions of users experienced service disruptions affecting voice calls, data access, and connectivity for businesses and public services. While outages are not uncommon for large telecom providers, the scale and visibility of this incident prompted questions…
-

Why the Latest Synthient “Stealer Log Mega-File” Is Not a Darknet Breach And Why It Matters
Over the past months, security communities have discussed a newly surfaced, extremely large “stealer log” file referenced indirectly through research by Synthient and indexed by HaveIBeenPwned (HIBP). Many users interpreted this as a new darknet breach, a massive leak, or a previously unknown dataset circulating among cybercriminals. But this conclusion is incorrect. After reviewing the…
-

Integrating Darknet Monitoring with NIST Threat Intelligence Framework
Image Source: AI Generated Organizations face about 1,000 cyber attacks every hour. This makes useful threat intelligence a vital part of modern cybersecurity programs. The NIST threat intelligence framework guides organizations to identify, assess and respond to cyber threats. The situation becomes more challenging as threat actors now operate in dark web environments. Security teams…
-
Understanding Credential Stuffing Attacks: How Breached Passwords Are Exploited
Credential stuffing attacks have become one of the most significant cybersecurity threats facing organizations today. These automated attacks attempt millions of stolen username and password combinations across multiple websites, leading to substantial financial losses and data breaches. Recent studies show that credential stuffing attempts account for over 80% of login traffic on many corporate networks,…
-
The Silent Threat: How Domain Spoofing and Typosquatting Fuel Cybercrime
Cybercriminals are constantly devising new ways to infiltrate our digital lives. Two particularly insidious techniques – domain spoofing and typosquatting – have emerged as powerful weapons in their arsenal. These methods are not just abstract concepts; they’re the gateway to phishing attacks, malware infections, and data breaches that can bring organizations to their knees. The…
-

Kaduu creates Spoofguard – a Domain Variation Analysis Engine to Detect and Mitigate Typosquatting Threats
What is the cyber-risk? Typosquatting, also known as URL hijacking, involves registering domain names that closely resemble legitimate domains of reputable brands but include small typographical errors. These deceptive domains are often leveraged by attackers in phishing and malware dissemination campaigns. By exploiting common typos made by internet users, attackers can lure victims into visiting…
-
The Sad Reality of Cyber Exploitation
Cybercriminals often exploit open databases that are accessible via the internet. These databases, when improperly secured, can be a gold mine for malicious actors. By using search engines like ZoomEye, attackers can programmaticallylocate databases left open to the public and use this access for harmful purposes, such as encrypting the data to demand ransom. How…
-

The Reality of Data Breach Take-Down Services in 2024: Do They Work?
The concept of data breach takedown services refers to the efforts made by cybersecurity firms or specialized service providers to mitigate the impact of a data breach by removing unauthorized online content that contains stolen or leaked information. These services often involve the identification, verification, and takedown of sensitive information from websites, forums, chat rooms,…
-
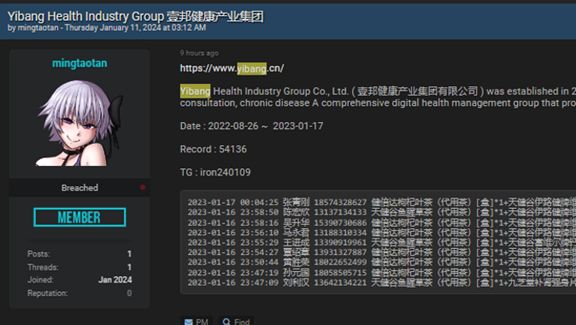
Exploring PHI (Medical Records) Sales and Cost Structures in the Darknet
This chapter focuses on the various types of medical data that are found on the darknet. The illicit sale of this data highlights significant risks to patient privacy and the integrity of medical institutions. Lets first explore the value of medical records. What is the price for PHI (medical records) on the darknet? The price…
-

Russia’s FSB-sponsored Cybercriminals Utilize Innovative Spica Malware
Russia’s notorious hacker group, ColdRiver, backed by the Federal Security Service (FSB), has recently unleashed a new wave of cyberattacks. The group has deployed a unique backdoor malware, dubbed “Spica,” that impersonates a PDF decryption tool. This development marks a significant evolution in the hacker group’s tactics, techniques, and procedures (TTPs), which potential targets should…
