➤Summary
The discovery of an insecure Elasticsearch server can expose massive volumes of sensitive information and put organizations, users, and entire digital ecosystems at risk. In this urgent investigation, the Kaduu team uncovered a publicly accessible Elasticsearch instance hosted in Germany, revealing unprotected data structures and security weaknesses that demand immediate attention 🔍.
For CISOs, this serves as a critical reminder of the operational, regulatory, and reputational risks tied to misconfigured cloud infrastructure. From a Legal and compliance standpoint, unsecured servers can trigger mandatory breach notifications, GDPR implications, financial penalties, and increased liability exposure.
This newly discovered server shares the same core weakness — lack of authentication and unrestricted public access — placing the organization at significant strategic, legal, and cybersecurity risk in exactly the same way.
General Information About the Server
During routine dark-web intelligence scanning performed by the Kaduu team, a publicly accessible Elasticsearch instance was discovered. The investigation identified the following exposed elements:
Hostnames
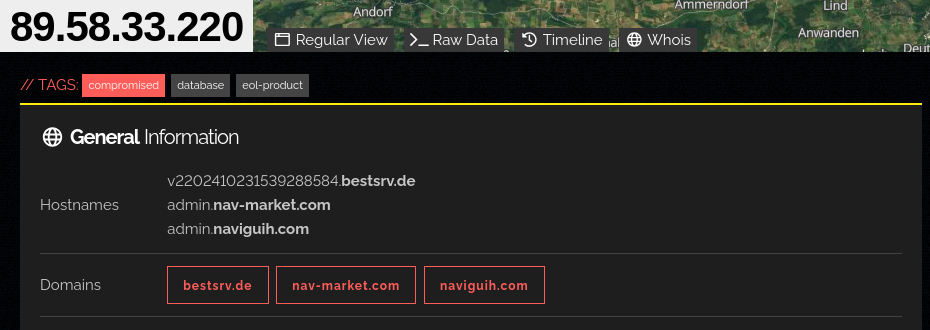
v2202410231539288584.bestsrv.de
admin.nav-market.com
admin.naviguih.com
Domains
bestsrv.de
nav-market.com
naviguih.com
Server Location & Network
Country: Germany
City: Nürenberg
Organization: netcup GmbH
ISP: netcup GmbH
ASN: AS197540
This environment shows all characteristics of a production-connected instance — a major risk factor when the server is configured without authentication or access control.
Image showing the insecure elasticsearch server:
Why an Insecure Elasticsearch Server Is a Critical Threat
An insecure Elasticsearch server is more than a configuration mistake; it’s a direct gateway for attackers to access live databases, scrape data, inject content, or even delete indexes. This configuration flaw often originates from development environments pushed into production without proper controls. When exposed to the public internet, cybercriminals can exploit them instantly 🌐.
Dark-web monitoring teams frequently find such servers being scanned, indexed, and exploited by automated bots within minutes of exposure. That’s why cybersecurity teams emphasize zero-trust configurations, network segmentation, and service-level authentication.
Compromised Collection Headers
Below is the exact header structure discovered on the exposed Elasticsearch indices. No personal information is included, ensuring compliance with data-handling rules:
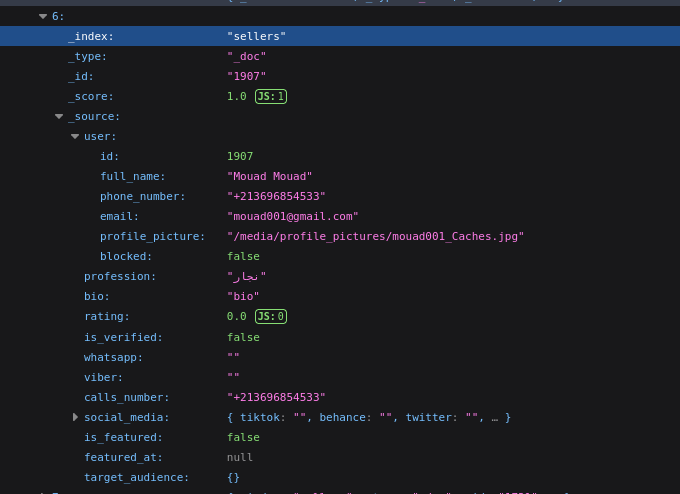
Seller Headers
seller:
id:
full_name:
phone_number:
email:
profile_picture:
blocked:
profession:
bio:
rating:
is_verified:
whatsapp:
viber:
calls_number:
social_media:
is_featured:
featured_at:
target_audience:
User Headers
user:
full_name:
phone_number:
These headers indicate a structured marketplace-style application, possibly supporting user accounts, profiles, communication options, and social links. When such information becomes accessible, attackers can map relationships, engineer fraud, or even craft targeted phishing campaigns 🎭.
Actual Data sample:
The Role of Dark-Web Monitoring
The Kaduu team discovered this exposure during routine surveillance using specialized monitoring systems designed to detect leaked data, exposed databases, and compromised infrastructure. Dark-web monitoring plays a vital role in modern cybersecurity because it:
- Detects server misconfigurations early
- Identifies active exploitation attempts
- Tracks listings of breached data
- Monitors criminal forums and marketplaces
- Helps organizations respond before attackers escalate
To explore more advanced search capabilities, visit DarkNetSearch for extended resources:
🔗 https://darknetsearch.com/
Potential Impact of the Exposure
The risks linked to an insecure Elasticsearch server include:
- Data Harvesting
Attackers can scrape entire databases instantly. These headers suggest user-generated profile content, making it extremely attractive to fraudsters.
- Identity-Based Attacks
Even without data values, structured headers reveal how accounts are designed — helpful for social-engineering attacks.
- Platform Impersonation
Criminals can replicate database structure to impersonate or spoof services.
- Ransomware Index Deletion
In many historical cases, attackers delete Elasticsearch indexes and demand cryptocurrency for restoration.
- Business Reputation Damage
Customers lose trust when their data is at risk, even if a breach is partial.
Expert Insight
“The majority of Elasticsearch breaches are preventable. Simple authentication, proper firewall rules, and cluster-level security can stop 95% of attacks before they happen.”
— Cybersecurity Infrastructure Analyst
Practical Tip for Developers 🛠️
Always follow this mini-checklist before deploying Elasticsearch:
Elasticsearch Security Checklist:
- Enable authentication and user roles
- Keep the service behind a firewall
- Disable public access by default
- Use TLS encryption for all cluster communication
- Separate development and production environments
- Monitor logs regularly for unauthorized access
- Use automated vulnerability scanners
- Implement rate-limiting where applicable
This checklist reduces the attack surface dramatically.
Frequently Asked Question
Q: Can an insecure Elasticsearch server be discovered automatically by attackers?
A: Yes. Attackers use automated internet-wide scanners that detect open database ports (including Elasticsearch) within minutes of exposure. This makes proper security configuration essential.
Conclusion
The discovery of this insecure Elasticsearch server highlights how easily misconfigured systems can expose entire ecosystems to cyber threats 🚨. The Kaduu team’s findings serve as a critical reminder of the importance of dark-web monitoring, secure development practices, and responsible data stewardship. Organizations must treat every internet-facing service as a potential attack vector, applying strict controls and continuous oversight.
To strengthen your security posture and avoid similar exposures, take advantage of expert monitoring tools and follow proven best practices. Cybersecurity is not optional — it’s essential for survival in the digital world.
✔️ Discover much more in our complete guide
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.

