➤Summary
The APUS data breach has become a widely discussed topic across cybersecurity circles in late 2025, especially after reports suggested that sensitive student-related data from the American Public University System may have appeared on dark web forums. While these claims remain unverified and should be approached with caution, the conversation highlights serious concerns for universities, online learning institutions, educational industry and anyone affected by potential data exposure. ⚠️ This article explores what has been reported, what remains unconfirmed, and what steps individuals and institutions can take to strengthen student data privacy in an increasingly hostile cyber environment. 😊
Reports From Dark Web Sources and Why They Matter
According to cybersecurity researchers monitoring dark web forums, a user identified as “wikkid” allegedly posted an announcement in November 2025 referencing an APUS cybersecurity incident 2025 that supposedly took place weeks earlier. These posts claimed that personal and academic information such as emails, educational history, military affiliation, and profile details were part of the leaked information. Although none of this has been independently confirmed, even an allegation of a cyberattack involving a large academic institution raises important questions about safety, transparency, and the evolving threat landscape.
➡️ [Forum Post Proof]
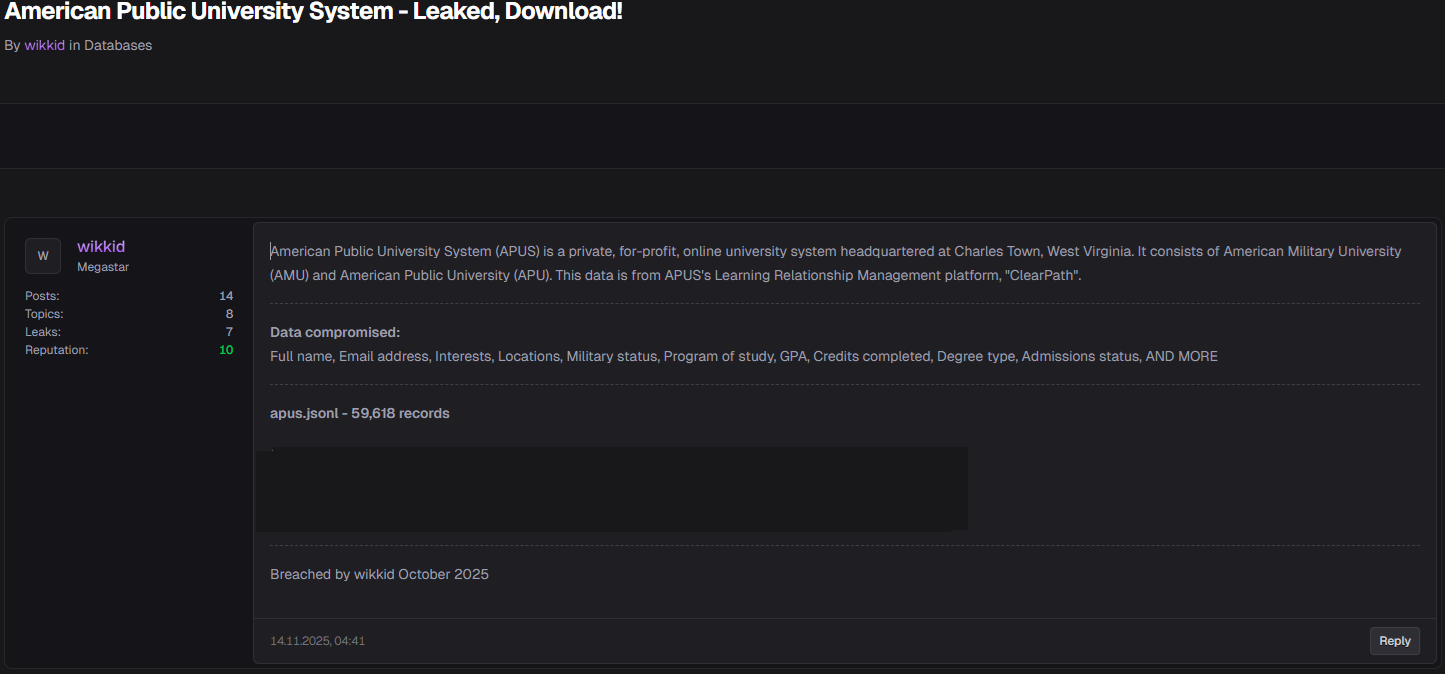
📸 [Screenshot of Data Proof]
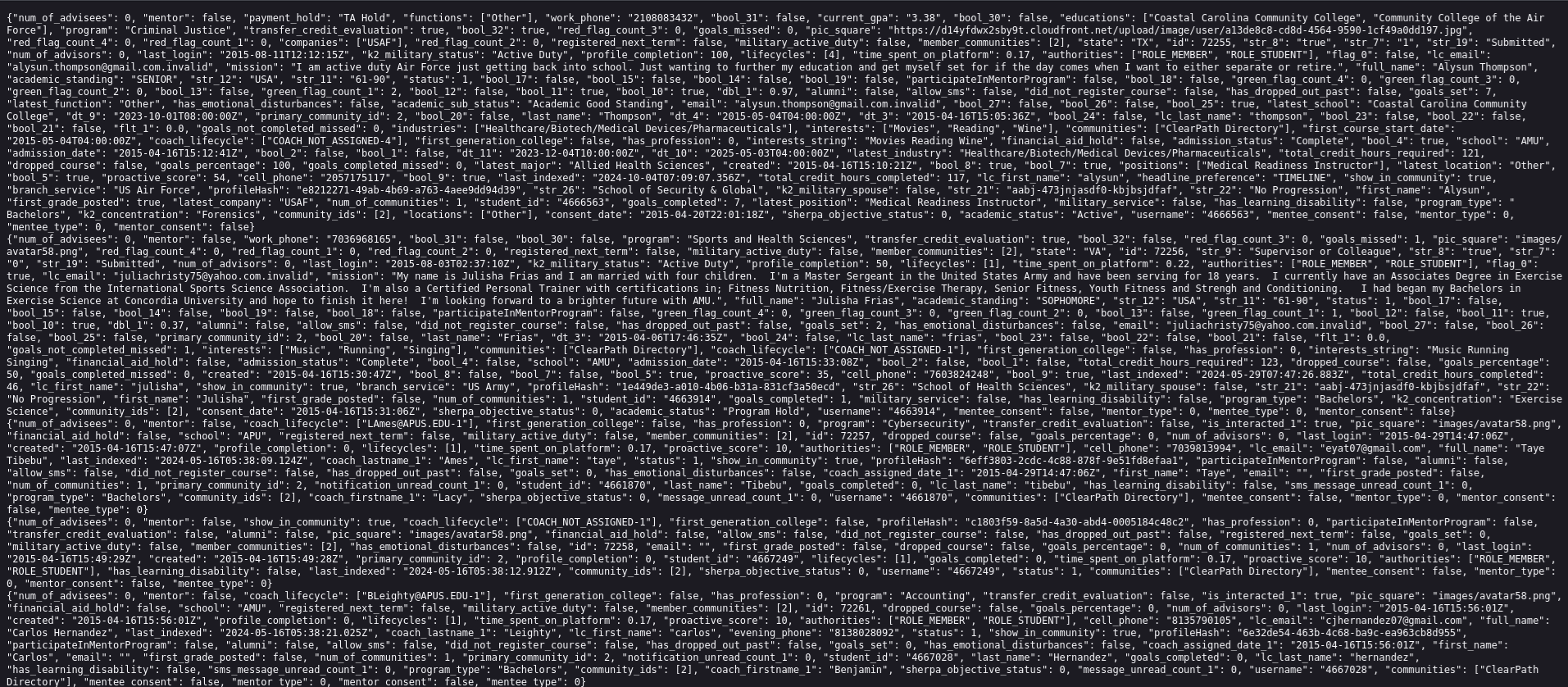
Understanding the American Public University System’s Role in Online Education
The American Public University System is known for serving a large population of online learners, including active-duty military personnel and veterans. Because its programs function almost entirely online, APUS maintains extensive digital records, making education cybersecurity a top priority. With thousands of students relying on safe virtual access, any alleged exposure—verified or not—puts emphasis on the importance of robust data protection practices. Institutions of this scale and digital activity face constant cyber threats, making them prime targets for malicious actors hoping to sell or trade data on hidden internet platforms.
What Makes the APUS Data Breach Discussion So Significant?
The allegations surrounding the APUS data breach matter not because they have been proven true, but because of what they represent. They highlight vulnerabilities that higher education institutions face daily. In recent years, cybercriminals have increasingly targeted academic networks to obtain emails, credentials, and personal details, which are often easier to acquire compared to corporate systems. Universities often manage very large databases, rely on legacy systems, and provide broad access for students, staff, and faculty—creating multiple points of entry for attackers.For example, suppose someone asks:
“Can leaked academic information be used for identity theft?”
✔️ Answer: Yes. Even basic information such as full name, location, or program of study can enable targeted phishing attempts. However, the severity depends on what types of records are actually exposed and whether sensitive identifiers were included—which is unknown in the APUS case.
Indicators and Patterns Seen in Other Higher Education Breach Reports
While details surrounding this case are speculative, cybersecurity experts often observe similar patterns in past breach reports:
- Attackers exploit weak passwords or credential reuse.
- Malware or ransomware infiltrates unpatched systems.
- Phishing emails trick faculty or students into granting access.
- Cloud misconfigurations expose stored data.
- Insider negligence or intentional misuse leads to leaks. These trends highlight why online universities must maintain continuous monitoring, frequent audits, and active cyber awareness training. 🧠 In the event the allegations about APUS were accurate, they would likely fall into one of these recognized categories.
Alleged Data Types and the Importance of Protecting Student Privacy
Even unverified claims mention categories like student interests, academic progress, military affiliation, and contact details. Institutions must guard such information with the utmost care because of its sensitive nature and potential misuse. When analyzing an alleged data exposure, experts consider whether the information could be used to harm individuals, impersonate students, or compromise login systems.🔐
Practical Tip: Enable multi-factor authentication on all university-related logins to reduce the risk of unauthorized account access. This single change blocks more than 90% of credential-based attacks.
How Dark Web Forums Influence Perception of Cyber Incidents
One significant challenge is misinformation. Cybercriminal forums often exaggerate or fabricate leaks to gain reputation, boast, or sell unrelated data. This means an alleged APUS data breach mentioned online must be viewed critically until confirmed by official channels. Nonetheless, the appearance of such posts—real or fake—serves as a wake-up call. They reveal how frequently academic institutions appear in criminal discussions.
For more context on how dark web activity works, readers can explore trusted resources such as DarknetSearch:
👉 https://darknetsearch.com/
The Growing Threat Against Online Universities
The shift to digital-first education has made institutions like the American Public University System more reliant on online platforms for everything: registration, advising, academic submissions, communication, and degree progress tracking. With this digital dependence, attackers see universities as high-value systems with large, diverse datasets that may not be protected as rigorously as corporate networks.Education is now one of the five most targeted sectors globally (according to independent cybersecurity analyses like those published by IBM: https://www.ibm.com/security). 🎓 These trends underscore why discussions about student data privacy and education cybersecurity continue to grow.
Preventive Measures Students Can Take Today
Even if the APUS data breach allegations remain unverified, students can take proactive steps.
📌 Checklist for Students:
- Update all APUS and non-APUS passwords.
- Avoid reusing passwords across multiple services.
- Activate MFA where available.
- Monitor inboxes for unusual messages.
- Do not click links in unsolicited emails.
- Review credit reports quarterly.These steps significantly reduce risks associated with phishing and identity misuse.
How Institutions Should Respond to Alleged or Real Data Incidents
Institutions like the American Public University System must have well-structured incident response plans, even when dealing only with unverified claims. An effective response plan includes:
- Immediate internal investigation
- Third-party forensic analysis
- Clear communication with staff and students
- Reviewing access logs for anomalies
- Implementing system patches
- Strengthening policies for data accessProactive action protects both institutional reputation and student confidence. 🔧
Expert Insight on Academic Cybersecurity
Cybersecurity specialists often emphasize that academic data is just as valuable as financial or medical information. As one expert commonly states, “Universities must treat their data infrastructure as critically as banks treat their vaults.” This perspective is crucial because modern universities hold personal, behavioural, academic, and sometimes biometric data. Allegations like the APUS data breach simply reinforce the need for stronger, more proactive security frameworks across the education sector.
Why Transparency Matters in a Cyber-First Academic World
Transparency builds trust. Even when faced with unconfirmed allegations, institutions benefit from communicating clearly with students and faculty. This includes openly discussing preventive measures, system upgrades, and safety best practices. People feel safer when they understand what is happening and what is being done to protect them. 💬
Final Thoughts: What the APUS Data Breach Story Teaches Us
The conversation around the APUS data breach—whether ultimately verified or disproven—has highlighted major issues in the intersection of education, technology, and cybersecurity. As online institutions grow, so do risks. Students must stay informed, and universities must continually upgrade their defences.Ready to dive deeper into cybersecurity topics, academic data protection, or dark web threat monitoring?
👉 Discover much more in our complete guide
👉 Request a demo NOW
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.

