➤Summary
The Kaduu research team reported recent cyber activities attributed to groups such as NoName057(16), SPIDER-X, Nation of Saviors (NOS), Cyber Team Indonesia (CTI), and Black-Hat Zombies having demonstrated a combination of Distributed Denial of Service (DDoS) attacks and exploitation of system vulnerabilities. These groups have evolved their tactics to increase the impact and reach of their operations in order to disrupt western countries operations and signal their vulnerabilities. The ultimate goal is to undermine economic and political stability in regions supporting Ukraine.
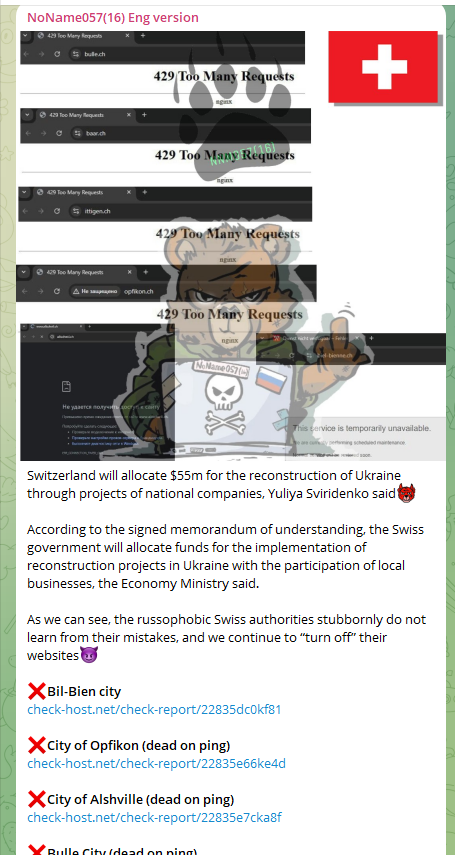
Analyzing Cyberattacks on Swiss Infrastructure by NoName05716
Recent cyberattacks claimed by the pro-Russian hacktivist group NoName05716 have targeted Swiss digital infrastructure. This analysis focuses on the number, size, and severity of these attacks, the types of targets, and their implications for Switzerland’s cybersecurity landscape.
Key Insights and Statistics
- Number of Attacks:
- Based on the Telegram messages, over 50 Swiss websites and online services have been attacked.
- Targets include both public sector institutions and private entities, with many services reported as “dead on ping” or “closed by geo,” indicating either complete shutdown or restricted access to mitigate the impact.
- Type of Targets: The group has focused on critical infrastructure and services, including:
- Government Portals:
- Swiss Federal Tax Administration portal
- Canton and municipal websites (e.g., Lucerne, Zug, Geneva, Davos)
- Swiss AGOV authentication services (used for secure logins across government services)
- Financial Sector:
- Waude Cantonal Bank and Zurich Cantonal Bank portals
- Private Bank Julius Baer authorization system
- Tourism and Transport:
- Davos Congress Center
- POOL-ALPIN cable car services
- Ski resort management in Davos and Klosters
- Utilities and Infrastructure:
- Schaffhausen energy and infrastructure company (SH POWER)
- Swiss Post financial division
- Private Sector and Associations:
- Association for Swiss Asset Management
- SwissCommunity (a platform for Swiss nationals abroad)
- Government Portals:
- Severity of Attacks:
- Service Downtime: Many websites were rendered inaccessible, causing disruptions in government services, financial transactions, and municipal operations.
- Economic Impact: The downtime of financial services like Zurich Cantonal Bank and Waude Cantonal Bank can lead to stalled economic activities, especially given their role in regional and international transactions.
- Tourism Sector Impact: Attacks on Davos infrastructure, including ski resorts and hotels, could significantly harm Switzerland’s tourism-dependent regions during the peak winter season.
- Public Sector Disruption: The inability to access municipal services hampers daily operations for residents and businesses.
Examples of Attacked Systems in Switzerland
Government Services:
- Swiss Federal Tax Administration Portal: Disabling tax-related services impacts government revenue collection and taxpayer interactions.
- Municipal Websites: Cities like Lucerne, Geneva, and Zug reported their portals as “dead on ping,” disrupting local governance and public communication.
Financial Institutions:
- Waude Cantonal Bank: Both the portal and login systems were reported as non-functional.
- Julius Baer Bank: Targeting private banking services highlights an attempt to disrupt Switzerland’s financial stability, given its reputation as a global banking hub.
Tourism Infrastructure:
- Davos Congress Center: Hosting events like the World Economic Forum (WEF), any downtime for this center affects Switzerland’s international reputation.
- POOL-ALPIN and Ski Resorts: These attacks disrupt one of Switzerland’s largest industries, tourism, during the winter season.
Utilities and Public Infrastructure:
- SH POWER: Disruption of energy companies can affect power distribution and essential services in the region.
General Activities NoName057(16) and Attack Patterns:
Distributed Denial of Service (DDoS) Attacks
- Objective: Overwhelm target servers or networks with excessive traffic, rendering services unavailable to legitimate users.
- Methodology: Utilize botnets or coordinated networks of compromised devices to flood targets with traffic. For instance, NoName057(16) has been known to employ such tactics against entities perceived as adversarial to their geopolitical stance.
Exploitation of Vulnerabilities
- Objective: Gain unauthorized access to systems by exploiting unpatched vulnerabilities.
- Methodology: Deploy malware or exploit kits targeting specific vulnerabilities in software or hardware. For example, SPIDER-X has been reported to exploit vulnerabilities in web applications to gain access to sensitive information.
Credential Theft and Lateral Movement
- Objective: Harvest user credentials to facilitate further infiltration within a network.
- Methodology: Utilize tools similar to Mimikatz to extract credentials from memory, enabling attackers to impersonate users and move laterally across systems.
Data Exfiltration and Ransomware Deployment
- Objective: Extract sensitive data for financial gain or strategic advantage.
- Methodology: Deploy ransomware variants that encrypt data and demand payment for decryption keys. Groups like NoName057(16) have been observed using such tactics to disrupt operations and extort victims.
Technical Methods Employed
DDoS Techniques:
- Volumetric Attacks: Generate massive amounts of traffic to saturate the target’s bandwidth.
- Application Layer Attacks: Target specific applications with requests designed to exhaust resources.
- Protocol Attacks: Exploit weaknesses in network protocols to disrupt services.
Exploitation of Software Vulnerabilities:
- Buffer Overflows: Craft inputs that exceed buffer limits, allowing execution of arbitrary code.
- SQL Injection: Insert malicious SQL queries into input fields to manipulate databases.
- Cross-Site Scripting (XSS): Inject malicious scripts into web pages viewed by other users.
Use of Exploit Kits:
- Description: Toolkits containing pre-packaged exploits targeting known vulnerabilities.
- Deployment: Often delivered through compromised websites or phishing campaigns.
Credential Dumping:
- Tools: Utilities like Mimikatz to extract plaintext passwords and hashes from memory.
- Techniques: Access Local Security Authority Subsystem Service (LSASS) to retrieve credentials.
Ransomware Implementation:
- Encryption Algorithms: Utilize strong encryption methods (e.g., AES-256) to lock files.
- Persistence Mechanisms: Modify system settings to ensure malware persists after reboots.
- Use of Legitimate Tools for Malicious Purposes:
- PsExec: A Microsoft utility used for executing processes on remote systems, often leveraged by attackers for lateral movement.
- PowerShell: A scripting language used to execute malicious scripts without triggering traditional antivirus defenses.
Recent Attack Analysis
In late 2024, NoName057(16) expanded its operations by forming alliances with various hacktivist groups, enhancing their capabilities and reach. This collaboration led to a series of coordinated attacks targeting multiple sectors, including government agencies and financial institutions.
The attackers employed a combination of DDoS attacks and exploitation of unpatched vulnerabilities to infiltrate systems. Once inside, they utilized tools like Mimikatz to harvest credentials, facilitating further access and data exfiltration. In several instances, ransomware was deployed to encrypt critical data, followed by demands for payment in exchange for decryption keys.
Hacker Groups Identified
NoName05716
- Profile: A pro-Russian hacker group known for DDoS attacks and defacement campaigns. They often target organizations perceived to support Ukraine, NATO countries, or entities opposing Russian interests.
- Alliances: Collaborating with “Black-Hat Zombies,” “UserSec,” and “SPIDER-X.”
- State Links: Likely backed or at least ideologically aligned with Russian state interests. The rhetoric mirrors Russian narratives, e.g., criticizing “the criminal Kiev regime” and targeting Western institutions.
- Tactics: DDoS, website defacement, and collaborative campaigns with other groups.
SPIDER-X:
- Profile: Conducting attacks targeting Israeli government websites, agencies, and private institutions.
- Motivation: Pro-Palestinian and anti-Israel stance. Their attacks are framed as support for Gaza during conflicts with Israel.
- Alliances: Collaborating with groups like “Nation of Saviors” (NOS), “Cyber Team Indonesia,” and NoName05716.
- State Links: Unclear, but the alignment with specific geopolitical causes suggests potential informal backing by sympathetic governments or entities.
Nation of Saviors (NOS):
- Profile: A group focused on targeting entities opposing Palestine or aligned with Israel. It emphasizes a pro-Palestinian agenda.
- Collaborations: Partnering with SPIDER-X for attacks and campaigns.
- Tactics: Website takedowns and defacements, leaking sensitive information.
Cyber Team Indonesia (CTI):
- Profile: A group actively collaborating with SPIDER-X, focusing on empowering communities and “innovation,” though tied to disruptive campaigns.
- Motivation: Likely aligns with the broader ideological goals of its partners, including anti-Western or pro-Palestinian agendas.
Black-Hat Zombies:
- Profile: Mentioned in partnership with NoName05716, seemingly supporting cyber campaigns targeting Ukraine and its allies.
- Tactics: Likely DDoS and breach-based attacks, following NoName05716’s modus operandi.
Motivations and Goals
Geopolitical and Ideological Motivations:
- NoName05716: Aims to undermine Western support for Ukraine and retaliate against countries providing aid to Ukraine. Their rhetoric consistently frames these nations as corrupt or anti-Russian.
- SPIDER-X and NOS: Strongly aligned with the Palestinian cause. Their actions target entities perceived as pro-Israel or complicit in oppression. The framing of their campaigns emphasizes justice and resistance.
- CTI: The collaboration with SPIDER-X suggests alignment with anti-Western or pro-developing world stances.
Goals:
- NoName05716:
- Disrupt Western countries’ operations to signal their vulnerabilities.
- Undermine economic and political stability in regions supporting Ukraine.
- SPIDER-X and NOS:
- Highlight support for Palestine through digital activism.
- Challenge global institutions or governments perceived as Zionist.
- CTI:
- Increase visibility and legitimacy of regional hacking collectives.
- Form global alliances to increase technical capabilities and campaign reach.
Tactics and Strategies:
- Collaboration: Groups form alliances to pool resources, technical knowledge, and amplify impact.
- Multi-Nation Targeting: A focus on high-profile targets (e.g., Israeli and American websites) to draw global attention.
- Propaganda: Use Telegram and other platforms to rally supporters and spread ideological messages.
- Economic Disruption: Targeting financial institutions and infrastructure to weaken perceived adversaries.
Government Involvement
- NoName05716: Likely state-aligned with Russia, given its pro-Russian rhetoric and alignment with Russian geopolitical interests.
- SPIDER-X and NOS: Possible informal support from governments sympathetic to anti-Israel or pro-Palestinian causes, though definitive links are unclear.
- CTI: Likely operates independently but may have tacit state approval in Indonesia due to the alignment of national sentiments with some campaigns.
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.

Leave a Reply