➤Summary
On 25 September 2025, a new thread popped up on the darknet forum darkforums.st. The post, published by an actor going by KaruHunters, claims that a database linked to Friedrich-Alexander-Universität Erlangen-Nürnberg (FAU / fau.de) was leaked online. The Kaduu team, while running routine checks on underground forums, spotted the post quickly. If accurate, the leak could expose names, addresses, emails, phone numbers, and even images of students and staff. That’s not just worrying—it’s potentially devastating for privacy and trust. ⚠️
What is FAU / fau.de & Why It Matters
FAU is one of Germany’s largest research universities, spread across Erlangen and Nuremberg. Its main domain, fau.de, connects students, faculty, and staff to digital tools ranging from class portals to administrative services. If attackers managed to pull data directly tied to fau.de, then highly sensitive personal information may already be circulating in underground markets. 🎓
In May 2024, FAU’s leadership openly acknowledged the growing cyber threat, stating: “It is not a question of if, but when” universities face attacks. (fau.de) That warning may now look uncomfortably prescient.
The Leak Post & Data Schema
On darkforums.st, KaruHunters published what appears to be the structure of a FAU database. This wasn’t just a vague claim—the post included actual table fields and technical details. 💻
📸 Image of the leak:
What Was Allegedly Exposed
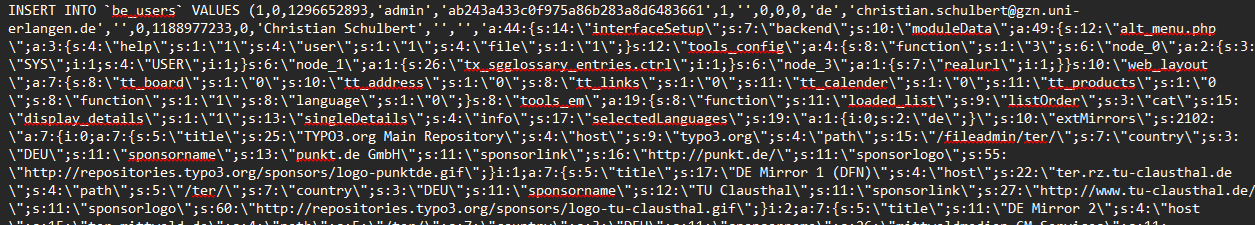
The schema includes:
- Personal details: full names, gender, titles, birthdates, hash password
- Contact info: emails, phone numbers, mobile, fax, usernames, email addresses
- Addresses: street, building, room, city, postal codes, country
- Additional data: company field, website, region, and even profile images (image blob)
- System fields: timestamps, deleted flags, group IDs
Taken together, these fields could paint a complete picture of an individual—far more than what should ever be exposed outside secure systems.
📸 Image of the sample data:
How Could the Leak Have Happened?
Leaks of this scale usually come down to one of a few common scenarios:
- Misconfigured databases left exposed to the internet without a firewall.
- SQL injection attacks against public‑facing sites tied to fau.de.
- Compromised staff accounts through phishing or stolen credentials.
- Unsecured backups stored in the wrong place.
- Third‑party service providers being hacked.
- Old data resurfacing after being stolen in the past. 🔐
The presence of image data and detailed address records suggests attackers had deep access, pointing to compromised credentials or an unprotected server rather than just scraping public info.
External Reference 🌐
For context, German universities have faced similar issues before. The Kaiserslautern University of Applied Sciences was hit by ransomware in 2023, forcing a major IT shutdown. (The Record) Cases like this show that academic institutions remain high‑value targets for cybercriminals.
Why This Alleged Leak is Serious
If the FAU data leak is genuine, here’s what’s at stake:
- 📧 Phishing attacks: exposed emails make social engineering easier.
- 🪪 Identity theft: with names, birthdates, and addresses, criminals can build convincing fake profiles.
- ⚖️ Legal fallout: under GDPR, FAU would be required to inform both regulators and affected individuals.
- 🏫 Reputation damage: trust in FAU’s digital infrastructure would suffer.
- 🔄 Chain reactions: attackers could pivot from this data to other systems or accounts.
Final Thoughts
The alleged FAU data leak posted on darkforums.st by KaruHunters is still unverified, but the technical details shared make it impossible to ignore. Whether this is a fresh breach or old data resurfacing, the risks to privacy and security are very real. 🚨
To follow developments, explore resources like darknetsearch.com for tracking underground activity. For a broader look at massive database exposures worldwide, see Wired’s coverage of mysterious open databases (wired.com).
Discover much more in our complete guide
Request a demo NOW
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.

