➤Summary
The ALSA data leak has shaken Spain’s cybersecurity landscape, with millions of customers potentially exposed after their personal information surfaced on a notorious underground forum. On September 16, 2025, a dark web user under the alias “draco” published a massive dataset allegedly tied to ALSA.es, Spain’s largest transport company. According to the leak, 2.4 million customers and 15,000 employees may have had their sensitive information stolen. 🚨
Discovered by The Kaduu Team during routine darknet monitoring, the breach raises urgent questions about data protection, consumer safety, and corporate responsibility. With records containing identification numbers, phone contacts, emails, and birth years, the leaked files provide cybercriminals with exactly the type of information they can exploit for scams, phishing, and identity theft.
What We Know About the ALSA Breach
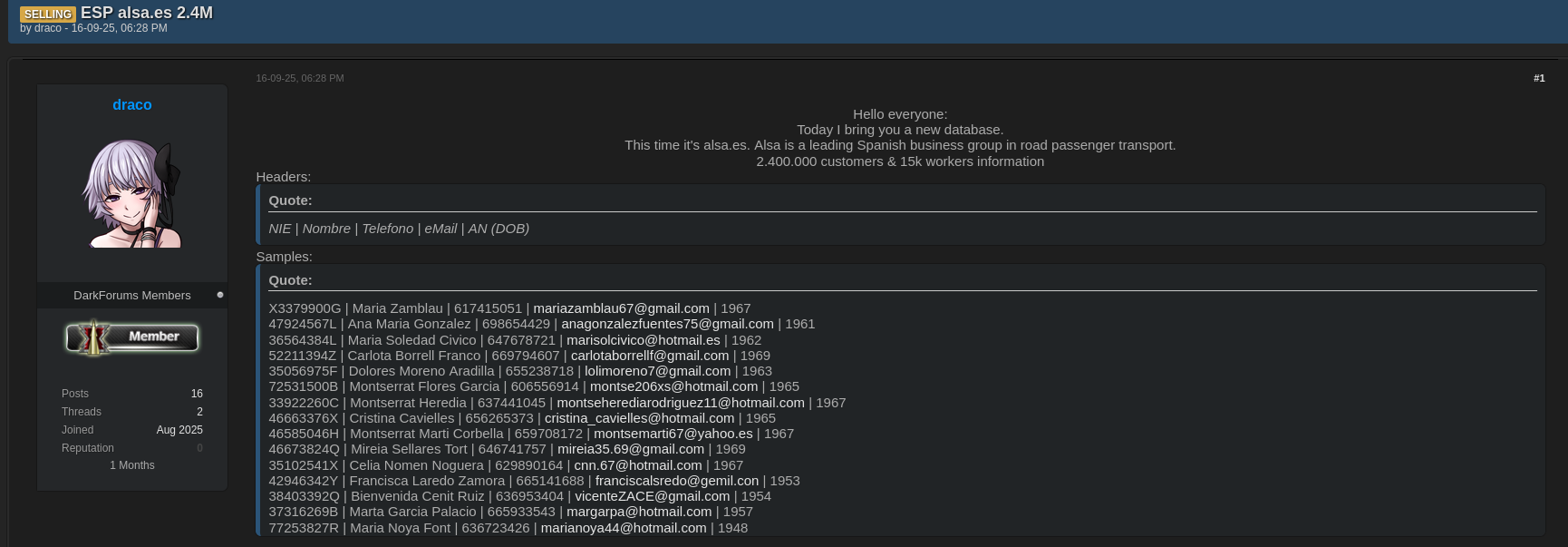
The alleged ALSA data leak first appeared on Darkforums.st, a popular underground marketplace where stolen databases are traded and exposed. The author “draco” claimed direct access to sensitive ALSA records but provided no details about the exact method of the cyber attack.
Unlike some leaks that are simply shared for reputation, this particular database is being offered for sale by draco, meaning cybercriminals willing to pay could potentially acquire the full dataset.
According to the leaked information:
- 2,400,000 customer records were compromised
- 15,000 employee files were included
- Each record contained NIE (identification number), full name, telephone, email, and birth year
Sample records from the forum included:
X3379900G | Maria Zamblau | 617415051 | mariazamblau67@gmail.com | 1967
47924567L | Ana Maria Gonzalez | 698654429 | anagonzalezfuentes75@gmail.com | 1961
While only small samples were shared publicly, cybersecurity experts believe the volume and type of information align with past database leaks seen in Spain.
Why the ALSA Data Leak Matters
A database leak of this scale can have far-reaching consequences. Exposed personal information like identification numbers and emails opens the door for:
- Identity theft – Criminals can impersonate victims for financial fraud.
- Phishing scams – Fraudulent emails targeting ALSA customers could increase sharply.
- Social engineering – Attackers may use stolen phone numbers for SMS scams or fake calls.
- Credential stuffing – If victims reused passwords, hackers could target other accounts.
💡 Practical Tip: If you were a customer or employee of ALSA.es, immediately change your account passwords, enable two-factor authentication, and remain cautious of unsolicited emails or calls.
Proof of the ALSA.es Customer Data Leak
The forum post provided sample data records as proof. These samples matched real Spanish formats for NIEs and emails, making the leak appear credible. The Kaduu team also confirmed spotting the dataset in multiple darknet threads, though its full extent remains unverified.
The original post included a reserved space for further proof, which indicates that the seller or leaker may release additional evidence to attract buyers or gain notoriety in cybercriminal circles. 🔎
Screenshot of the post:
Expert Analysis on the ALSA Breach
Cybersecurity experts warn that transport and travel companies are prime targets for cybercriminals due to the large amounts of personal and payment data they hold. Reports confirm that Europe’s transportation sector faced a growing share of cyberattacks in 2023–2024 (S&P Global, ENISA).
Monitoring firms such as Kaduu (DarknetSearch) highlight that routine darknet surveillance is essential for detecting leaks early (DarknetSearch, Kaduu News).
“Large mobility companies are attractive targets for cybercriminals… exposed records often end up traded on the dark web.”
The statement reflects findings from multiple threat intelligence sources, including Cybersecurity Intelligence, Kaduu reports, and industry reviews (Software Advice).
In short, both industry analysts and official agencies agree: mobility companies like ALSA face rising cybersecurity risks, making proactive monitoring and fast incident response critical.
Timeline of Events in the ALSA Data Leak
- September 16, 2025 – Forum post published by user “draco” on Darkforums.st.
- Mid-September 2025 – The Kaduu Team discovers the leak during monitoring.
- Date of actual breach – Unknown, as the leak post provided no timeline.
- Current status – Data being actively sold on darknet forums.
This lack of transparency around the breach date complicates incident response and victim protection efforts.
Risks for ALSA Customers and Employees
The ALSA.es customer data leak exposes individuals to multiple cybersecurity threats. Here’s a quick checklist of risks and prevention measures:
Risks:
- Phishing emails targeting ALSA users
- Smishing (SMS-based scams) 📱
- Identity fraud using NIE numbers
- Fraudulent online registrations
- Targeted spam campaigns
Prevention Measures:
- Verify all ALSA-related emails before clicking links
- Use unique, strong passwords for all accounts
- Monitor bank and credit card statements regularly
- Report suspicious activity to Spanish data protection authorities
ALSA’s Official Response (or Lack Thereof)
As of today, ALSA.es has not released any official statement regarding the incident. This silence leaves both customers and cybersecurity professionals in the dark. In past cases, delayed responses have worsened the impact of cybersecurity incidents by allowing criminals more time to exploit stolen data.
Regulators in Spain may investigate whether ALSA complied with GDPR obligations, which require companies to report breaches within 72 hours of discovery. 🚨
How the ALSA Data Leak Could Spread
Leaks like this often follow a pattern of escalation:
- Initial leak announcement on dark web forums.
- Sample data release to prove authenticity.
- Sale or free distribution among cybercriminals.
- Resale and repackaging on other forums or Telegram channels.
- Public exposure through mainstream news and breach databases.
Once data enters this cycle, removing it from circulation is virtually impossible.
Similar Cases in Spain
Spain has faced multiple data breaches in recent years, affecting sectors from healthcare to telecommunications. For example, Telefónica and Iberia previously reported smaller leaks. The ALSA data leak, however, stands out because of the sheer volume of exposed records and the direct involvement of customers’ identification numbers.
Checklist: What to Do If You’re Affected by the ALSA Breach
- ✅ Change your ALSA account password immediately
- ✅ Enable two-factor authentication on related services
- ✅ Check if your email appears in breach databases like HaveIBeenPwned (external DA 90+)
- ✅ Be cautious of emails offering refunds, vouchers, or urgent payment requests
- ✅ Monitor credit activity for unusual transactions
The Bigger Picture: Data Breaches in Europe
The ALSA data leak reflects a growing trend of cyber attacks in Europe. With stricter GDPR regulations, companies must improve cybersecurity defenses or face heavy fines. Meanwhile, dark web markets remain the go-to place for trading stolen information, highlighting the urgent need for proactive monitoring.
For additional analysis of current breaches, visit DarknetSearch where threat intelligence teams track leaks in real-time.
Conclusion
The ALSA data leak is more than just a cybersecurity headline—it’s a wake-up call for both companies and individuals. With millions of exposed records circulating online and actively being sold by “draco,” the ALSA breach highlights how critical it is to safeguard sensitive information and react quickly to suspicious activity.
For affected users, the best defense is vigilance: monitor accounts, change passwords, and remain skeptical of unsolicited messages. For companies, this breach is another reminder of the importance of robust data protection policies and transparent communication.
👉 Discover much more in our complete guide at DarknetSearch.com
👉 Request a demo NOW to see how proactive monitoring can protect your business
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.

