➤Summary
The University of Pennsylvania data breach has become one of the most discussed cybersecurity incidents of 2025. According to multiple sources, including a post made on Darkforums.st by a user named upennleak, the attackers claim to have exfiltrated sensitive personal information belonging to over 1.2 million students, alumni, and donors. 💥 The group published what they called an “Appetizer Leak” — a teaser of the larger dataset that they say will be released in coming months. This incident, now known as the University of Pennsylvania data leak 2025, raises major concerns about the security of academic institutions and their ability to protect private data.
What Happened in the University of Pennsylvania Data Breach
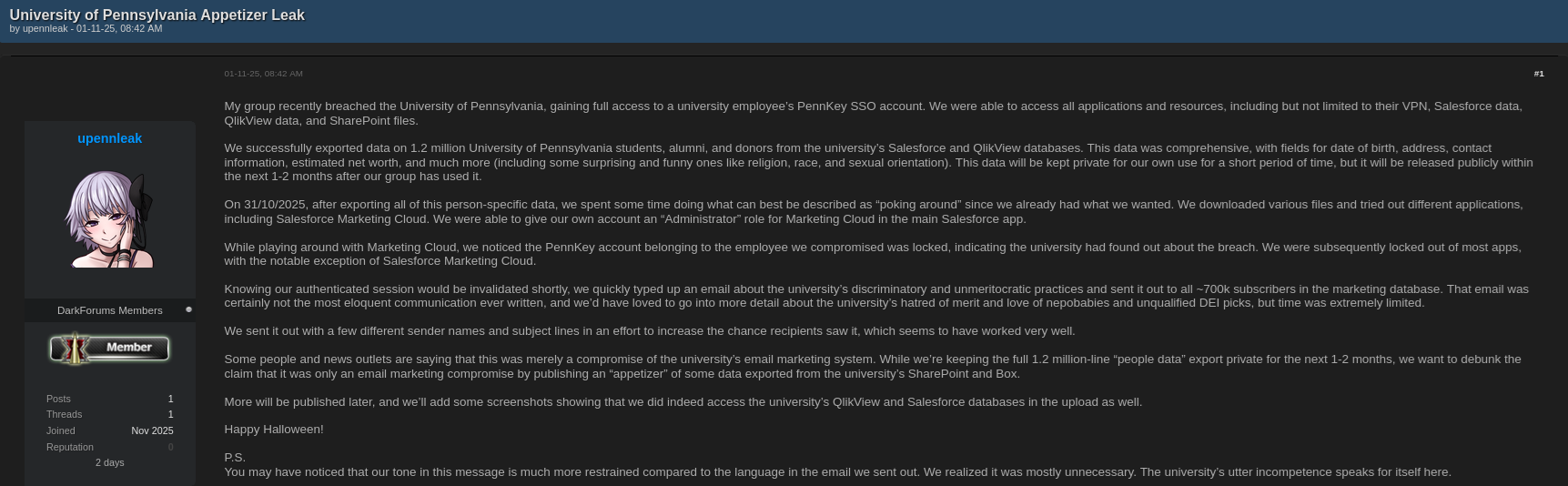
On 01 November 2025, a forum user known as upennleak posted a thread on Darkforums.st describing in detail how their group allegedly breached the university’s systems. They claimed to have gained full access to a PennKey SSO account belonging to a university employee. Through this access, the group reportedly reached internal applications, VPNs, Salesforce, QlikView, and SharePoint environments. 😱
According to their own statements, they were able to export a vast database containing personal and financial information, such as:
- Names, dates of birth, and addresses
- Email and phone contact details
- Estimated net worth
- Demographic data such as religion, race, and sexual orientation
This revelation is alarming, not only because of the sensitivity of the data but also due to its completeness — the records seem to span both current and former university affiliates. Cyber experts say such details could be used for identity theft, phishing campaigns, and large-scale social engineering.
The “Appetizer Leak” and the Group’s Statement
In their post, upennleak described how after exporting the data, they experimented with internal tools such as Salesforce Marketing Cloud, even managing to assign themselves an Administrator role. When the university eventually detected the intrusion and locked the original employee’s account, the attackers still had an open session in Marketing Cloud. Before being fully removed, they reportedly sent an email to over 700,000 recipients, criticizing what they described as the university’s “discriminatory and unmeritocratic practices.” 📧
The message, though short and rushed, reached hundreds of thousands of inboxes and instantly alerted staff, students, and alumni that something was wrong. Security analysts have since confirmed that the incident went far beyond email compromise. The University of Pennsylvania data breach involved unauthorized access to core business applications and databases, suggesting an extensive infiltration rather than a superficial hack.
Forum Post Reference (Darkforums.st)
Proof of Data and “Appetizer Leak” Screenshots
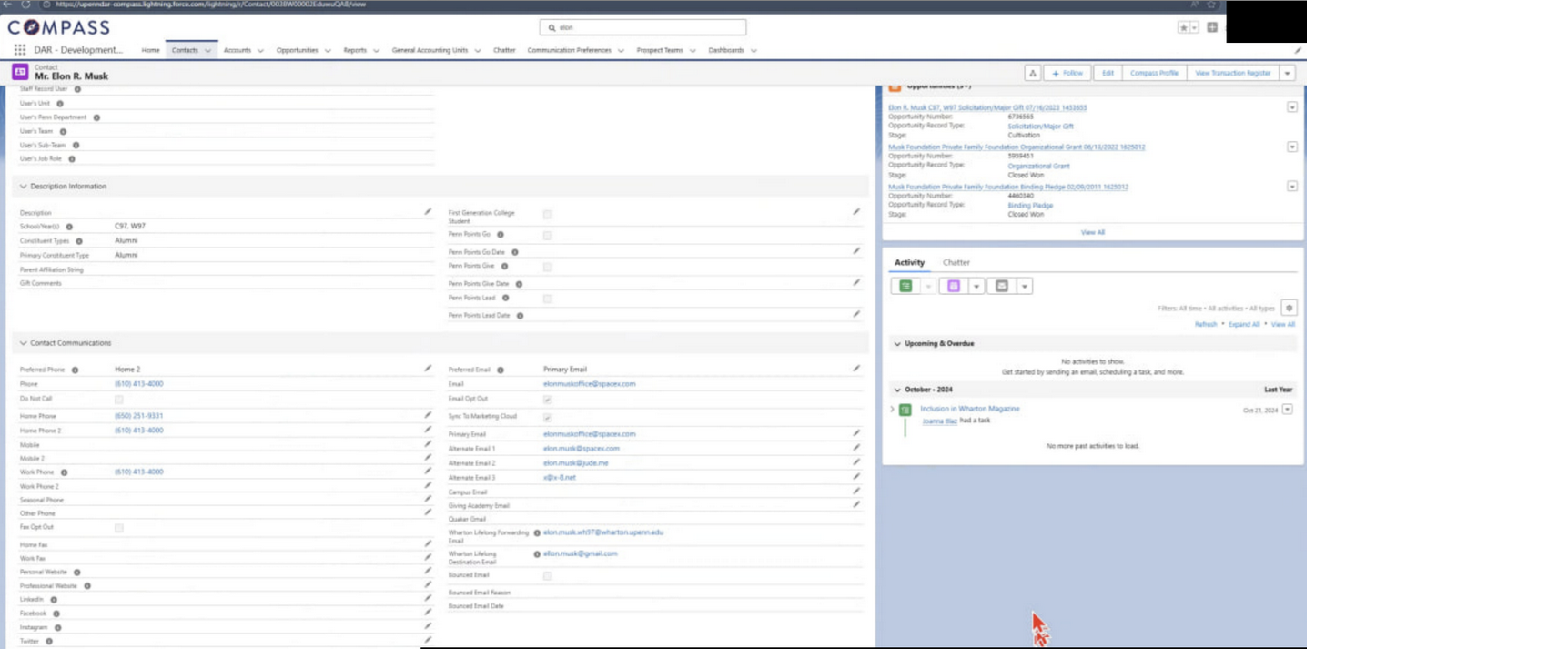
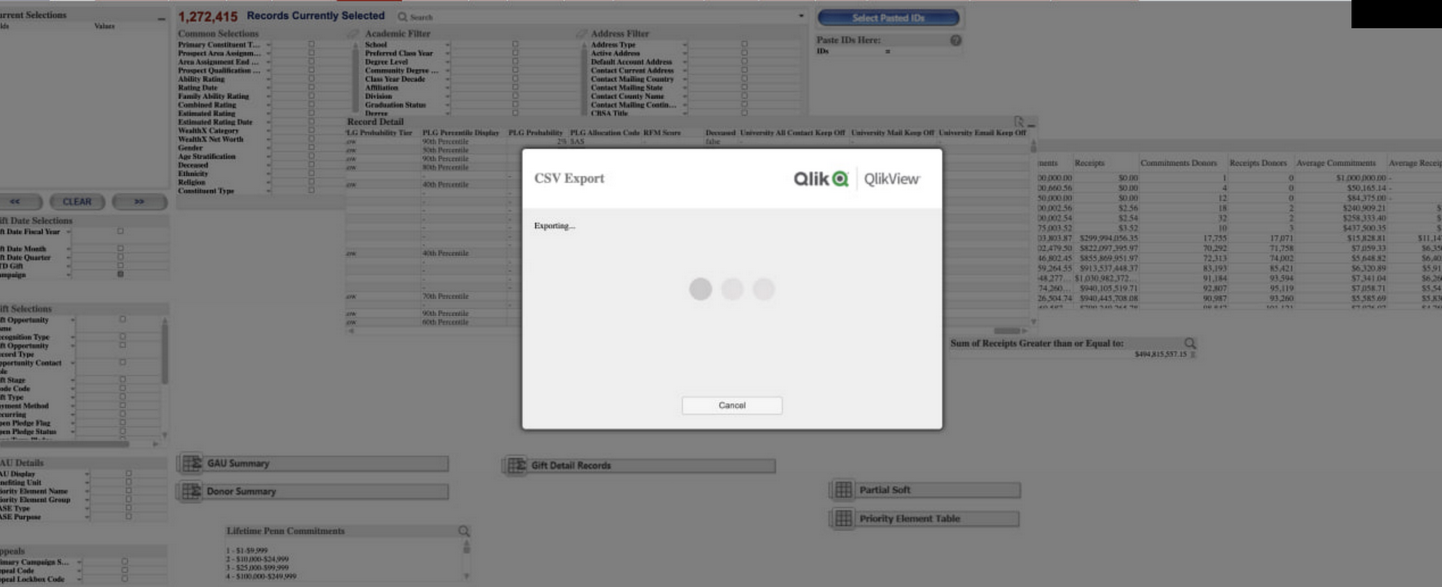
Who Discovered the Leak: The Kaduu Team’s Findings
The Kaduu cybersecurity research team reportedly discovered traces of this database while conducting regular dark web monitoring operations. Their analysts found the thread on Darkforums.st and confirmed that sample files labeled “Appetizer Leak” were available. These samples, they say, appear consistent with authentic university data — though official verification from the University of Pennsylvania has not yet been made public.
Cyber intelligence firm Kaduu emphasized that the leak could expose both individuals and the institution to long-term reputational and legal risks. The UPenn hack demonstrates how even well-resourced universities are becoming prime targets for data-driven cybercrime. 🎯
“Higher education systems have increasingly become data goldmines,” says cybersecurity analyst Marcus Lee from DataSentinel Labs. “They contain not only academic data but also wealth and demographic details that are extremely valuable on illicit markets.”
How the Attackers Accessed the Systems
Based on the attackers’ statement, the intrusion began when they compromised a PennKey single sign-on (SSO) account. Once logged in, they could access cloud-hosted applications, internal analytics platforms, and marketing systems. Using these, they exfiltrated datasets stored in Salesforce and QlikView, along with files from SharePoint and Box.
Such attacks often exploit weaknesses in employee authentication, multi-factor configurations, or reused credentials. Experts suspect phishing, credential stuffing, or token hijacking as possible initial vectors. Once inside, lateral movement to administrative resources allowed the attackers to extract massive datasets without immediate detection.
What Makes the University of Pennsylvania Data Leak 2025 So Serious
While many institutions have faced ransomware or limited data theft, this incident appears different in scale and motivation. The group did not demand ransom or sell the data immediately. Instead, they claim they will “keep it private for their own use for a short period” before a public release.
This statement alone heightens anxiety among students and alumni. The University of Pennsylvania data leak 2025 could expose deeply personal and financial information, making victims vulnerable to fraud and social manipulation. 🚨
The leak’s structure — including wealth estimates and demographic categories — suggests data pulled directly from CRM and analytics tools, rather than general administrative databases. That kind of contextual data is extremely valuable to both criminals and unethical marketing entities.
Could the Attack Have Been Prevented?
Cyber experts argue that stronger access control and more aggressive behavioral monitoring could have reduced the risk. Once the PennKey account was compromised, the attacker’s activities may have mimicked normal usage patterns, delaying detection.
Practical Tip:
To prevent similar attacks, organizations should:
- Require hardware-based MFA for SSO accounts.
- Enforce least-privilege access to sensitive systems like Salesforce and QlikView.
- Conduct real-time audit logging and anomaly detection.
- Establish immediate incident response for credential anomalies.
Implementing these steps could reduce exposure by over 70%, according to industry benchmarks published by the Cybersecurity and Infrastructure Security Agency (CISA).
University Response and Public Reaction
As of early November 2025, the University of Pennsylvania has not issued a detailed public statement about the scale of the breach. However, internal sources suggest that the IT and information security teams have been working continuously to contain the situation. The university is also believed to have contacted law enforcement and external forensic experts.
On social media, reactions range from disbelief to anger. Alumni networks on LinkedIn and Reddit are questioning how such a prominent Ivy League institution could allow such extensive access to sensitive personal information. 💬
Expert Analysis: Why Universities Are Prime Targets
The UPenn hack highlights a growing problem — universities store data on students, staff, donors, and research projects, making them lucrative targets for both cybercriminals and hacktivists. Universities also tend to have complex IT ecosystems, mixing old legacy systems with modern cloud applications.
“Universities have hundreds of entry points,” notes Professor Elaine Roberts, a cybersecurity lecturer at Temple University. “You have researchers, students, contractors, and partners all using the same authentication environment. That’s a nightmare for unified security.”
Checklist: What Affected Individuals Should Do 🛡️
If you believe your information may have been part of the University of Pennsylvania data breach, consider these steps immediately:
- Change all passwords associated with university or personal accounts.
- Enable multi-factor authentication (MFA) wherever possible.
- Monitor credit reports for unusual activity.
- Be cautious of phishing emails referencing the breach.
- Report suspicious contacts pretending to represent the university.
Following this checklist can minimize damage and help prevent secondary exploitation of stolen data.
Broader Implications for Cybersecurity in Higher Education
The University of Pennsylvania data breach isn’t an isolated event. Universities like Stanford, Harvard, and MIT have all experienced cyber incidents in recent years. The combination of personal data, intellectual property, and financial information makes educational institutions especially vulnerable.
The UPenn hack serves as a wake-up call for all higher education systems to modernize their identity and access management frameworks. It also underscores the need for constant dark web monitoring, as early detection can reduce public exposure and mitigate reputational harm. 🔍
The publication of the so-called “Appetizer Leak” shows how attackers are increasingly using psychological tactics — partial data releases — to prove credibility and generate attention before full dumps.
Conclusion: Lessons from the UPenn Data Leak
The University of Pennsylvania data breach illustrates the evolving landscape of cyber threats against academic institutions. From stolen credentials to internal database exposure, this event demonstrates how critical it is for universities to prioritize proactive monitoring and robust authentication.
While the University of Pennsylvania data leak 2025 may not yet have reached the full release stage, the implications are already severe. Students, alumni, and donors must remain alert, while institutions everywhere should treat this as a call to action. ⚙️
Discover much more in our complete guide
Request a demo NOW
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.

