Author: Cybersecurity Analyst
-
They Steal Our Democracy: New Electoral Data Breach Exposes 8 years of UK Voter Data
The UK Voters Data Breach In an era dominated by digital advancements, the sanctity of democratic processes faces unforeseen threats. Recent revelations of electoral data breaches have ignited concerns over the vulnerability of voting systems. The journey towards safeguarding the essence of democracy takes a precarious turn as incidents akin to the one involving the…
-
FraudGPT: The Latest AI Tool for Sophisticated Cyber Attacks
Why not “FraudClaude”? It sounds even better 😄 In a rapidly evolving cyber landscape, threat actors have once again made their presence known with the emergence of a new AI tool called FraudGPT. Following in the footsteps of its predecessor, WormGPT, this cutting-edge technology is specifically designed to facilitate advanced cybercrime activities. Dark web marketplaces,…
-

An Inside Look at How Cybercriminals Sell Stolen Credit Card Information
When it comes to the hidden corners of the internet, few places are as infamous as the darknet and deep web. They are sometimes misunderstood and often misrepresented. While they have legitimate uses, they have also gained notoriety for harboring a thriving trade in illicit goods, including stolen credit card details. To clarify, the deep…
-
MOVEit Hack Exposes Deutsche Bank’s Client Data
Multiple banks affected by the same service provider attack Deutsche Bank AG, one of the world’s largest financial institutions, has confirmed a data breach at one of its service providers, leading to the exposure of customer data. The breach is believed to be part of a larger MOVEit Transfer data-theft attack. Bank spokesperson comments on…
-
The Week in Threat Actors – July 6 – The new and the arrested
Unmasking the New Cyber Threats and Celebrating Security Victories The cyber security landscape is a dynamic and ever-evolving field, with new threat actors emerging and existing ones being apprehended. The first week of July has been no exception, with a flurry of activity that has kept the cyber security community on high alert. Here’s a…
-
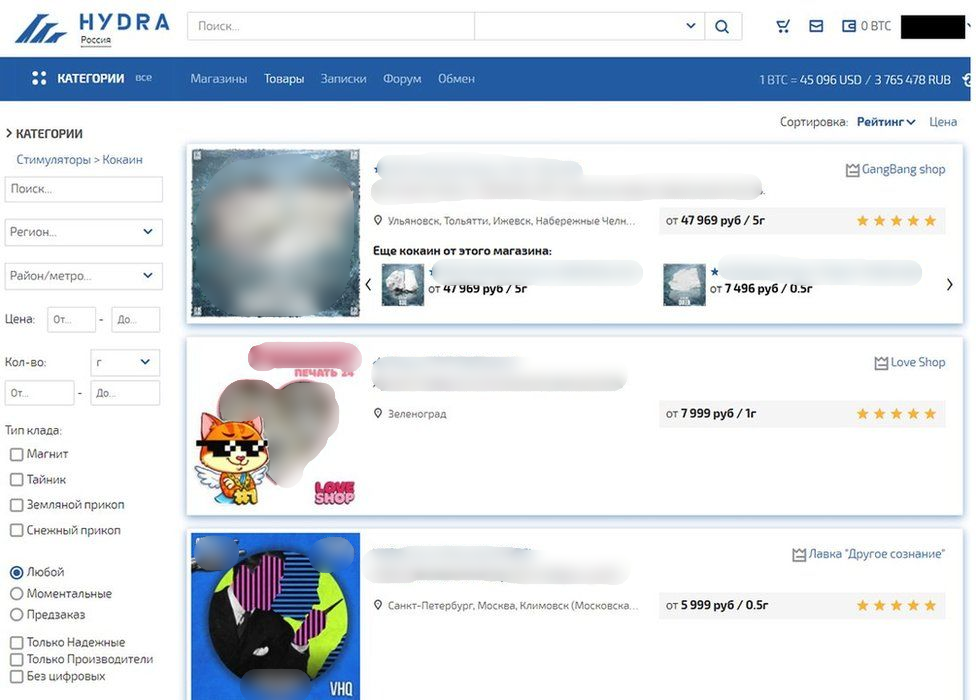
The Next Era of Cybercrime: Dark Web Marketplaces and Threats on the Horizon
As the digital landscape constantly evolves, so does the world of cybercrime. The fall of prominent dark web marketplaces, reshaping geopolitical dynamics, and the ever-evolving tactics of cybercriminals, all contribute to the continually shifting landscape. This article delves into the future of cybercrime, focusing on the evolution of dark web marketplaces and the emerging threats.…
-
Swiss Government and Bank System Under Siege
Pro-Russian Cyber Group “NoName” Attacks and Leaves Unresponsive Dozens of Swiss Websites On Monday, June 12, 2023, the Swiss government and several state-linked companies fell victim to a series of cyber-attacks, rendering their websites inaccessible. The finance ministry of Switzerland confirmed the incident, stating that federal administration specialists were quick to notice the attack and…
-
The Emergence of Rhysida and DarkRace: Two New Ransomware Threats
At least ten victims are listed in roughly a week of existence Ransomware attacks have been on the rise in recent years, and two new groups have emerged in May 2023: Rhysida and DarkRace. These sophisticated ransomware groups have already targeted several organizations across Europe, encrypting victims’ data and demanding ransom payments. Rhysida Ransomware Targets…
-
An Introduction to the Ransomware Business Model
In the ever-evolving digital landscape, ransomware attacks have carved a niche as an extremely lucrative venture for cybercriminals. But why exactly have they become a magnet for hackers worldwide? This blog post delves into the mechanics of ransomware operations and how they fuel the engines of cybercrime economies. Ransomware is a type of malicious software…
-
The Rise of AI Malware: How to Protect Yourself
AI Enthusiasts gradually become #1 target for cybercriminals Over the years, malware operators have continuously adapted their strategies to capitalize on emerging trends and exploit new vulnerabilities. In the past, they primarily relied on distributing classic “keygen.exe” programs through platforms like YouTube, file sharing and custom fake websites, preying on users seeking free software or…
