Author: Cybersecurity Analyst
-
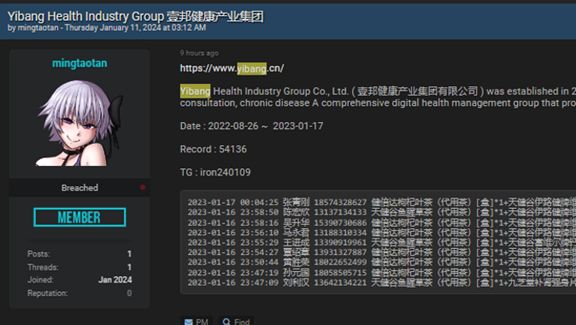
Exploring PHI (Medical Records) Sales and Cost Structures in the Darknet
This chapter focuses on the various types of medical data that are found on the darknet. The illicit sale of this data highlights significant risks to patient privacy and the integrity of medical institutions. Lets first explore the value of medical records. What is the price for PHI (medical records) on the darknet? The price…
-

The Rise of Stealer Logs in 2024
Among the many cyber threats out there, a category of malicious software tools has emerged as a pervasive and insidious danger. These tools, commonly referred to as “stealers,” are designed by cybercriminals to infiltrate computers and surreptitiously extract sensitive data. The malware operates in the background, gathering details like login credentials, personal information (such as…
-
Boeing Cyber Incident: Unraveling the Intricacies
Boeing, one of the world’s leading aerospace companies, confirmed that it was the target of a cyberattack. The company stated that the incident specifically targeted the parts and distribution division of the business. Boeing’s spokesperson, Jim Proulx, emphasized that this incident did not pose a threat to flight safety.This post provides a comprehensive analysis of…
-

MSP vs. MSSP: Navigating the Distinctive Roles and the Crucial Impact of MSSPs on Dark Web Monitoring
Are you confused about the difference between an MSP and an MSSP? You’re not alone. Many people use these terms interchangeably, but they represent two distinct types of service providers in the cybersecurity industry. Understanding the difference can help you make informed decisions about which provider is right for your business. Kaduu has the darknet…
-

AI and Cybersecurity in 2023
In the fast-paced digital age, where threats lurk in the shadows of cyberspace, the importance of robust cybersecurity measures cannot be underestimated. As we look towards the future, one technology stands out as a game-changer in this arena: artificial intelligence (AI). In 2023, AI is set to revolutionize cybersecurity, empowering organizations to stay one step…
-

Securing the Future: Germany’s Triumph at the 2023 European Cybersecurity Challenge
Germany is the winner of the 2023 edition of the ECSC, followed by Switzerland in second place and Denmark in third place. Introduction to the European Cybersecurity Challenge In the rapidly evolving digital landscape, cybersecurity has become a paramount concern for nations across the globe. To address this critical issue, the European Cybersecurity Challenge (ECC)…
-

Safeguarding Your Business Against Credential Theft
As businesses increasingly rely on digital platforms for their operations, the risk of cyber threats and credential theft has become more prevalent. There are many documented examples of passwords being leaked or stolen by darknet hackers – one of the more famous cases was documented by the Washington Post. One recent incident that highlights the…
-

The Importance of Darknet Monitoring for IT Admins
In today’s digital landscape, where cyber threats are constantly evolving, it is crucial for IT administrators to prioritize the security of their systems and networks. One area that often gets overlooked is the use of weak and easily guessable passwords by IT admins themselves. This is a significant vulnerability that can be exploited by hackers,…
-
Protecting the Unprotected: Casio Goes Through its Latest Data Breach
Casio’s data breached impacts customers in 149 countries Japanese electronics manufacturer, Casio, recently found itself at the center of a cybersecurity storm when it disclosed a data breach impacting customers in 149 countries. Consequently, this breach serves as a stark reminder of the importance of safeguarding customer information and the need for constant vigilance in…
-

The Dark Side of Discord: An In-Depth Look into Malware Exploitation
Discord has become a household name in the realm of online communication, offering a convenient platform for text, voice, and video interactions. Its accessibility and user-friendly interface have attracted an array of audiences, from gamers to business communities. Regrettably, it has also caught the attention of cybercriminals who exploit its features for their nefarious activities,…
