➤Summary
Blavity cybersecurity discussions in 2025 continue to influence how digital-first platforms evaluate operational risks, especially as media ecosystems expand across newsletters, mobile apps, cultural content, and large creator-driven communities 📱. As media companies scale, the importance of data protection, reinforcing system configurations, and strengthening digital tools becomes central to daily operations. In this extended analysis, we explore how Blavity cybersecurity conversations mirror the challenges faced by the broader industry—highlighting misconfiguration risks, CRM exposures, and the urgent need for improved media company security frameworks. The goal is to help teams understand vulnerabilities in modern marketing systems, improve digital safety, and adopt practical tools to secure their infrastructure 🛡️.
With more companies relying on third-party SaaS platforms, automation tools, and integrated CRM architectures, the threat landscape continues to evolve. Even small system missteps—like forgotten API keys or outdated permissions—can escalate into significant operational risks. That is why learning from case studies, expert opinions, and platform audits is essential for building safer content ecosystems. In this article, we break down actionable strategies, practical checklists, and forward-looking predictions that can help media companies maintain trust, support compliance, and scale safely without compromising performance or user privacy 🔎.
[Data Post Proof]
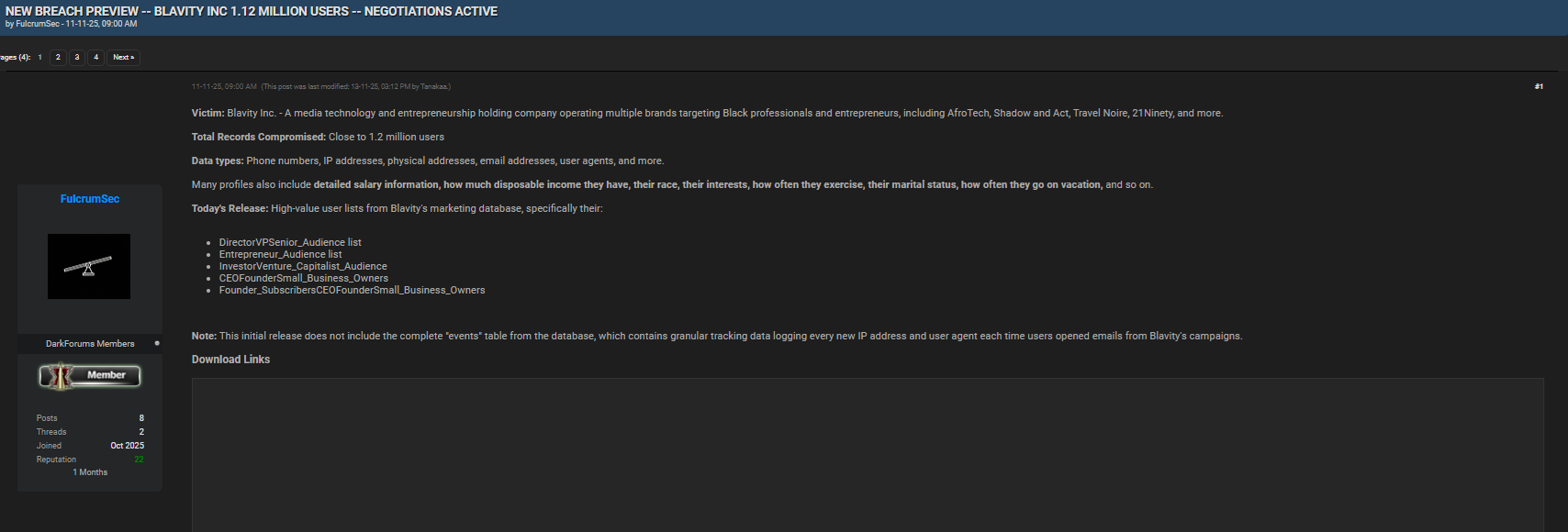
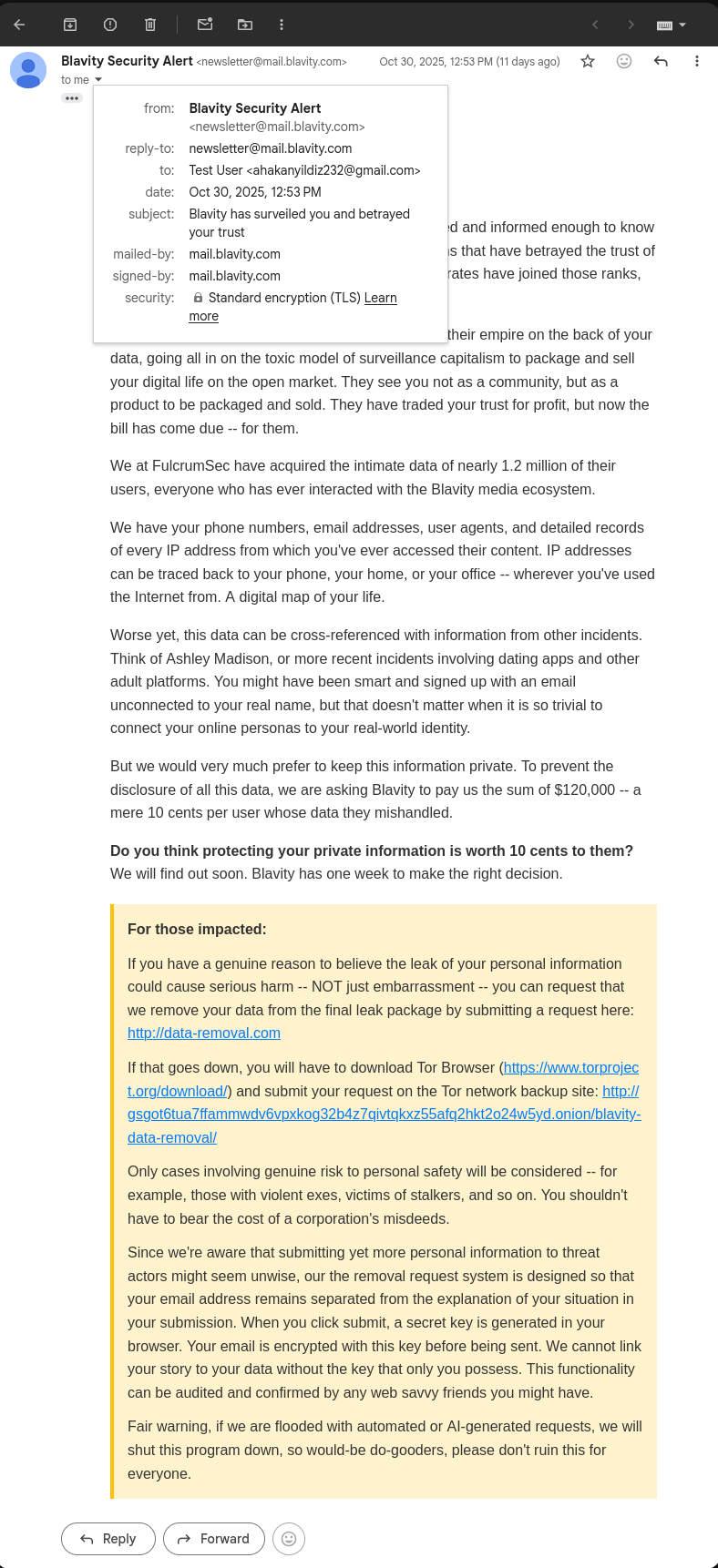
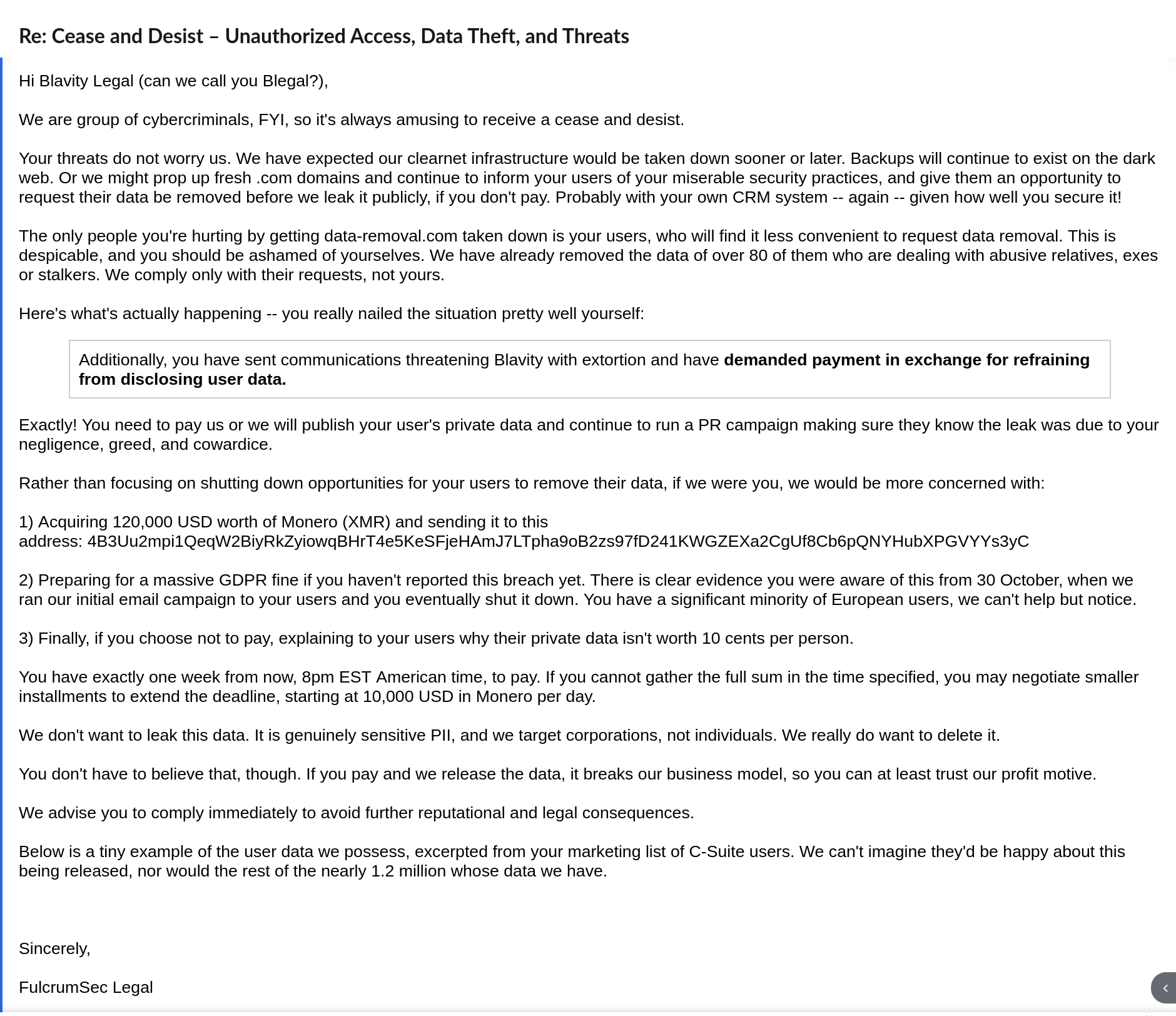
A set of email exchanges between the reporting party and the company—📧 screenshots added below—document the initial notification, the company’s acknowledgment 📨, and the steps taken to verify and address the issue 🔍.

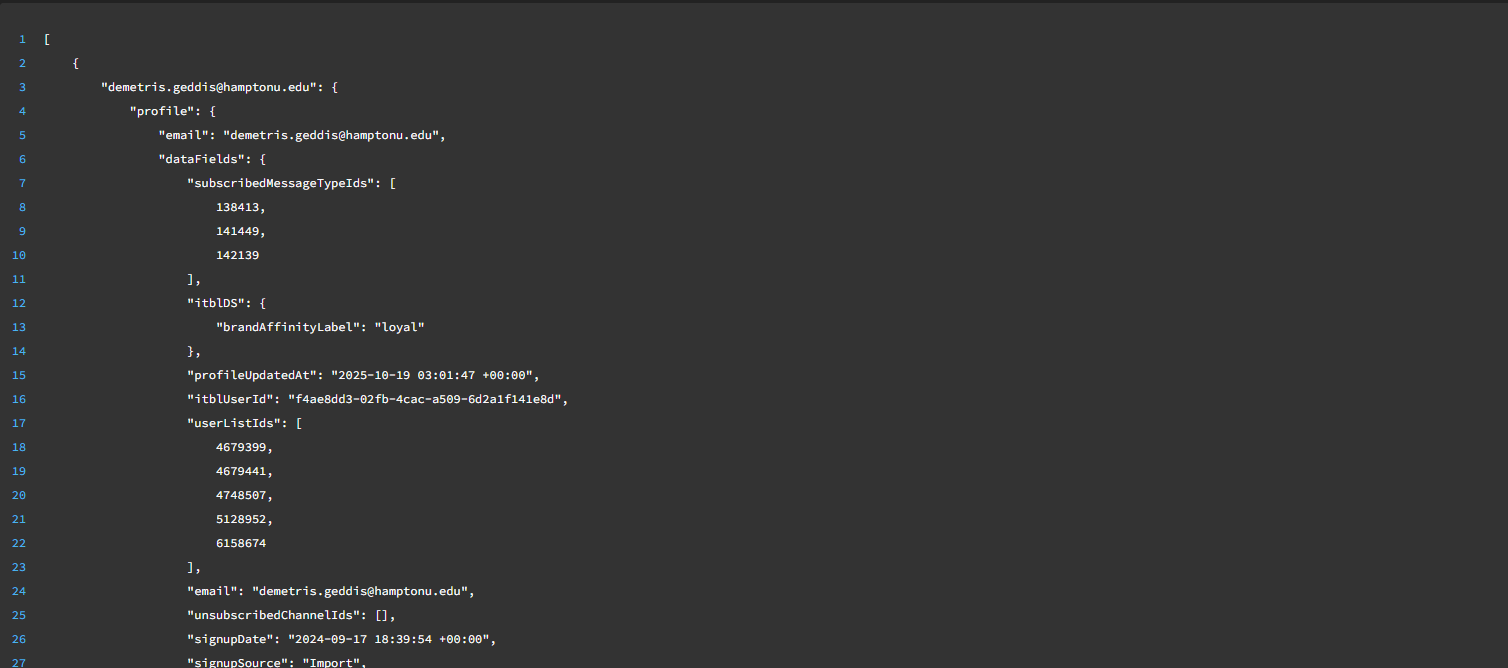
Understanding CRM Vulnerabilities in Modern Media
In the world of content publishing, CRM systems serve as the backbone of audience engagement. They consolidate user data, preferences, email interactions, behavioral analytics, and campaign history into a single ecosystem. However, when these systems are misconfigured or when access tokens are inadvertently exposed, even a well-developed CRM structure becomes a potential risk. This is why Blavity cybersecurity discussions emphasize the relationship between system reliability and data protection. Understanding how CRM vulnerabilities affect media company security helps industry teams strengthen their internal processes, align their workflows, and reduce the potential for unauthorized access.
CRM misconfigurations often happen silently. A developer may push a test configuration into production. A marketing manager may overlook an outdated vendor permission. A new integration might require access scopes that exceed original requirements. When these oversights go unnoticed, attackers may exploit publicly accessible endpoints, weak authentication processes, or unnecessarily exposed credentials. As one analyst notes, “CRM platforms are only as secure as the teams managing them.” This simple statement reflects a deeper truth: platform complexity increases risk unless supported by strong internal governance, periodic audits, and clear operational standards 💡.
How Marketing Infrastructure Becomes a Target
Marketing infrastructure, while essential, is one of the most attractive elements of a digital ecosystem because it connects multiple pieces of the business. It links CRM systems, email automation tools, ad platforms, analytics dashboards, and user tracking frameworks. Blavity cybersecurity insights show that attackers often target these interconnected systems not because of the content itself but because of the valuable metadata behind it—device information, engagement records, traffic logs, and demographic segments.
This is why improving media company security means securing not just the content platform but also the behind-the-scenes marketing stack. Access credentials, webhook endpoints, partner integrations, and automated pipelines should be reviewed on a regular schedule. Outdated API keys are among the most common vulnerabilities because they remain active long after the original configurations have been updated or removed. Rotating keys and enforcing least-privilege access models significantly reduces exposure and strengthens marketing systems security.
Strong marketing infrastructure protection helps ensure that audience data remains safe, campaign insights stay confidential, and operational continuity is preserved—even as platforms grow more complex. Teams that prioritize digital safety build trust with their users and enhance the efficiency of their internal systems.
Practical Tip: Essential Security Checklist
🧩 Use this quick checklist to reinforce media company security from the inside out:
• Conduct monthly permission audits across all CRM and marketing tools
• Rotate API keys, OAuth tokens, and platform credentials on a fixed schedule
• Require multi-factor authentication (2FA) for all users
• Secure sensitive data using both encryption at rest and encryption in transit
• Set up anomaly-based monitoring to detect unusual behaviors
• Use role-based access control to narrow permissions
• Document system configurations and update them quarterly
• Train every team member on digital safety basics
This checklist helps organizations build habits that reinforce long-term resilience. Even small improvements—like deactivating unused vendor accounts—can significantly reduce risk.
The Strategic Value of Data Protection in Media
Blavity cybersecurity conversations demonstrate why user trust is the foundation of any media brand. Every interaction—whether someone signs up for a newsletter or engages with a mobile app—relies on the assumption that personal data will be handled with care. Media company security requires more than just responding to threats. It demands building a culture of protection where security becomes a shared responsibility across teams.
Data protection adds strategic value in several ways:
• It strengthens brand reputation
• It reduces regulatory risk
• It enhances customer loyalty
• It improves operational transparency
• It attracts higher-value partnerships
Companies that proactively reinforce their data management frameworks can scale faster and operate more confidently in competitive markets.
The Role of Employee Training in Reducing Risk
Human error remains one of the most overlooked vulnerabilities. Whether someone accidentally exposes a token, uses weak credentials, or misconfigures a service, the consequences can be significant. That is why cybersecurity lessons for media brands often include ongoing training programs. When employees understand how attackers operate, how phishing attempts are crafted, and how systems must be configured, the overall risk level drops dramatically.
Training should be consistent, simple, and role-specific. Teams working with CRM tools need specialized guidance. Developers need secure coding resources. Marketing teams need to understand platform permissions and data privacy obligations. When training is integrated into daily operations, companies build a culture where secure behavior becomes second nature.
What Does This Mean for the Future of Media Security?
The central question facing today’s leaders is simple: Can media companies grow without raising their exposure to risk?
Answer: Yes—if they prioritize forward-thinking strategies, proactive audits, and continuous improvement 🚀.
Platforms like CISA offer comprehensive guidance for organizations seeking to enhance their cybersecurity frameworks. For deeper research into security trends, resource hubs like https://darknetsearch.com/ provide reference materials that help professionals stay informed about emerging threats and preventative strategies.
As media companies adopt more automation, more integrations, and more data-driven workflows, the stakes continue to rise. The future belongs to platforms that combine creativity with security, innovation with responsibility, and scale with protection.
Strengthening Tomorrow’s Media Ecosystems
Blavity cybersecurity discussions reveal a clear message: modern media companies need to invest in transparent data practices, resilient infrastructures, and dynamic security frameworks to stay competitive. As teams commit to stronger internal governance, structured audits, and continuous system monitoring, they create ecosystems where users feel safe, operations run smoothly, and growth becomes sustainable 🔍.
Security is not a one-time project—it is an evolving commitment. By integrating strong media company security practices into everyday workflows, brands demonstrate leadership, responsibility, and long-term vision.
Discover much more in our complete guide
Request a demo NOW
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.

