➤Summary
The Under Armour data breach has rapidly become one of the most alarming cybersecurity incidents affecting the Retail industry this year 😨. During a routine security operation, the Kaduu team uncovered evidence of the attack in dark web forums, revealing discussions that referenced a massive leak attributed to the Everest ransomware group. According to early reports—such as the detailed coverage published by TechRadar, which stated that hackers claim to have hit Under Armour in a large-scale breach (TechRadar)—the attackers allegedly exfiltrated more than 343 GB of company data.
Further confirmation comes from analysis shared by eSecurityPlanet, which reported that Everest ransomware publicly alleged responsibility for the breach and claimed the stolen dataset includes customer histories, internal documents, and employee records (eSecurityPlanet). These findings have intensified concerns over the brand’s data protection measures and highlighted evolving threats across modern retail operations 🔐.
Massive Scale of the Alleged Cyberattack
The Everest ransomware group posted claims across multiple underground markets, announcing that they successfully infiltrated Under Armour’s systems and extracted hundreds of gigabytes of data 📁. Their public statements on leak channels indicate that the stolen files include extensive consumer data logs, internal analytics, employee documents, and operational metadata.
For an international brand like Under Armour, the volume and type of exposed information signal a major breach of both operational security and consumer trust. The cybercriminals emphasize that their goal is not simply financial gain—though a ransom demand is almost guaranteed—but strategic leverage and reputational damage intended to force compliance.
In today’s cyber-extortion ecosystem, data theft has become more dangerous than system encryption. Threat actors increasingly focus on collecting actionable intelligence—precisely the kind of information Under Armour customers may now have exposed.
What Data Was Allegedly Stolen?
According to the dark web listing, the 343 GB of stolen content includes:
- Customer shopping histories
- Email addresses and phone numbers
- Purchase timestamps, SKUs, and pricing information
- Regional location data and store preferences
- Marketing logs and campaign metadata
- Deep-link tracking analytics
- Employee contact details and personnel files
- Internal company reports, store documents, and product data 📊
Such an extensive dataset goes far beyond basic PII. It includes behavioral insights, marketing performance data, device interaction logs, and purchase pattern analytics—elements often used by major brands for growth strategies. Unfortunately, in the wrong hands, these insights could be weaponized.
Forum Post Proof and Data Sample Proof
Below is the required space for adding evidence of the discovered listing:
Forum where it was found: Nohide.io
Author: shenron
Discovered by: Kaduu Team during a routine security operation
Forum Post Proof:
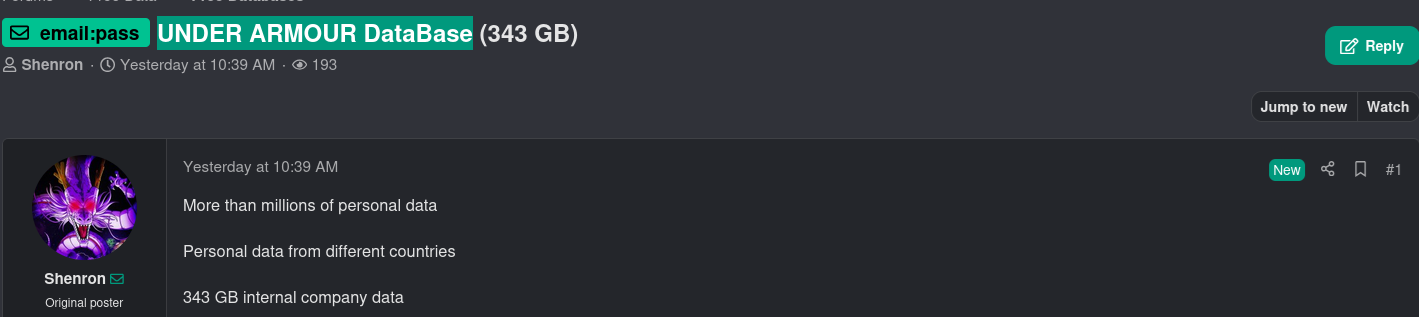
Download Data Proof:
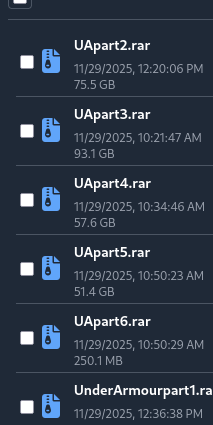
Is Everest Ransomware a Credible Threat Actor?
A notable precedent is the recent breach at Coupang — one of South Korea’s largest ecommerce platforms. According to DarknetSearch, the Coupang data breach exposed personal details of 33.7 million customers including names, email addresses, phone numbers, shipping addresses, and order histories — though payment data and passwords reportedly remained safe. This incident has become a prime example of a case study dark web monitoring scenario, showing how quickly stolen retail-industry data can be monetized or weaponized. The parallels between Coupang’s leak and the alleged Under Armour data theft reinforce how a well-organized cyberattack by a group like Everest can easily lead to large-scale exposure when companies lack robust data protection and real-time monitoring.Key Risks for Affected Customers
Victims of such a breach may face several immediate and long-term threats, including:
- Highly personalized phishing attacks
- Identity theft using exposed contact data
- Account takeover attempts
- Unauthorized access to third-party services
- Behavioral profiling leading to targeted fraud
Because the attackers reportedly obtained deep-link tracking metadata and marketing logs, cybercriminals could create fake order confirmations, shipping updates, or reward program messages, making scams extremely convincing 😬.
Practical Tip to Protect Yourself
To enhance your digital safety, follow this quick checklist 🛡️:
Security Checklist
- Reset your Under Armour account password
- Enable two-factor authentication
- Scrutinize unusual emails or messages
- Avoid clicking new tracking links
- Monitor bank and credit activity
- Review app permissions and connected devices
These simple but effective steps significantly reduce your exposure risk.
Are Customers in Immediate Danger?
Yes—but primarily from indirect attacks.
Direct, immediate financial theft is unlikely unless payment information was directly linked to your Under Armour account. However, large-scale phishing campaigns, fraud attempts, and social engineering attacks often follow major corporate breaches.
Question: Should customers freeze their credit?
Answer: Credit freezing is optional but recommended if you receive suspicious activity alerts or if your personal financial information was stored in your retail profile.
Expert Insight on Data Protection Failures
Modern cyberattacks focus on analytical datasets, not just customer profiles. Marketing logs, behavioral analytics, and internal reports are incredibly valuable to attackers. These datasets allow them to craft detailed social engineering campaigns that mirror genuine brand interactions.
For the Retail industry, this breach highlights the need for advanced data protection protocols, including encryption-at-rest, segmented databases, and secure behavioral analytics storage. Companies must also treat marketing data with the same security standards applied to financial information.
Checklist for Companies to Strengthen Security
To avoid similar incidents, organizations should implement:
- Strong network segmentation
- Continuous endpoint monitoring
- Dark web surveillance
- Rapid incident response models
- Employee phishing training
- Zero-trust authentication models
- Marketing data encryption
Conclusion
The Under Armour data breach is a powerful reminder of how vulnerable global Retail industry companies have become in today’s digital era 🚨. With 343 GB of allegedly stolen data—covering customer histories, marketing analytics, and internal files—millions may face long-term cybersecurity risks. This incident emphasizes the urgent need for robust data protection systems, smarter user awareness, and corporate transparency.
As cybercriminals evolve and extortion tactics grow more sophisticated, customers must remain proactive and informed, while companies must adopt stronger defenses and real-time monitoring solutions.
Discover much more in our complete guide
Request a demo NOW
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.

