➤Summary
Introduction
The Samsung Electronics Germany data leak has shocked both customers and cybersecurity experts. In March 2025, a hacker under the alias @GHNA (also called GEHENNA) posted a large customer-support database on the darknet forum Breachsta.rs. The dataset was later analyzed and described in detail by the author Photon. According to dark web monitors, the compromised information included PII such as names, emails, addresses, support tickets, and shipment tracking numbers, impacting at least 270,000 customers.
The breach, discovered by the Kaduu team during routine monitoring, is directly tied to Spectos GmbH, Samsung’s third-party service provider. One of its employees reportedly fell victim to an infostealer malware attack in 2021, and the stolen credentials were never rotated. This long-standing oversight allowed attackers to access customer tickets years later. With sensitive records exposed, the incident is now listed on Have I Been Pwned and covered by leading outlets such as eSecurity Planet. 📉
Proof of Breach
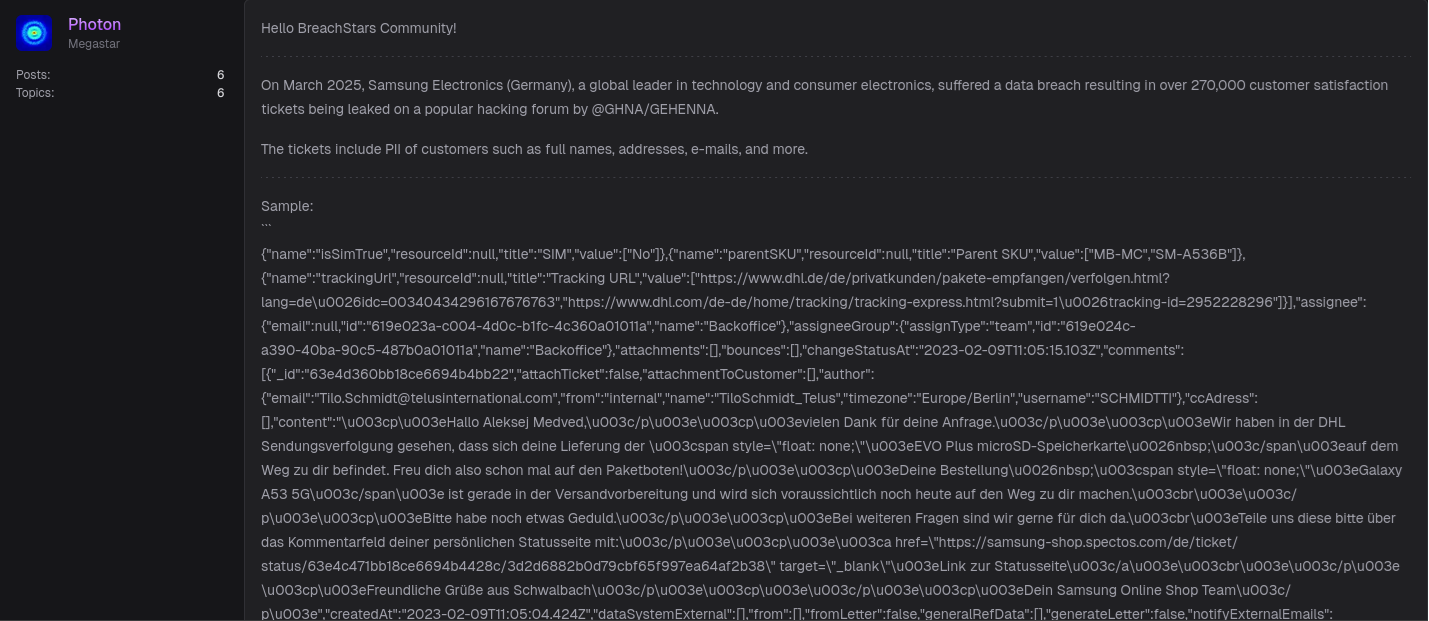
What Was Exposed in the Samsung Germany Data Leak
Reports confirm that the leaked database contained nearly 270,000 customer records, including:
- Full names and salutations
- Email addresses (around 216,000 unique entries)
- Physical addresses
- Support tickets with personal messages
- Order and purchase details
- Shipment tracking numbers
- Ticket IDs, timestamps, and internal employee metadata
This is not just a list of emails. The exposed records combine contact details, purchase histories, and shipping data, making them highly valuable for cybercriminals. 🎯
How the Leak Happened
Investigations traced the breach back to Spectos GmbH, a vendor working with Samsung Electronics Germany. Analysts discovered that:
- Attackers used credentials stolen in 2021 by malware such as Raccoon.
- These credentials were tied to a Spectos employee.
- Because they were never reset, hackers could still use them in 2025.
- Access to the ticketing system enabled the theft of hundreds of thousands of customer records.
This incident highlights a critical supply-chain risk: a vendor’s weak security can expose customers even if the main company has strong defenses. As cybersecurity experts stress, “an organization is only as secure as its weakest supplier.”
Where the Data Appeared Online
The dataset was first published on Breachsta.rs, a darknet forum where stolen databases are routinely shared. 💻 Threat intelligence platforms such as Kaduu quickly flagged the listing during their monitoring cycles. Within days, analysts and journalists confirmed the breach and it was indexed by Have I Been Pwned.
This rapid discovery demonstrates the importance of dark web monitoring. Organizations relying solely on user reports often find out too late, when attackers are already exploiting exposed data. For comparisons and other cases, see DarknetSearch.com.
Risks to Customers From the Leak
The Samsung Electronics Germany data leak creates multiple risks for affected customers:
- Phishing attacks – Emails referencing real order or ticket numbers make scams convincing.
- Identity scams – Names, addresses, and emails improve social engineering effectiveness.
- Delivery fraud – Shipment tracking numbers may be exploited to intercept packages. 🚚
- Warranty fraud – Criminals could impersonate customers for fake warranty claims.
- Account compromise – If victims reused passwords, attackers may access unrelated services.
👉 Practical Tip: If you’ve interacted with Samsung Germany support, search your email on Have I Been Pwned. If it appears, reset your passwords and enable MFA.
How Big Was the Samsung Germany Data Leak?
The numbers confirm a significant exposure:
- 270,000 customer records with detailed support tickets
- 216,000 unique email addresses indexed on Have I Been Pwned
The difference reflects duplicate tickets linked to the same customers. Either way, the impact ranks among the largest European corporate leaks in 2025.
Expert Insights
Cybersecurity analysts point out that the core issue was credential mismanagement. A password stolen in 2021 should never remain active in 2025.
According to security researcher Michael Richter:
“The Samsung Electronics Germany data leak is a textbook case of how ignoring credential rotation creates cascading risks. Attackers don’t need advanced exploits if old credentials still work.”
For further expert analysis, see the detailed coverage on eSecurity Planet.
Here’s a quick checklist for anyone who may be impacted by this breach:
- ✅ Check your email on Have I Been Pwned.
- ✅ Change your passwords and enable MFA on all accounts.
- ✅ Be cautious of phishing emails mentioning Samsung orders.
- ✅ Track packages via official courier websites only.
- ✅ Contact Samsung Germany support for suspicious activity.
Related Breaches and Wider Context
This case belongs to a growing wave of supply-chain data breaches. Attackers increasingly target third-party providers because they often hold sensitive data with weaker defenses. Similar trends appeared in the Ticketmaster incident and the MOVEit supply-chain attack. 🔑
For more breach comparisons and dark web leak monitoring, visit DarknetSearch
Frequently Asked Question
Was payment information exposed in the Samsung Germany leak?
No. Available evidence shows the breach did not include credit card or banking details. The exposed data consisted of PII and support ticket information, which still carries significant risk for phishing and identity fraud.
Conclusion
The Samsung Electronics Germany data leak, carried out by @GHNA (GEHENNA) and documented by Photon, has left 270,000 customers exposed. The incident highlights the serious dangers of third-party failures and credential mismanagement. For customers, the immediate steps are to stay alert to phishing, update passwords, and monitor shipments. For businesses, the lesson is clear: credential hygiene, vendor audits, and proactive dark web monitoring are essential.
💡 Want to learn more?
- Discover much more in our complete guide
- Request a demo NOW
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.

