➤Summary
The Malaysian data breach reported in late 2025 sparked significant public attention 🔥, especially after claims surfaced on a dark-web community alleging that a student-related platform had suffered a large-scale compromise. According to the forum post, the attacker published what they described as full access to a student information system—an event that, if true, raises major concerns about personal data exposure, cybersecurity practices, and the safety of educational platforms. This report explores the context of the alleged incident, the risks involved, and how such claims impact both students and institutions. As the discussion continues to evolve, understanding the mechanisms behind a Malaysian data breach becomes essential for safeguarding digital ecosystems.
[Data Proof] 🎯
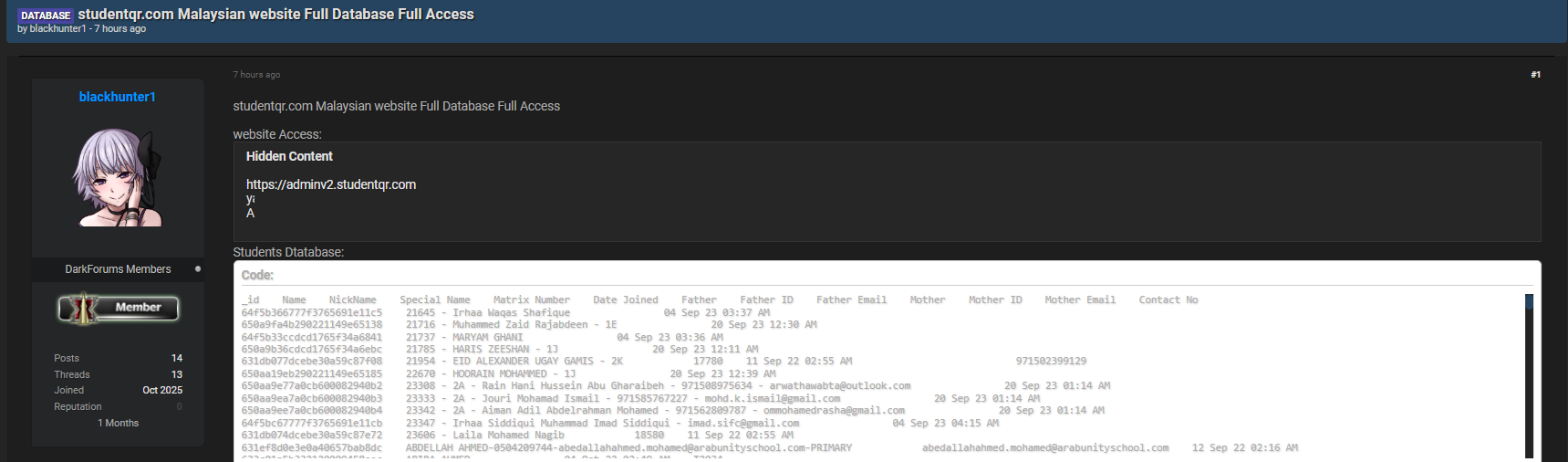
Overview of the Alleged Incident
In December 2025, a dark-web user claimed responsibility for releasing what they described as a student database leak, allegedly taken from a Malaysian educational platform. Although the authenticity of the claim remains unverified, discussions around the potential personal data exposure intensified quickly. Such leaks—real or rumored—often generate fear because educational records include sensitive identifiers, parental information, and contact details. Reports of this kind highlight how vulnerable academic systems can be when database security is not properly maintained.
How the Claim Emerged on Dark-Web Communities
The post appeared on a well-known underground discussion board, where similar cybersecurity incident claims are frequently shared. While the content of the post cannot be independently confirmed, its structure followed a familiar pattern: screenshots, sample lines of alleged database entries, and a public release tag. 🛑
Cybersecurity analysts frequently warn that the dark web hosts a mixture of real breaches, exaggerated claims, and complete fabrications. As such, determining the credibility of a student database leak requires technical review and institutional transparency.
Key Indicators Seen in the Alleged Leak
If true, the leak would fall under what experts call an educational records compromise, involving elements such as:
- Student names and internal identifiers
- Enrollment information
- Parent or guardian contact details
- Internal system timestamps
These categories reflect the type of information often targeted because they hold long-term value for identity-related fraud. Even when data sets appear incomplete, threat actors may combine them with other sources to build detailed identity profiles. This is why any Malaysian student data leak analysis must include broader ecosystem risks.
Why Educational Platforms Are High-Value Targets
Educational institutions manage large volumes of personal information, frequently across outdated systems or fragmented infrastructure 😟. This makes them appealing to attackers seeking easy entry points. Key factors increasing vulnerability include:
- Insufficient encryption
- Legacy database architecture
- Misconfigurations during updates or migrations
- Limited cybersecurity budgets
- High user turnover (students entering/leaving annually)
Because of these weaknesses, even unverified claims of a Malaysian data breach can trigger intense scrutiny—and rightly so.
Similar Cases in the Education Sector
A related incident occurred at UCL, where attackers reportedly leaked over 45,000 student and staff records in a darknet forum. The similarities in target type, leak presentation, and motivation reflect a broader trend affecting educational institutions worldwide.
🔗 https://darknetsearch.com/knowledge/news/en/ucl-data-breach-revealed-45000-records-leaked-in-darknet-forum/
Risk Assessment: What Could Be Affected?
When dealing with a suspected student database leak, risks vary depending on what categories of data might have been exposed. Potential consequences include identity theft, SIM-swap risks, targeted phishing, and social engineering. 📛
A common question arises:
“Does every data leak automatically lead to identity theft?”
Answer: No—but any leak increases the probability of identity-related fraud, especially when multiple datasets are combined. Attackers analyze and cross-reference leaked information across various environments to maximize exploitation opportunities.
Checklist: How Institutions Should Respond
Here is a practical checklist institutions can follow when confronted with a potential breach claim:
- Verify the authenticity of the data sample.
- Run system-wide integrity and access audits.
- Reset administrator credentials immediately.
- Notify users transparently if indicators of compromise are confirmed.
- File a breach report with the appropriate regulatory body.
- Engage an independent cybersecurity firm for forensic review 🛡️.
These steps reflect international best practices for handling cybersecurity incidents in educational environments.
Expert Commentary on the Trend
Cybersecurity researchers consistently emphasize the growing pattern of attacks involving schools, universities, and digital learning platforms. One analyst explains:
“Educational records have long-term value. While passwords can be reset, personal identity data cannot. That permanence makes the sector highly vulnerable.”
This underscores the importance of reinforcing digital protection frameworks against any type of student database leak or related threat.
Preventive Strategies for Individuals
Even when authenticity is uncertain, users can take precautionary steps to protect themselves from potential personal data exposure:
- Enable multi-factor authentication on all accounts
- Avoid reusing passwords
- Monitor mobile and banking accounts for unusual activity
- Be cautious of unsolicited calls or emails
Simple actions like these dramatically reduce the impact of a Malaysian data breach on everyday users. 💡
Practical Tip for Parents and Students
If you are part of an institution that might have been mentioned, always request an official statement before taking any action. Institutions are legally required in many jurisdictions to disclose confirmed breaches. Never rely solely on screenshots or user-generated claims circulated online.
Conclusion
The alleged Malaysian data breach discussed across online communities highlights the increasing vulnerability of digital education platforms and the growing sophistication of cyber threats. Whether verified or not, such claims remind institutions of the urgent need to prioritize data protection, adopt tighter security controls, and maintain transparency with users. Students, parents, and educators must also remain vigilant to minimize risks associated with potential personal data exposure.
To stay informed and prepared:
👉 Discover much more in our complete guide
👉 Request a demo NOW
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.

