➤Summary
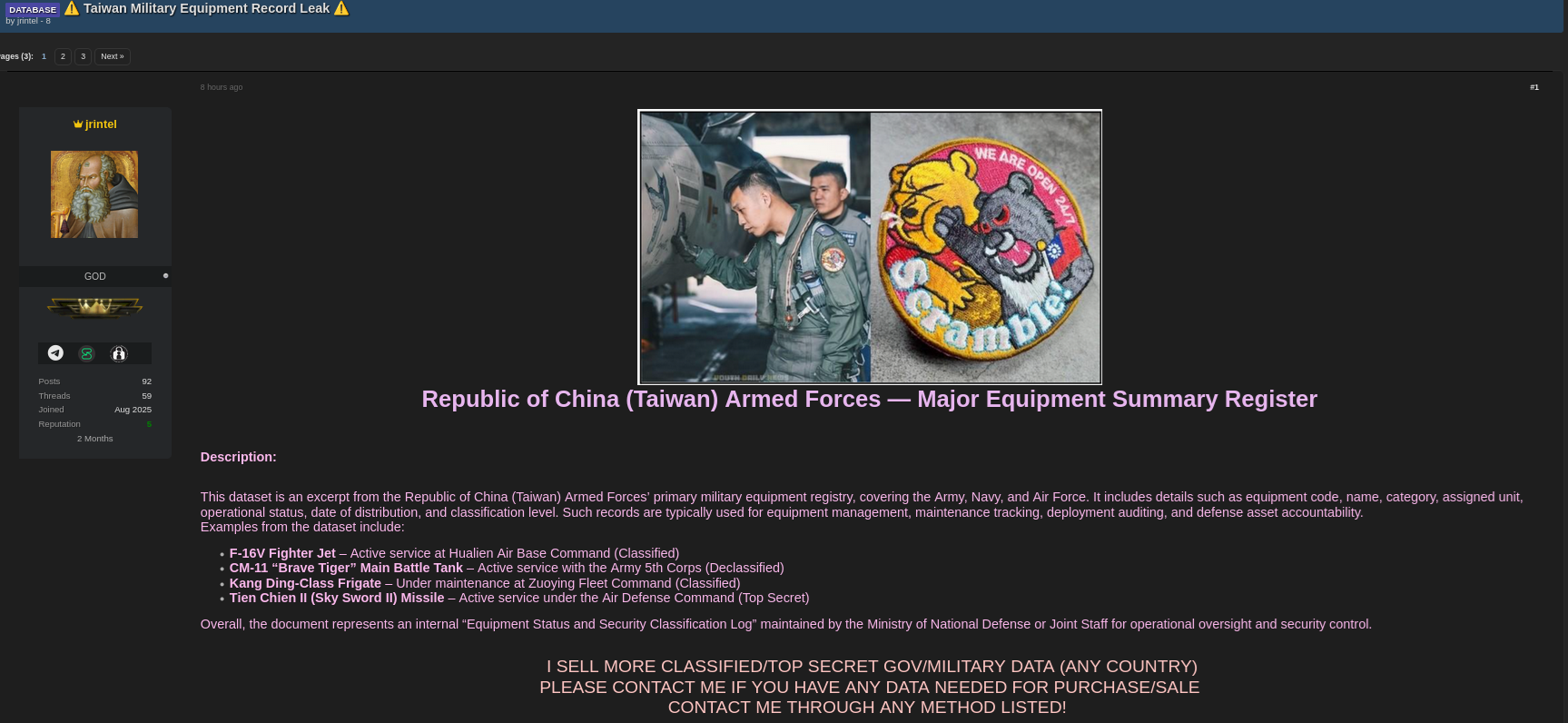
The Taiwan military data breach reported on October 31, 2025, has sent shockwaves through cybersecurity and defense intelligence communities. According to claims shared on a dark-web forum, a dataset titled “Republic of China (Taiwan) Armed Forces — Major Equipment Summary Register” was allegedly leaked online. While the authenticity is still under investigation, the case underscores the growing danger of Republic of China cyberattacks and highlights how digital vulnerabilities can compromise national security 🔐.
The Alleged Leak and What It Contains
A dark-web user known as “jrintel” described the dataset as including codes, names, categories, assigned units, operational status, and classification levels—key data used in military logistics and accountability. Although the Ministry of National Defense has not confirmed the breach, cybersecurity analysts warn that even partial exposure of such metadata could reveal strategic information.
This claim emerges amid escalating regional tensions, where Taiwan’s defense networks face daily cyber incursions and social engineering campaigns.
[Forum Post Proof]
For awareness purposes only, the following illustrative dataset reflects the kind of structured information that may exist in legitimate military registries (note: this table is fictional, used purely for educational demonstration):
| Equipment Code | Equipment Name | Category | Assigned Unit | Status | Issue Date | Classification Level |
| F16V-001 | F-16V Fighter Jet | Aircraft | Hualien Air Base Command | Active | 2023-05-10 | Classified |
| CM11-105 | CM-11 “Brave Tiger” MBT | Armor | Army 5th Corps | Active | 2022-11-14 | Declassified |
| KD-FFG110 | Kang Ding-Class Frigate | Naval | Zuoying Fleet Command | Under Maintenance | 2024-02-19 | Classified |
| TCII-122 | Tien Chien II Missile | Weapon System | Air Defense Command | Active | 2023-08-01 | Top Secret |
Why the Taiwan Military Data Breach Matters
Even without confirmation, the Taiwan Armed Forces equipment registry leak narrative highlights several key issues:
- Operational visibility: Exposing equipment status or unit assignment could allow adversaries to map readiness or deployment cycles.
- Supply-chain vulnerabilities: Identifying maintenance schedules or fleet assignments may compromise defense contractors and logistics providers.
- Escalating state-linked cyber threats: Reports show Taiwan’s government networks face nearly three million daily intrusion attempts, with a sharp uptick in 2025, according to Reuters.
- Disinformation risks: Leaks—real or fabricated—can spread uncertainty and weaken public trust, a trend confirmed by The Record.
- Defense digitalization challenges: Integrating logistics and readiness data across networked systems creates efficiency but expands attack surfaces ⚙️.
The Republic of China Cyberattack Context
The Republic of China cyberattack landscape has evolved dramatically. Taiwan’s defense infrastructure has faced multiple incursions in recent years, including an incident where basic military data was confirmed leaked, as reported by Cybersecurity Review.
Experts note that many dark-web breach claims blend real information with false data to enhance credibility. Whether this latest forum post represents an actual compromise or disinformation, its timing coincides with intensified digital espionage in East Asia 🌏.
Cyber strategist Dr. Michael Sung of the CyberDefend Institute observes:
“Even a simple equipment registry, if cross-referenced with open-source intelligence, can expose deployment readiness. Data classification must go hand-in-hand with cyber-segmentation and personnel training.”
Cybercriminal Motivation and “Proof-of-Leak” Patterns 💰
Threat actors often include “proof” segments—screenshots or CSV snippets—to attract buyers or attention. These “proofs” are not always authentic. Analysts believe the so-called forum proof in this case may have been generic. Nevertheless, such claims can still damage reputations, inspire copycats, or test defense response readiness.
[Sample Leak Proof]

Global Reactions and Verification Challenges
The Ministry of National Defense has yet to release a formal statement verifying the breach. Meanwhile, media coverage and public discourse emphasize vigilance rather than panic. According to a study by the Global Digital Resilience Center, the perception of a leak can cause as much disruption as a genuine compromise.
The Center for Strategic and International Studies (CSIS) tracks dozens of significant cyber incidents each year, many involving defense systems. Its analysis of Asia-Pacific threat patterns shows that Taiwan’s networks are among the most persistently targeted globally (CSIS Report).
A Regional Trend of Escalating Cyber Threats
The Straits Times previously reported on incidents where hackers accessed sensitive military communications and foreign-affairs data through compromised telecom systems (The Straits Times). These breaches illustrate that Taiwan’s defense modernization, while essential, introduces new digital risks requiring continuous oversight.
Checklist: Reducing the Risk of Registry Breaches ✅
To mitigate exposure and prepare for incidents resembling the alleged Taiwan military data breach, cybersecurity experts recommend:
- Adopt Zero-Trust architecture: Ensure role-based access, authentication, and network segmentation.
- Enforce multi-factor authentication (MFA): Especially for users managing sensitive or classified systems.
- Implement continuous monitoring: Deploy AI-driven detection to flag abnormal access or data exfiltration.
- Encrypt and isolate backups: Prevent attackers from tampering with historical defense records.
- Test incident response plans: Simulate “registry-leak” scenarios to improve readiness.
- Vet contractors carefully: Defense contractors are frequent points of compromise.
- Combine cyber and information-security training: Teach personnel to identify social-engineering tactics 🎯.
💡 Practical Tip: Even systems labeled “air-gapped” can be indirectly exposed through maintenance laptops or shared networks—review all connectivity points quarterly.
Could This Be Disinformation?
Some experts suspect the alleged leak could be part of a coordinated information-operations campaign. As The Record explains, hostile cybercriminals frequently release fabricated leaks to manipulate public perception and test response protocols. Whether authentic or not, such incidents are reminders that transparency and calm communication are vital in crisis management 🧠.
Strengthening Collective Cyber Defense
Following similar incidents, international partnerships have intensified efforts to improve resilience. Taiwan cooperates informally with other nations through shared cyber-forensics frameworks, joint exercises, and real-time threat intelligence exchange.
Global authorities such as the Cybersecurity and Infrastructure Security Agency (CISA) also urge continuous updates to security architectures and promote incident-response best practices for defense sectors worldwide.
Frequently Asked Question
Q: Has Taiwan confirmed the leak’s authenticity?
A: As of publication, no. Officials have acknowledged investigations but cautioned against spreading unverified information. This measured stance helps prevent panic while allowing forensic teams to validate technical details.
Key Takeaways and Next Steps
The Taiwan Armed Forces equipment registry leak—whether verified or not—demonstrates how digital transformation introduces new vulnerabilities into defense systems. Cybersecurity is now inseparable from national resilience, requiring proactive measures, transparent communication, and cross-sector collaboration.
Strengthening cyber-defense readiness means balancing technological advancement with stringent data-protection protocols. Every organization—public or private—can learn from Taiwan’s experience to fortify its own systems.
👉 Discover much more in our complete guide at DarknetSearch
🚀 Request a demo NOW
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.

